The convergence of cloud complexity, dissolution of traditional perimeters, and the dual-edged effect of artificial intelligence are reshaping vulnerability management for good. For security leaders, the challenge has moved from merely identifying vulnerabilities to managing a continuous, interconnected attack surface that spans from a developer’s first line of code well into production environments.
The sheer number of vulnerabilities makes traditional “patch everything” strategies economically unsustainable, as well as operationally infeasible. We need a new strategic framework to evaluate, select, and integrate vulnerability management tools effectively, with a clear emphasis on vulnerability mitigation.
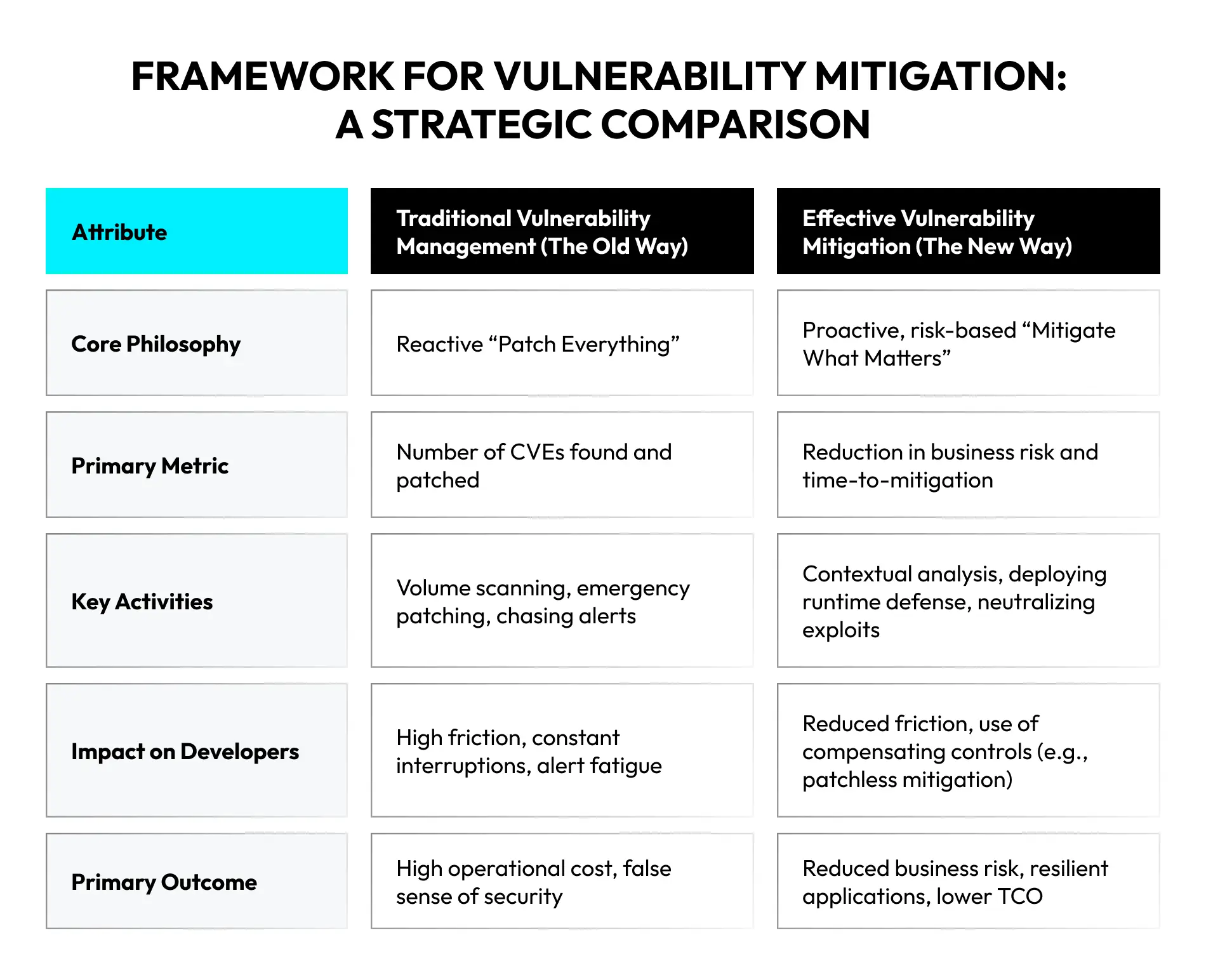
Our analysis depicts one such framework for comparing vulnerability mitigation tools built upon three pillars:
- Technical efficacy and intelligence
- Operational integration and automation
- Business and strategic alignment
This framework is a pivot from static feature comparisons to a new approach that helps assess a tool’s value based on its helpfulness in a specific context. It provides a durable methodology for designing a resilient, efficient, and business-aligned vulnerability mitigation process.
A Modern Taxonomy of Vulnerability Management Tools
We categorize security solutions by their primary function into five complementary categories:
- Code security (pre-production): Identify vulnerabilities before deployment via SAST (static application security testing), SCA (software composition analysis), and IaC (infrastructure as code) scanning.
- Application and API testing (pre- and post-production): Test running applications for behavioral flaws using DAST (dynamic application security testing) and IAST (interactive application security testing).
- External posture and asset management (continuous): Provide an adversary’s view of the internet-facing footprint using ASM (attack surface management), a core component of modern exposure management. This is a key part of the modern debate around exposure management vs. vulnerability management.
- Runtime defense (production): Actively protect live applications and workloads via tools like WAFs (web application firewalls) and RASP (runtime application self-protection).
- Foundational hygiene and response (continuous): Encompass the core processes of identifying and remediating known flaws through vulnerability management and patch management.
The 3 Core Evaluation Pillars for Effective Procurement
Selecting the right vulnerability mitigation tools requires a multi-dimensional evaluation. This evaluation must factor in and balance technical capability, operational feasibility, and business alignment.
- Pillar 1: Technical efficacy and intelligence: Assesses a tool’s ability to find high-impact risks accurately. That involves minimizing false positives, covering the organization’s technology stack, and providing context-aware risk prioritization beyond static CVSS scores.
- Pillar 2: Operational integration and automation: Evaluates how effectively a tool embeds into existing workflows. For instance, it must integrate seamlessly into your existing tool stack and pipelines to avoid creating friction and becoming shelfware.
- Pillar 3: Business and strategic alignment: Analyzes the security solution’s alignment with business goals. This includes its TCO (total cost of ownership), ability to scale without performance degradation, and capacity to generate compliance and executive-level reports
Representative Tools Within the Framework
This section highlights representative vendors that exemplify the function of their respective categories.
Code Security
- Checkmarx: High-accuracy, unified platform for SAST, SCA, and more.
- Veracode: AI-assisted remediation and proprietary vulnerability database.
- Snyk: Developer-first experience with strong workflow integration.
- Mend.io: Leader in automated dependency remediation.
Application and API Testing
- Invicti (Netsparker): Enterprise DAST with proof-based scanning to eliminate false positives.
- Contrast Security: Pioneer in the IAST market, using runtime instrumentation for high-accuracy results.
External Posture and Asset Management
- UpGuard: Leading ASM and third-party risk management platform.
- Bitsight: Combines asset discovery with real-time cyber threat intelligence.
Runtime Defense
- Cloudflare: Leading WAF with a massive global network for threat intelligence.
- Imperva: WAF leader with advanced bot protection and API security.
- Approov: Dynamic RASP focused on securing mobile apps and their APIs.
- Virsec’s OTTOGUARD.AI: Advanced runtime protection providing autonomous, patchless mitigation for workloads.
Foundational Hygiene and Response
- Tenable: Vulnerability management leader with risk-based VPR prioritization.
- Qualys: Cloud-native VMDR platform for detection and response.
- NinjaOne: Unified IT platform with robust, automated patch management.
- ManageEngine: All-in-one patching for Windows, macOS, Linux, and third-party apps.
Applying the Framework to OTTOGUARD.AI
Runtime is the “robbing the vault” phase. It is when an application’s code is actually running on a server or endpoint and when adversaries do the actual damage. The malicious actions, such as encrypting files in a ransomware attack, stealing data, or disrupting services, are all processes that must execute on a live system.
Consequently, while all layers are important, the runtime defense layer is where active protection against exploitation occurs.
Placement in the Taxonomy: Advanced Runtime Defense
OTTOGUARD.AI fits into the runtime defense (production) category. Its core offering is not about scanning code before it runs or managing a list of CVEs. Instead, its entire focus is on protecting live, running applications and workloads from being exploited.
OTTOGUARD.AI integrates into the application’s environment to monitor its execution. By understanding the application’s correct structure and operations, it can detect and block deviations that point to an attack, including a zero-day exploit.
This autonomous workload patchless mitigation model reframes vulnerability management from the ground up. While standard vulnerability management revolves around patching and remediating known vulnerabilities, the goal here is to make the act of exploitation impracticable, thereby neutralizing the threat even if the underlying vulnerable code remains unpatched.
Analysis Against the Core Evaluation Pillars
Pillar 1: Technical Efficacy and Intelligence
- Accuracy and noise reduction: OTTOGUARD.AI provides deterministic and application-aware protection, which directly addresses the framework’s emphasis on minimizing false positives. By mapping an application’s legitimate execution flow, it blocks deviations, contrasting with probabilistic or signature-based methods that can easily lead to alert fatigue.
- Contextual risk prioritization: The platform offers a different approach to prioritization. Instead of focusing on a list of CVEs, workload patchless mitigation aims to render the majority of those vulnerabilities non-exploitable. This trait aligns with the strategic need to handle the overwhelming volume of vulnerabilities by focusing on genuine business risks.
- Coverage and depth: OTTOGUARD.AI’s capabilities extend to protecting legacy software and third-party applications where patching is difficult, addressing a common coverage gap. Also, the ability to block zero-day exploits addresses the need for advanced, consistent, and high-fidelity defense.
Pillar 2: Operational Integration and Automation
- Developer experience and workflow integration: The patchless aspect is a key strength. It directly addresses the framework’s concern that security tools creating friction for developers become shelfware. By providing a compensating control that protects applications in production, it alleviates the pressure on developers for emergency patching, reducing friction.
- Automation capabilities: As an autonomous platform, OTTOGUARD.AI delivers defense that does not require constant manual intervention for rule-tuning, aligning with the need for reducing manual effort and filling the current workforce shortage.
Pillar 3: Business and Strategic Alignment
- TCO: Effective vulnerability mitigation must consider the total cost of ownership. Workload patchless mitigation lowers TCO by decreasing operational costs from emergency patching, downtime, and manual alert investigation. Protecting legacy systems also extends their usable life, avoiding costly re-architecture.
- Compliance and reporting: For regulations requiring vulnerabilities to be addressed promptly, OTTOGUARD.AI serves as a powerful compensating control that helps organizations maintain compliance when patching is not feasible.
- Scalability and performance: As a runtime solution, its ability to scale with growing workloads without degrading application performance is a critical evaluation point.
Strategic Imperatives and Conclusion
Given the expansion of the attack surface and the accelerating threat velocity enabled by technological developments like GenAI, yesterday’s security approaches are now flip phones in a smartphone world. The current cyber terrain and the path forward demand a strategic re-evaluation of technology and approach.
The framework we presented here provides a robust foundation for performing this re-evaluation. A successful security leader of 2025 will be one who masterfully applies the principles of this framework, championing a mitigation-centric approach to reducing security risk.
FAQS
Modern platforms provide layered capabilities across the entire “code-to-cloud” lifecycle, from identifying flaws in pre-production code to actively protecting live applications at runtime.
Yes, advanced mitigation tools serve as a powerful compensating control to help organizations maintain compliance and prove due diligence, especially when prompt patching isn’t possible, which is most cases.
Organizations can neutralize threats through advanced techniques like patchless mitigation, which block exploits even on unpatchable systems, such as legacy software.




