The ongoing attacks on Microsoft Exchange servers by the Hafnium cyber espionage group appear to be escalating, and potentially impacting a wider range of organizations than even the massive SolarWinds attack. While SolarWinds potentially put their 18,000 customers at risk, the Exchange attacks have reportedly impacted more than 30,000 organizations in over 100 countries. Regardless of size, Hafnium and SolarWinds have a lot in common – they both started with email servers, used multi-step attack kill chains, deployed fileless malware, and used remote code execution (RCE) techniques that bypass most conventional security tools. And both attacks benefited from massive dwell time – with attackers opening persistent backdoors and roaming undetected in thousands of networks for many months.
As part of our commitment to protecting against these attacks, first it’s always critical to understand what happened. The Virsec Security Lab continuously analyzes new vulnerabilities, major attacks, and hacking techniques. But they also go beyond analyzing and build test exploits based on available knowledge, published content, and their own engineering skills. These are used to both recreate attack scenarios and test Virsec’s defenses against both known and unknown vulnerabilities. In the case of SolarWinds, our team built a unique version of the Sunburst attack in only 16 man hours of work. This fact challenges recent security industry testimony during Senate hearings (see our blog) that building the SolarWinds attacks required thousands of hours from armies of well-trained, nation-state-sponsored hackers – implying that these attacks are rare. There certainly are armies of hackers, but we believe they are creating tens of thousands of unique variants with relative ease and speed.
A couple of caveats on our process:
With any attack, there is some speculation about what occurred, and changing storylines as details emerge. Our team combines the best available information, expert opinions, and our own experience to simulate how these attacks likely occurred. When new information becomes available, we will always try to update our analysis.
-
We use publicly available tools, and our own knowledge base to build exploits that simulate what likely occurred in these attacks.
-
We build unique versions of attacks that are not cataloged in AV signature databases (it’s easy to stop a known piece of malware…)
-
We do not publish our hacking tools but can make them available to customers under NDA to test their own applications and security systems.
Here’s our analysis of how the Hafnium-Exchange attacks were likely perpetrated. See the diagram below, and you can also view our Video Analysis for a detailed discussion.
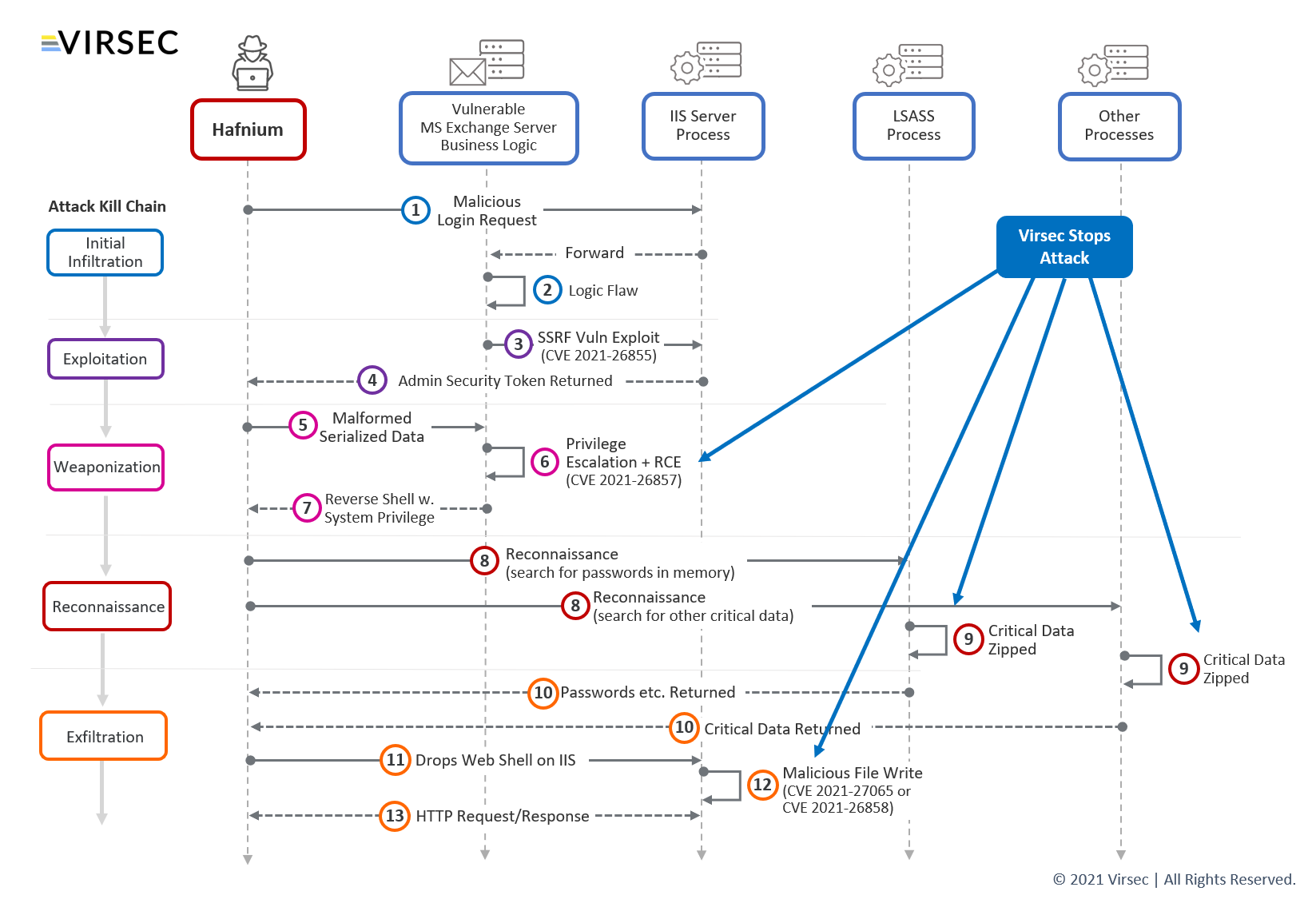
In early March, seven new MS Exchange vulnerabilities were exposed. Three had been previously identified, but the other four were unknown Zero-Day. Apparently, the Hafnium group has been exploiting these for some time.
The attack starts with a crafted malicious login request (1) which takes advantage of a flaw in the Exchange server logic (2) to launch a Server-Side Request Forgery (SSRF) attack (3) using vulnerability CVE-2021-26855.
As part of this flaw, the Exchange server returns an Admin Security Token (4), enabling the attackers to login with admin privileges.
Next, the attacker sends specially-crafted, malformed serialized data (5), which exploits another Exchange vulnerability – CVE-2021-26857 (6). Embedded in that is malware that can run Remote Code Execution (RCE) which allows further privilege escalation. From here, the attacker can establish a Reverse Shell (7) with full system privileges.
For the next step, the attacker sets up a Reverse Shell to do Reconnaissance (8) on other server components, looking for passwords, usernames, or other critical data, which gets Zipped (9) and returned to the hackers (10).
Now with full system privileges, the hacker can drop a Web Shell (11) on the IIS server, and gain full remote command over the server. Additional vulnerabilities were exploited to allow malicious file writes – CVE-2021-27065 and CVE-2021-26858 (12). Finally, using HTTP requests and responses (13) the attackers can easily exfiltrate data from the system.
The severity of having an organization’s Exchange server compromised may seem obvious, but bears stating. Email is the communication lifeblood of many organizations and contains enormous amounts of sensitive data, private information, and intellectual property. To have this compromised can have enormous negative consequences.
Fortunately, Virsec can stop these advanced cyberattacks at multiple points in the Kill Chain, interrupting them at the earliest possible point, and eliminating dwell time. Crucially, Virsec stops these attacks without prior knowledge, regardless of whether a vulnerability is known, zero-day, and has yet to be discovered.
At Virsec, we believe a new approach is needed to break this vicious cycle of cyberattacks that have clearly outpaced our current security defenses. Rather than endlessly chasing threats and trying to react as quickly as possible (which in both SolarWinds and Hafnium was weeks to months to years to never…), our approach is to apply a Zero Trust model to protecting critical application workloads during runtime. Essentially, instead of trying to stop everything ‘bad’ – an endless, infinite problem, Virsec focuses on providing deep application-awareness, runtime protection, and full automation to ensure ‘good’ – making sure critical systems only execute as intended and never go off the rails.
Gartner states this need succinctly in their Market Guide for Cloud Workload Protection: “At runtime, replace antivirus-centric strategies with “zero-trust execution.””