This article explores both attack surface management and vulnerability management, detailing their scopes, methodologies, and the tools used within each one. It discusses the nature of their relationship and offers insights into why and how understanding their distinction can affect your exposure management strategy.
What Is the Difference Between Attack Surface Management and Vulnerability Management?
Attack surface management (ASM) and vulnerability management (VM) are indeed separate disciplines; yet, in reality, they are often confused with each other.
Why Are Attack Surface Management and Vulnerability Management Confused?
The perplexity springs from the following factors:
- Overlapping goals: Both attack surface management and vulnerability management strive to reduce security risk by discovering and addressing security weaknesses, which makes them key to effective exposure management.
- Shared terminology: Both deal with vulnerabilities.
- Scanning as a common activity: Both involve scanning, but the term “scanning” can mean somewhat different things in varied contexts.
- Vulnerability management is a subset or component of attack surface management: This hierarchical relationship can lead to the impression that VM and ASM are the same thing.
- Vendors offering both or integrated solutions: Cybersecurity companies now offer solutions that include both VM and ASM capabilities or integrate them both into one product. This convergence can often blur the lines, as a single platform can perform functions associated with both disciplines.
- Cybersecurity landscape evolution: Attack surface management is a new category that emerged as organizations’ digital footprints started expanding with cloud adoption, SaaS, and remote work. It was a new, modern way to address the new realities, which were beyond the coverage of traditional vulnerability management. However, since we need time to catch up with the fast-paced changes in our industry, as well as the terminology reflecting those changes, we view them as the same reality.
Attack Surface Management
However, attack surface management and vulnerability management are not identical.
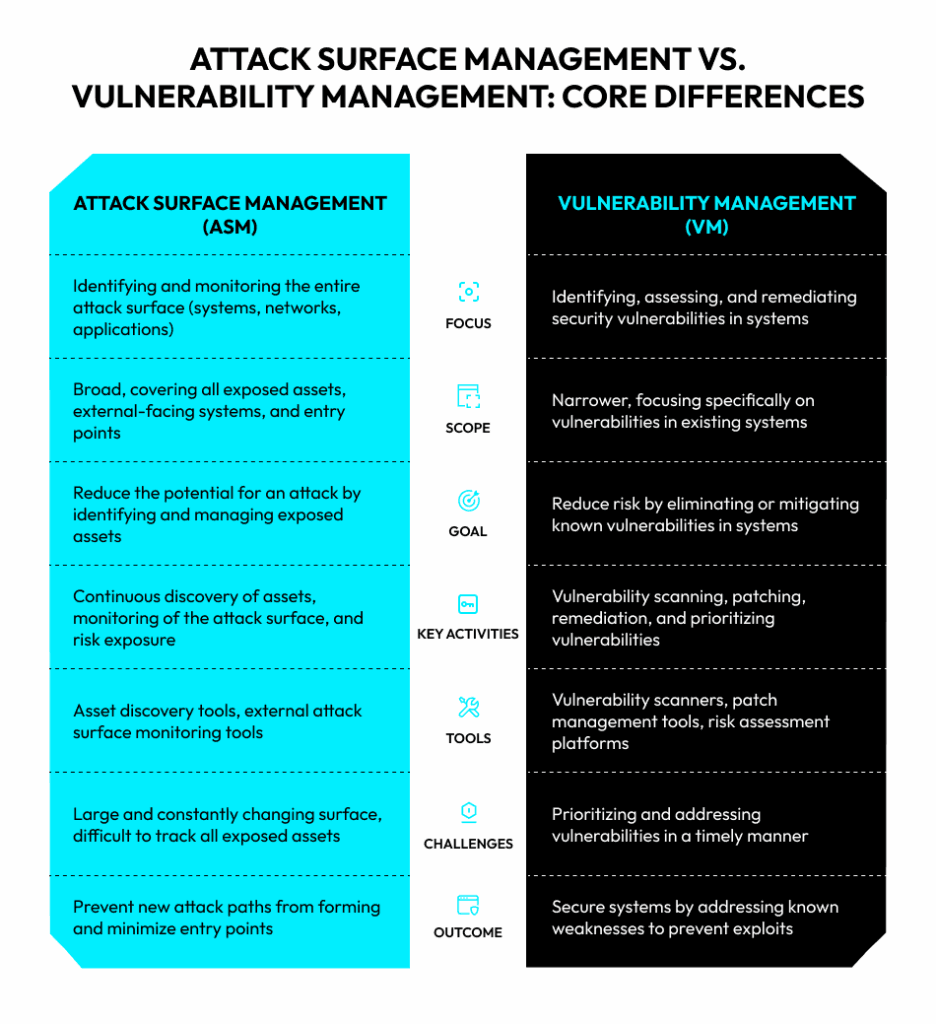
Attack surface management is a continuous, attacker-centric process of discovering, inventorying, classifying, and prioritizing an organization’s digital assets and their potential exposure primarily from an external perspective.
It begins with the understanding of what adversaries see and how they can get in.
ASM Scope
ASM’s scope is broad and external. It is concerned with all digital assets exposed to the internet, including those the organization may not even know about, such as shadow IT or dormant assets. That includes:
- Public-facing websites and web applications
- Cloud services and storage buckets
- APIs
- Domain names and DNS records
- Public code repositories in GitHub or GitLab
- Third-party integrations and software supply chain risks
- Employee-owned devices connected to the network
ASM Focus
Attack surface management is all about discovery and exposure. It aims to answer the question: “What parts of my organization are visible and accessible to an attacker?” That often means finding “invisible assets”—assets that were spun up without IT’s or the general organization’s knowledge, forgotten test environments, or misconfigured cloud instances.
ASM Methodology
ASM uses techniques like OSINT (open-source intelligence), internet-wide scanning, and reconnaissance. It can also leverage attacker methodologies to mimic actual threat actors discovering vulnerable assets. In short, it strives to map your entire digital footprint.
ASM Goal
ASM strives to reduce the overall attack surface, which is why many see it as a key component of proactive exposure management. It’s proactive and aims to prevent attacks by making the organization a harder target.
It’s like walking around the outside of your house to look for all the possible ways someone could get in—unlocked windows, open doors, crawl spaces you forgot about, and even the shed with a broken lock in the backyard that you don’t use anymore.
Vulnerability Management
Vulnerability management is the methodical process of discovering, evaluating, prioritizing, and remediating known vulnerabilities within an organization’s identified IT environment.
VM Scope
VM’s scope is much more specific and internal. It focuses on known assets within the organization’s managed IT infrastructure, such as:
- Servers: Windows or Linux
- Workstations: laptops or desktops
- Network devices: routers, switches, or firewalls
- Apps and programs
- Databases
VM Focus
VM concentrates on finding, understanding, and fixing known vulnerabilities, a great majority of which are indexed in CVE. It answers the question: “Are there any known technical flaws in my environment that threat actors can exploit?”
VM Methodology
VM relies on vulnerability scanning tools—like network scanners, application scanners, and agent-based scanners—that compare discovered software versions and configurations against databases of known vulnerabilities, like NVD.
It’s also worth noting that VM revolves around patching as a primary remediation method.
VM Goal
Vulnerability management aims to reduce the risk posed by specific vulnerabilities on known assets, thus contributing to your exposure management efforts. In that sense, it’s reactive to newly discovered vulnerabilities. It can also be part of a regular patching cycle.
Staying with the house analogy, VM is like going inside your house and checking the locks on all of your windows and doors. You also make sure your alarm system is fully functional and your security cameras work as expected. When you find a broken lock on a window you know about, you fix that lock to make sure no burglar exploits this weakness to enter your home.
Are Attack Surface Management and Vulnerability Management Complementary?
This distinction between attack surface management and vulnerability management naturally leads to a pressing question for security leaders as they allocate budgets and resources: “Are ASM and VM mutually exclusive, and, if not, do I really need them both?”
Has Attack Surface Management Replaced Traditional Vulnerability Management?
The answer is straightforward, and it’s a categorical “No.”
ASM has emerged as a critical and complementary partner, representing a more modern approach, an adaptation if you will, in how organizations approach security weaknesses. The relationship is one of enhancement, not substitution.
Think of it as a shift from a purely “inside-out” to a combined “outside-in” and “inside-out” security model:
- Vulnerability management operates from the “inside out,” finding and prioritizing patching within a recognized inventory.
- Attack surface management works from the “outside-in,” mimicking an attacker’s perspective, mapping an organization’s entire external-facing digital footprint, and discovering all the potential vectors of attack—exposed ports, misconfigured cloud services, and leaked credentials, to name a few—as well as CVE vulnerabilities.
In the modern cybersecurity context, ASM provides the essential, high-level context that makes VM more effective for the holistic tendencies of exposure management. ASM discovers what needs to be protected, and VM then performs an in-depth assessment of the specific vulnerabilities of those discovered assets.
Without ASM, a VM program risks being blind to the threats posed by unknown and unmanaged systems, and without VM, an ASM program may lack depth in addressing particular technical vulnerabilities.
Do You Need Attack Surface Management If You Are Already Doing Vulnerability Management?
Even with a mature vulnerability management program, you still need attack surface management. To risk sounding like a broken record, ASM doesn’t so much replace traditional VM as it acts as its essential complement. It does this by addressing blind spots left by vulnerability management and promising a holistic, attacker-centric view of your digital footprint.
Your VM program excels at identifying and remediating known vulnerabilities within your known and managed assets. It’s like meticulously checking the locks and windows on all the doors and windows you already know exist in your house.
But ASM’s value lies in its ability to discover the unknown, hidden spots in your house, more precisely, the digital assets and exposures that your VM tools don’t see. Why? Because they are not in your inventory or are publicly exposed in ways you haven’t expected.
Besides, since ASM extends beyond purely technical vulnerabilities and CVE, it enables you to protect your organization even from quirky and elusive threat exposures such as API business logic flaws.
How Does ASM Mitigate the Exposures VM Misses?
Attack surface management helps mitigate threats through continuous discovery. VM can only scan assets it knows to exist. If an asset is spun up in a forgotten cloud account, an old domain is repurposed, or an API is exposed inadvertently, vulnerability management remains oblivious.
In contrast, attack surface management actively hunts for these exposures to bring them into your security purview. That’s the only way to make sure you can remediate them.
There may be instances of shadow IT, cloud misconfigurations, or APIs that lack authentication or authorization controls. They can remain hidden with only a vulnerability management program in place, but attack surface management can find them because doing so is precisely why and how it started in the first place—it’s attack surface management’s raison d’être.
Which of the Two Should I Prioritize with a Limited Budget or Headcount?
In case of a limited budget or headcount, prioritizing ASM over VM or vice versa depends on your current risk posture.
If your organization has a rapidly expanding cloud footprint, relies heavily on third-party services, or has a history of unmanaged IT projects, attack surface management is a wiser option.
However, if your IT environment is stable and well-inventoried but you struggle to keep up with patching known vulnerabilities, you’d be better off prioritizing vulnerability management.
Ideally, a phased approach that includes establishing initial ASM visibility to discover major blind spots, followed by integrating a robust VM program to assess and remediate vulnerabilities on all discovered assets continuously, works best.
The most effective cybersecurity strategy integrates ASM and VM, leveraging ASM for comprehensive discovery and external perspective and VM for in-depth analysis and remediation of known weaknesses within the now fully visible environment.
Good to Know: Types of Attack Surface Management and Vulnerability Management Tools
Although a significant overlap now exists between ASM and VM tools, as they adopt each other’s features, their foundational approaches to risk reduction remain distinct.
Vulnerability Management Solutions
Vulnerability management tools methodically scan an organization’s known and managed digital assets by checking them against extensive databases of documented vulnerabilities, most notably CVEs.
The primary goal of a VM tool is to identify specific, known weaknesses and produce prioritized reports that direct IT teams on which patches to apply and where. They are essential for security hygiene within a defined and inventoried IT environment.
Here are the key types of vulnerability management tools:
- Network-based scanners: Analyze the security of network infrastructure like routers, switches, and firewalls.
- Host-based scanners: Assess vulnerabilities on individual machines, such as servers and employee workstations, by examining their configuration and installed software.
- Application scanners (DAST/SAST): Focus specifically on finding flaws in web applications and software code, both in development and in production.
- Database scanners: Scan database management systems looking for code-based flaws (but also weaknesses like misconfigurations, weak passwords, and insecure access controls).
Attack Surface Management Solutions
Attack surface management tools perform continuous discovery of an organization’s overall digital footprint as it appears on the public internet. They are built to find all connected assets, including those that traditional VM scanners miss.
Types of attack surface management tools include:
- External attack surface management (EASM): Focuses exclusively on discovering and monitoring an organization’s internet-facing assets and associated risks.
- Cyber asset attack surface management (CAASM): Aims to provide a holistic view of your assets, both internal and external, by aggregating data from various sources, including VM tools, to identify security gaps and misconfigurations.
- Digital risk protection services (DRPS): Specialize in identifying and mitigating external threats beyond assets, such as brand impersonation, data leakage on the dark web, and social media account takeovers.
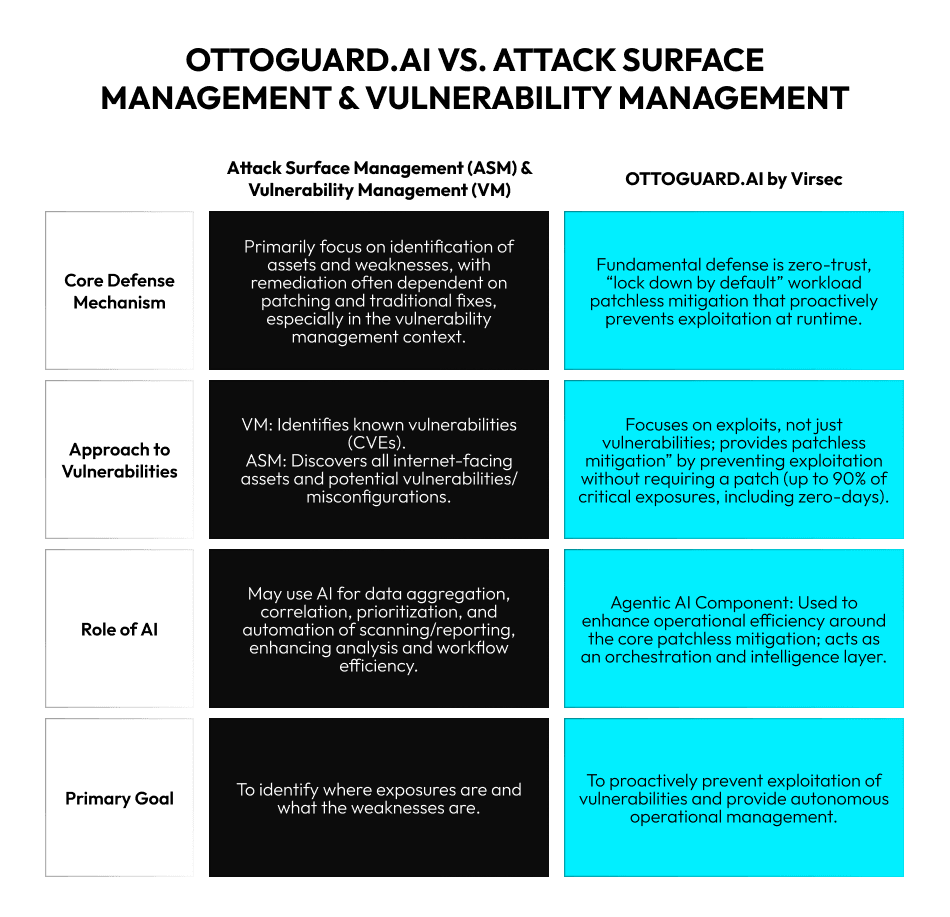
OTTOGUARD.AI: A Skeleton Key
Like a skeleton key that doesn’t belong to any single lock but can open many, OTTOGUARD.AI is neither an attack surface management nor a vulnerability management tool, but applies to both cybersecurity disciplines.
Here is a side-by-side comparison:
Final Thoughts
Attack surface management and vulnerability management do address security weaknesses from distinct vantage points, but they are not mutually exclusive. A good cybersecurity strategy would attempt to integrate them both, using ASM for comprehensive discovery and external insight and VM for in-depth remediation of known technical vulnerabilities.
Stop exploits where ASM and VM leave off.
Book a demo and see how OTTOGUARD.AI provides immediate, workload patchless mitigation to neutralize 90% of your critical exposures right off the bat.
FAQs
Attack surface management and vulnerability management serve as the foundational discovery pillars within a CTEM program, providing the essential data on all external exposures and internal flaws for the subsequent stages of prioritization, validation, and remediation.
You can integrate attack surface management data with your existing vulnerability management tools primarily by using APIs to continuously feed the comprehensive, externally discovered asset inventory from your ASM platform into your VM scanner. That will make sure that your vulnerability assessments cover all known and previously unknown assets for a complete and accurate risk picture.
To measure the effectiveness of your attack surface management, you should use KPIs like:
- Time to discover new assets
- Percentage reduction in shadow IT
- Asset inventory completeness
- Number of critical external exposures
- Reduction in security misconfigurations
- Attack surface risk score
- Number of leaked credentials or secrets
- Mean time to remediate for exposures
- Mean time to triage
- Percentage of exposures remediated within the SLA




