Priorities for servers, apps, and cloud workloads are shifting
Nothing has changed the business and technology world more than the cloud. The cloud has changed the application delivery landscape, and the area that may be most effected of all is the area of security strategies. As businesses move their applications to the cloud, the security fail-safes they’ve relied on for decades – A/V, firewalls, IPS, WAFs and more -- have little to offer in a cloud environment. At the same time, the risks have never been greater.
The concept of a perimeter, where these legacy solutions once contributed, has all but vanished. It’s as though you continue to lock the front door of your house, but now all the windows are left open for any intruder to climb right on in. Hence for the cloud, a completely different mindset is needed. Reputable cloud providers include an array of security functions, but it can’t be assumed that it’s enough to protect enterprise data and applications. As more apps move to the cloud, A/V and signature-based products will become more and more irrelevant. Neil MacDonald from Gartner says, “Signature-based, anti-malware scanning provides little value for most server workloads.”
Endpoint security is not sufficient or even relevant when protecting applications in runtime
Conventional endpoint protection platforms (EPP) claim that they are cloud-ready. Many people assume, and AV vendors often even promote, that conventional signature-based endpoint protection will work on servers hosting applications. But their security systems are designed to protect end-user devices (laptops, desktops, mobile devices). Conventional anti-virus (AV), EPP and endpoint detection and response (EDR) tools can protect personal devices but they are no match for the advanced attacks targeting critical enterprise applications. These vendor solutions are not equipped to protect cloud workloads.
Per Gartner, “Enterprises using EPP offerings designed solely for protecting end-user devices (e.g., desktops, laptops) for server workload protection are putting enterprise data and applications at risk.”
Simon Hunt, vice president and CTO of Endpoint Solutions at McAfee said in 2013, "We are seeing about 150,000 new pieces of malware every day now. The attack is just impossible and we're purely on the defensive. Before we know about any new virus, somebody has to be a sacrificial lamb and die and tell us about it. It's an awful way of doing things*." Now, with memory-based attacks on the scene, conditions are far worse.
Signature-based solutions are inadequate
The reason signature-based solutions fail is because they are too cumbersome, slow and intrusive to be effective in securing high-volume app servers. The types of attacks bad actors use to target applications utilize techniques legacy solutions can’t see or address. Applications inherently have vulnerabilities attackers can exploit. They can inject malicious code - a fileless attack technique that easily bypasses conventional security controls - that runs entirely from memory. We’ve seen this played out in real time against companies with devastating results in memory attacks like WannaCry, NotPetya, and Apache Struts. With good reason, these kinds of memory exploits earn the reputation of being nearly indefensible.
Security must travel with your applications
The only way to protect applications from such indefensible attacks is to take a new tact. Because applications in the cloud don’t run the same way they did on-premise, the methods of securing them must change as well. The cloud is dynamic in nature and to be effective, its security models must be equally dynamic. With perimeter security stripped away, that leaves mission-critical applications and data – the crown jewels of any business – exposed to real threats. Rather than expecting applications to remain where perimeter security used to be, security must adapt to automatically deploy and follow your applications wherever they go, wherever they run.
The new security approach must be capable of protecting memory and applications in runtime. Gartner’s latest Market Guide has called Memory Protection a mandatory capability.
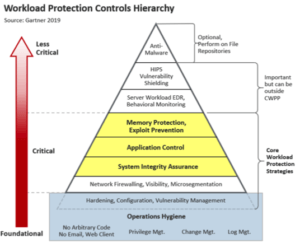
We predict businesses are realizing this fact and will increasingly rely less on A/V and signature-based products. Businesses must look instead to Memory and Process Protection solutions. Those who don’t make this a priority gamble with the threat of malware attacks and landing in the undesirable situation of seeing their names in data breach headlines.
~~~
Further resources:
Solution Brief: Protection Against Advanced Web Attacks
White Paper: Why Web Application Firewalls Are Not Enough
Webinar: Defending Your Business from Attacks that Weaponize at Runtime