The corporate attack surface is a sprawling, dynamic, and often chaotic frontier of cloud assets, IoT devices, SaaS applications, and legacy systems. For security leaders, the winds have indeed changed, and reactive security measures are no longer defensible. This evolution is settling the exposure management vs. vulnerability management debate, making a proactive and holistic strategy the clear strategic imperative.
But what truly defines an effective exposure management platform in 2025?
This article answers that question with a deliberately unorthodox analysis. We believe a complete exposure management approach requires more than a single category of tool. Therefore, we assess not only foundational scanners like Rapid7, Tenable, and Qualys, but also innovators in endpoint control and remediation like Tanium and Vicarius.
Finally, we will examine a platform that brings the crucial final layer to that program, challenging the conventional discover-and-patch cycle entirely: OTTOGUARD.AI. By delivering deterministic protection to application workloads at runtime, it provides true resilience for the inevitable gaps that even the best strategies leave behind.
The Pillars of Exposure Management: A Comparative Look
The exposure management landscape is vast, with major platforms such as CrowdStrike and Palo Alto Networks offering different capabilities through modules like Falcon Spotlight and Cortex Xpanse.
For this analysis, however, we will focus on a representative set of platforms that highlight key exposure management trends and distinct strategic approaches — from traditional vulnerability assessment pioneers to innovative endpoint control and runtime protection solutions.
The following platforms are important players in the cybersecurity space, each providing essential capabilities for a complete exposure management program. It is worth noting that they are not direct, one-to-one competitors so much as different foundational pillars for security operations.
Tenable: The Pioneer of Predictive Prioritization
Tenable has become synonymous with vulnerability management. Its platform, built around the core Nessus scanner, has grown into a comprehensive exposure management suite.
- Core focus: Tenable’s main forte is its expansive discovery and assessment capabilities. It excels at identifying vulnerabilities, misconfigurations, and other weaknesses across a vast range of assets, including IT, OT (Operational Technology), and cloud infrastructure.
- Role in exposure management: Tenable is essential for the discovery and prioritization stages. Its VPR (vulnerability priority rating) uses machine learning to predict which vulnerabilities are most susceptible to being exploited in the near future. That helps teams cut through the noise of thousands of critical (based on severity score) CVEs to focus on what matters most.
- Key differentiator: The predictive power of VPR and its deep coverage of OT and niche environments make Tenable a go-to for complex, hybrid organizations that need to prioritize remediation efforts with data-backed intelligence.
Rapid7 Insight Platform: Unifying Visibility and Operations
Rapid7 takes a slightly different approach. It integrates its exposure management capabilities (InsightVM) with broader security operations tools for detection and response (InsightIDR) and application security (tCell). Furthermore, it now incorporates an automated patching and remediation function through its Active Patching solution, which is powered by the Automox platform.
- Core focus: Rapid7’s philosophy is to unify visibility. It aims to provide a single pane of glass for understanding risk from the endpoint to the cloud and to connect that risk to real-world threats and active attacks.
- Role in exposure management: Rapid7 is mostly suitable for the discovery, prioritization, and validation stages. Its integration with Metasploit allows for the practical validation of vulnerabilities, helping teams confirm exploitability.
The connection between InsightVM and InsightIDR can help correlate an observed vulnerability with active threat actor behavior, adding powerful context for prioritization. With the integration of automated remediation workflows, its role now extends into the final stage of the vulnerability management lifecycle: remediation.
- Key differentiator: The tight integration of vulnerability management with SIEM/XDR capabilities provides a unique advantage. It bridges the gap between knowing you have an exposure and knowing if someone is actively trying to exploit it, enabling a risk-centric response. In addition,, the new capability allows for a more complete, closed-loop vulnerability management process by automating the patching of identified and prioritized risks.
Qualys Cloud Platform: The Integrated Security and Compliance Powerhouse
Qualys was one of the first to deliver security solutions from the cloud and has built an incredibly broad, integrated platform on that foundation.
- Core focus: Qualys offers a vast array of apps on its Cloud Platform. These applications cover everything from vulnerability management and detection & response (VMDR) to patch management, cloud security (CSPM), and compliance.
- Role in exposure management: Qualys provides strong, native support for the entire CTEM lifecycle, from discovery (with its robust asset inventory) and prioritization (with TruRisk™ scores) all the way to mobilization (with its integrated Patch Management module). This end-to-end capability can be a significant draw.
- Key differentiator: The platform’s breadth and integration are its core strengths. For an organization looking to consolidate vendors and manage security and compliance from a single agent and platform, Qualys presents a compelling, all-in-one vision for exposure management.
Tanium: Real-Time Visibility and Control at Scale
Tanium approaches the exposure problem from a different angle: the endpoint. It was built to provide near real-time visibility and control over millions of endpoints, answering questions and executing changes in seconds.
- Core focus: Endpoint management and security at massive scale. Tanium can query every endpoint for specific data (e.g., “show me all machines with this unpatched software”) and get answers back almost instantly.
- Role in exposure management: Tanium is a powerhouse in the discovery and mobilization stages. Its unparalleled speed in identifying assets and their state makes it invaluable for discovery. More importantly, its ability to deploy patches, change configurations, or kill processes across the entire enterprise in seconds makes it a great remediation and mobilization tool.
- Key differentiator: Speed and control at scale. While other platforms identify what needs to be fixed, Tanium excels at doing the fixing, noticeably reducing the time between detection and remediation for known vulnerabilities.
Vicarius: A Modern Approach to Prioritization and Fixing
Vicarius represents a modern, focused approach to vulnerability management, designed to automate and streamline the remediation process.
- Core focus: Vicarius is laser-focused on prioritizing vulnerabilities based on asset context and threat analysis. Building upon those two, it then provides flexible remediation options, most notably patchless protection.
- Role in exposure management: Vicarius squarely targets the prioritization and mobilization stages, but with a novel twist. Its vRX product analyzes vulnerabilities and provides scripts to eliminate the risk without waiting for an official vendor patch. This digital vaccine can be a lifesaver when patches are unavailable or difficult to deploy.
- Key differentiator: Patchless protection — the ability to neutralize a vulnerability by securing the application’s memory or blocking a specific function, rather than applying a full binary patch. This is a powerful tool for reducing exposure quickly and with minimal operational disruption.
The Final Layer: Introducing OTTOGUARD.AI and Workload Patchless Mitigation
The platforms above are essential. They find the holes in the ship and help you patch them. But they all operate on a fundamental premise: You must first know about a vulnerability to fix it. That leaves critical gaps:
- The zero-day problem: What about the exposures that haven’t been discovered yet?
- The patching gap: What about the weeks or months it takes to test and deploy a patch, even for a known vulnerability?
- The legacy gap: What about the unpatchable EOL (end-of-life) software and systems?
With these gaps in mind, the conventional threat exposure management script requires a fundamental change — from patching, prioritization, and scanning to mitigation-first protection. And that’s OTTOGUARD.AI’s domain.
Runtime Mitigation for Unpatched Workloads
OTTOGUARD.AI is not a vulnerability scanner. It doesn’t compete on who can find the most CVEs. Instead, it assumes that despite your best efforts, some exploits will eventually reach your critical applications. Its mission is to stop the exploit from executing, regardless of whether the vulnerability was known or unknown.
- Core focus: Application-aware runtime protection based on patented deterministic zero-trust technology and supplemented by agentic AI security functionality. OTTOGUARD.AI maps the known-good DNA of an application, its files, libraries, processes, and acceptable execution flows. And it immediately stops any deviation from this map.
- Role in exposure management: While so many solutions mobilize a patch, OTTOGUARD.AI mobilizes a deterministic guardrail. It effectively makes exposures and vulnerabilities non-exploitable at the most critical moment — during the attack execution. With its compensating controls, it operates as a safety net for your entire exposure management program.
How OTTOGUARD.AI Supports The Entire Exposure Management Strategy
OTTOGUARD.AI integrates with your existing tool stack to contribute to a more resilient and effective exposure management strategy:
- Neutralize the exploit technique: The reason this platform delivers effective protection against zero-day exploits is that its core defense doesn’t rely on signatures or threat intelligence. OTTOGUARD.AI protects against the technique of the exploit (for instance, remote code execution or memory corruption) by making sure your application only does what it’s supposed to do. This approach can be equally effective against both known exposures and zero-day threats.
- Make prioritization consistent, systematic, and manageable: OTTOGUARD.AI’s workload patchless mitigation gives you much-needed breathing room, letting you follow a strategic patching cadence based on operational risk, rather than reacting frantically to every new critical CVE. That substantially minimizes the risk of a breach from unpatched vulnerabilities.
- Secure the unpatchable: For legacy systems, OT environments, or embedded software where patching is impossible or impractical, the platform minimizes the possibility of a successful cyberattack targeting all-too-familiar critical exposures.
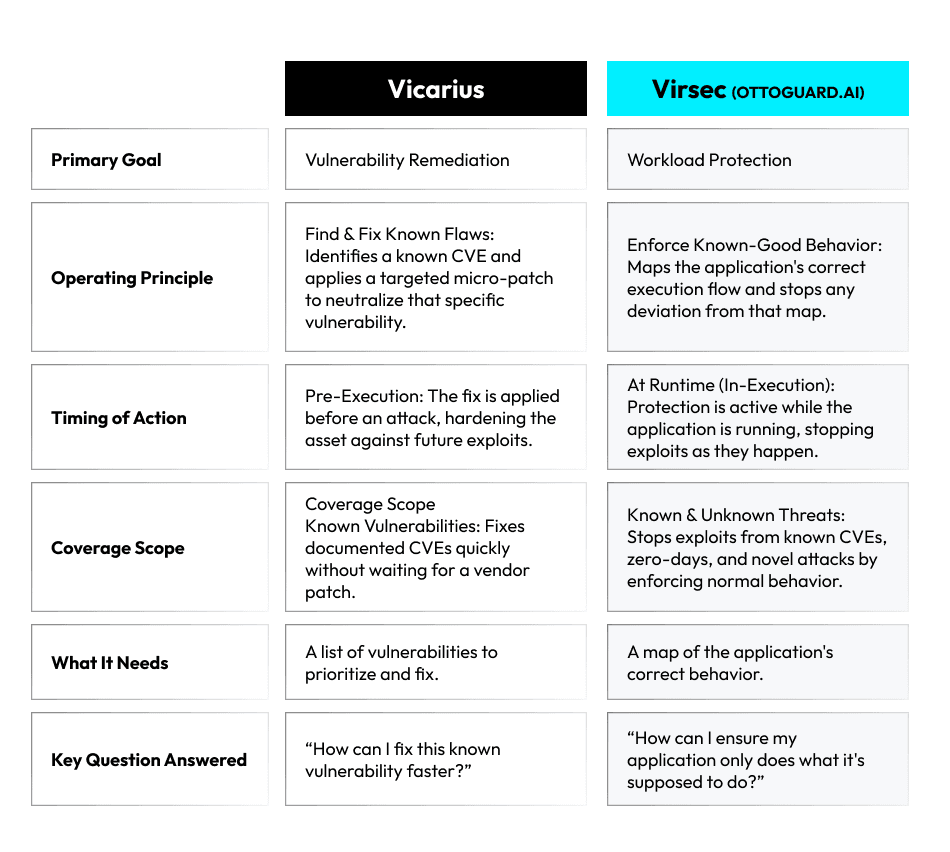
Distinguishing Patchless Approaches: Vicarius vs. OTTOGUARD.AI
Both Vicarius and OTTOGUARD.AI offer patchless protection. The question arises, then, how do they differ?
This table breaks down their key functional differences:
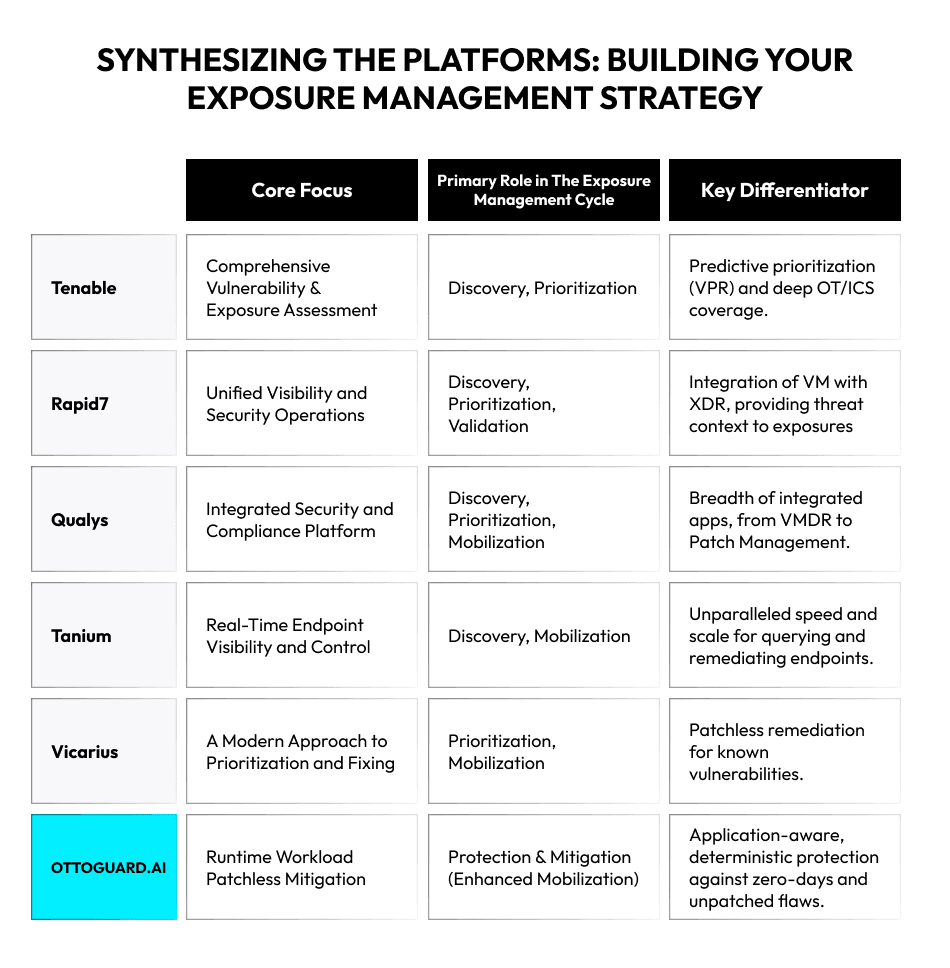
Synthesizing the Platforms: Building Your Exposure Management Strategy
Conclusion
The best exposure management platforms of 2025 are not a monolith. An effective strategy is not about choosing Tenable or Rapid7, or Qualys. It’s about leveraging their strengths to build a comprehensive program that can discover, prioritize, and mobilize against threats. Tanium provides the speed to act, and Vicarius offers innovative ways to remediate.
However, even the most perfect execution of this cycle leaves you exposed. The time between discovery and remediation is the window of opportunity for attackers. OTTOGUARD.AI operates in that window.
It delivers a powerful conclusion to the exposure management story. It doesn’t replace the need for vulnerability discovery and patching, but it provides crucial exposure mitigation mechanisms that make sure your environment remains safe even when an exposure is missed or a patch is delayed.
Book a demo: Discover how OTTOGUARD.AI protects your unpatched workloads at runtime.
FAQs
Look for platforms that offer comprehensive asset discovery, risk-based prioritization, integrated remediation, and a mitigation-first approach to protection.
No, focusing only on CVSS scores is insufficient because this approach ignores the crucial context of business criticality and real-world exploitability data needed to identify true risk.
Since exposure management consists of distinct stages, like discovery and remediation, organizations often build a more resilient program by integrating multiple specialized platforms that excel at each specific function.
The exposure management vs. autonomous exposure mitigation discussion comes down to these two ideas:
- Exposure management is the complete strategic program for handling the entire attack surface.
- Autonomous exposure mitigation is an advanced capability within that program where a tool automatically neutralizes threats in real time without human intervention.




