What is cybersecurity exposure management? What does the term “exposures” even mean? How many phases does effective exposure management consist of? What strategies and advanced techniques can US organizations implement to reduce exposure successfully? Read on and discover the answers to these questions and more.
Introduction to Exposure Management
We can trace the official beginnings of exposure management back to Gartner’s 2022 research. It’s been only a few years since then, but exposure management is already one of the most discussed and trending topics in cybersecurity, with its prominence only expected to grow.
Unlike old threat management, which was reacting to known flaws, exposure management takes a proactive and continuous approach. Its mission is to systematically identify, assess, prioritize, and remediate the security weaknesses, that is, exposures, in your organization’s entire digital environment, with its focus shifting more toward prevention.
These exposures extend beyond vulnerabilities in the typical CVE sense to include:
- Misconfigurations: open ports, default credentials, verbose error messages, public storage accounts, debugging features in production, and more.
- Identity flaws: guessable passwords, orphaned accounts, exposed session IDs, decentralized identity management, and similar.
- Software supply chain risks: compromised open-source libraries and dependencies, compromised CI/CD pipelines, hijacked software distribution channels, compromised developer accounts, subpar third-party vendor security practices, etc.
- Cloud environment weaknesses: AWS Security Groups or Azure Network Security Groups left open, shadow IT, poor data classification, compromised container images, and others.
- Security control gaps: lack of MFA on critical accounts, poor incident response plan, missing formal patch management program, no security awareness training, and more.
As a modern practice for addressing modern security phenomena, exposure management views exposures through the lens of how malicious actors might chain them together to achieve their objectives.
For organizations operating in the territory of the United States, the convergence of regulatory scrutiny (e.g., the SEC cybersecurity disclosure rules), technological changes (e.g., cloud adoption and AI integration), and geopolitical dynamics (e.g., state-sponsored attacks and cyber warfare) vastly increase the need for a holistic cybersecurity strategy built upon exposure management.
By deeply understanding the actual threat terrain and focusing resources on the exposures that pose the greatest risk, organizations can build cyber resilience and real-time protection that secure operational and business continuity.
The Key Components of Effective Exposure Management
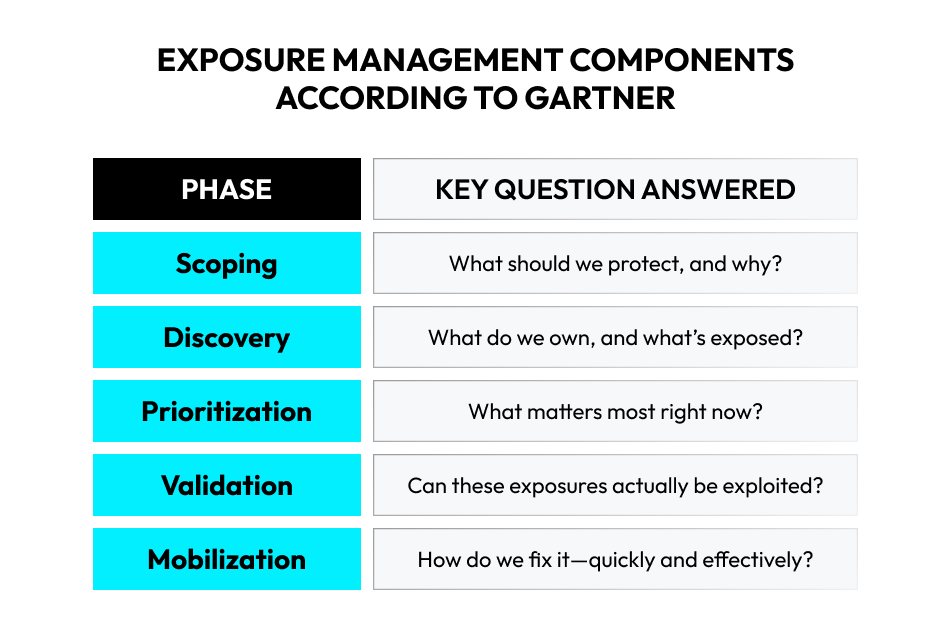
Exposure management isn’t a one-off project. It’s a continuous process to help you first understand and then reduce your cyber risk. Specific implementations can vary from organization to organization. Nevertheless, the key elements generally align with a cyclical approach, often exemplified by Gartner’s CTEM (continuous threat exposure management) framework.
Here, we stick to the names of Gartner’s five key components.
1. Scoping
Goal: Define precisely what you should protect, as well as the limits of your analysis.
- Identify critical systems, data, applications, and environments.
- Clarify organizational goals, such as reducing the external attack surface, protecting crown-jewel assets, or securing CI/CD pipelines.
- Establish with stakeholders what constitutes unacceptable risk and acceptable exposure.
- Specify the scope across on-prem, cloud, hybrid, and third-party environments.
Why it matters: Without a clear scoping, exposure management efforts tend to become too broad or, worse, not aligned with business risk.
2. Discovery
Goal: Gain full visibility into assets, users, and potential exposures.
- Continually inventory all assets: devices, cloud workloads, APIs, data flows, SaaS, containers.
- Map internal and external attack surfaces, including shadow IT.
- Use asset discovery tools to spot unmanaged resources.
Why it matters: You can’t reduce what you can’t see. Discovery ensures unknown exposures don’t blindside you.
3. Prioritization
Goal: Focus efforts on what is most exploitable or impactful.
- Combine threat intelligence (e.g., information about known exploited vulnerabilities or KEVs) with vulnerability data and asset criticality.
- Use contextual frameworks, like MITRE ATT&CK, to understand how exposures map to attacker behavior.
- Score and rank exposures not just by severity (CVSS) but by vertical relevance, business impact, and the likelihood of exploitation.
Why it matters: Prioritization filters out noise and ensures security teams focus on the right exposures, before attackers find and exploit them.
4. Validation
Goal: Simulate and confirm the real-world exploitability of exposures.
- Use offensive security—penetration testing, breach and attack simulation (BAS), or red teaming—to test your security controls.
- Validate whether prioritized exposures indeed lead to compromise to avoid wasted effort on false positives.
- Identify multi-step attack paths and privilege escalation possibilities.
Why it matters: It’s one thing to know something is exposed, but it’s another to prove that it’s exploitable in your particular environment.
5. Mobilization
Goal: Apply remediation/mitigation across teams and processes.
- Assign exposures to the right asset owners, whether it is IT, DevOps, cloud engineers, or someone else.
- Track time-to-remediate and closure rates.
- Build SLAs for critical vulnerabilities and feedback loops to reduce future exposure.
- Apply automation where possible using autonomous mitigation, SOAR, automatic patch deployment, and other tools and methods.
Why it matters: Discovery without follow-through is meaningless. Mobilization ensures that you not only identify but also eliminate exposures.
Smart Strategies for Exposure Management in US Organizations
You can approach exposure management in many ways. Much of your approach will depend on your concrete conditions—the type of organization or business, your industry, the resources at your disposal, or your company’s culture. But it’s always a good idea to receive experience-based recommendations ahead, so here they are.
Leverage Data for Better Decision Making
Leveraging data for better decision-making is a smart, strategic move for US organizations striving to do exposure management properly.
Data analytics has become a pillar for nearly every modern organization, and rightly so. It transcends industry boundaries to empower better decision-making, support innovation, and optimize daily operations. It transforms raw, disparate data into meaningful, actionable insights, enabling you to understand past performance, recognize current trends, and sometimes predict future outcomes.
As such, it can become the nervous system of an organization’s effective exposure management program. Today, we face and operate with a deluge of security-relevant data, from vulnerability scan results and configuration details to identity logs and threat intelligence feeds.
Using big data analytics together with AI can only help you identify exposures faster and with a higher exactness, as well as analyze complex attack paths with unprecedented depth. In addition, it can come in handy in predicting future risks.
So, don’t hesitate to use it. It might look like jumping on the bandwagon, but you know you’ll be adopting it for a good reason.
Implement Automation in Risk Management
Automation is instrumental in streamlining the exposure management lifecycle. It drastically improves the speed, accuracy, and scalability with which organizations identify and mitigate security risks. There’s hardly a self-respecting security organization today that won’t tell you that automation is not a choice anymore but an urgent necessity.
The diligent work of creative and seasoned cybersecurity pros remains indispensable. However, consider that we’re currently facing a yawning gap between cybersecurity needs and the available skilled workforce to meet those demands. Besides, manual processes are often error-prone and, more often than not, quite slow.
Imagine automating repetitive tasks such as asset discovery, vulnerability scanning, misconfiguration detection, and data aggregation from disparate security tools. They’re difficult to do right without any additional requirements; picture doing them continuously, as exposure management requires.
With automation, organizations can achieve virtually real-time visibility, mitigation, and response capabilities, especially when fueled by an AI or ML engine. AI agents can autonomously analyze your IT environment, trigger remediation workflows, block the much-feared ransomware attacks in milliseconds, and maintain your system integrity across time.
Promote Collaboration Between Departments and Stakeholders
Cyber exposures can originate from or affect any part of your business: the IT infrastructure, cloud deployments, HR systems, or marketing apps. This implies that siloed cybersecurity is inherently flawed.
An effective exposure management program calls for close coordination among IT, security, legal, compliance, risk management, and business unit leaders. That’s the only way to guarantee a complete approach to your attack surface and a unified response to security risks and cyberattacks.
Stakeholders, including the board of directors and senior management, play a crucial role beyond just oversight. Their support and active engagement are what move your security program in a good direction through allocating the right budget, defining risk appetite, and guaranteeing that exposure management is not implemented only for compliance reasons but as a key business enabler.
Advanced Techniques for Managing Exposure
Although there are at least several highly recommended advanced techniques for managing exposure we can share, to shorten our discussion, we’ll restrict it to three.
Real-Time Risk Monitoring and Adaptive Response
Real-time risk monitoring and adaptive response stem from the markedly proactive orientation of exposure management.
These two advanced techniques send a strong signal: We’ve put periodic assessments behind us and we continuously observe our fluctuating attack surface, ingesting live data streams from diverse security tools, threat intelligence feeds, and business operations.
Real-time monitoring benefits enormously from AI-driven data analytics. As such, it helps you immediately detect anomalous activities, new exposures, attack attempts, and, indirectly, even shifting adversary tendencies.
When the resulting real-time insight is paired with an adaptive response mechanism, enabling automated or semi-automated actions, you’re simply bound to mitigate risks promptly.
Consider how beneficial these two can be to a large financial institution.
Suppose the real-time monitoring capability detects a highly unusual pattern: a series of quick, high-value financial transactions coming from an employee’s account in a division that typically handles low-volume, domestic transfers. At the same time, the monitoring system flags a login from that same employee’s account from a location inconsistent with their usual work patterns and recent travel history.
Instead of generating an alert for analyst review, the adaptive response component kicks in. Within milliseconds:
- It isolates the compromised employee account, temporarily preventing it from initiating further transactions and restricting network access.
- It flags all related transactions for immediate review by the fraud department.
- Only then does it send a high-priority alert to the SOC, providing a detailed account of the detected anomalies and the automated actions taken in response.
- It forces a password reset for the affected account and triggers a prompt for the employee to re-authenticate, using MFA on their usual registered device.
Zero-Trust Technology
Zero trust has switched defenders’ focus from perimeter-based defense to “never trust, always verify”. In general terms, it eliminates implicit trust and requires continuous authentication and authorization for every user, device, and application attempting to access resources.
Zero trust dramatically limits an attacker’s ability to move laterally across a network. Typically, it is accompanied by granular control and strict conformity with the principle of least privilege. This way, it minimizes the impact of a compromised credential or initial breach, which is especially valuable in distributed and highly dynamic environments.
Take as an example a zero-trust implementation resting on the “default-deny, allow-on-trust” principle.
This technology can create a baseline of how, say, an application of yours is supposed to behave at runtime. That includes which processes should run, which memory locations they should access, which system calls they should make, and which files they should interact with.
Say an adversary is attempting to inject malicious code into the application’s memory to alter a transaction amount or exfiltrate data. This technology sees this attempt as a deviation from the authorized baseline and blocks the threat in milliseconds.
It doesn’t have to rely on signatures or prior knowledge of the attack. It can stop the unauthorized action at the earliest possible stage of the attack chain, preventing the malicious code from executing within the application’s memory, regardless of whether it’s trying to exploit a zero-day or a known CVE vulnerability.
Mitigation-First Approach
Adopting a mitigation-first approach in exposure management offers crucial advantages over relying exclusively on long patching cycles, especially considering the current pace of exploitation.
Instead of making your security posture dependent almost entirely on a complex, often delayed patching process, this approach gives precedence to mitigation as a first action in exposure management. Addressing security weaknesses is the central component in exposure management, anyway, so why postpone it and unnecessarily increase the risk of threat actors gaining control over unprotected assets?
A mitigation-first approach reduces overall exploitability, prevents damage, and opens a protective umbrella above the weak links in your environment, such as legacy software. Its point is not for you to discard patching and vulnerability/exposure prioritization altogether. What it aims at is immediate protection, even if it’s only interim until that future update, upgrade, or patch comes into play.
As an illustration, consider a zero-day vulnerability discovered in a widely used web server software. This weakness makes organizations globally susceptible to remote code execution. The vendor announces a full patch, but it won’t be available for several days, and deploying it across hundreds of servers will take weeks.
Instead of waiting for the full patch, you deploy a mitigation-first security solution that blocks attacks in real time. This in itself can be sufficient to reduce the exposure to active exploitation for all affected servers, buying your organization precious time until it can safely and thoroughly deploy the official patch.
Final Thoughts
Moving beyond reactive measures to proactive and continuous strategies and techniques has become essential as well as advantageous. Adopt advanced techniques like real-time risk monitoring, zero-trust technology, and a mitigation-first approach. In addition, use powerful enablers such as data analytics, automation, and cross-departmental collaboration, and you can systematically reduce your organization’s attack surface.
Did you know that Virsec has built a platform, OTTOGUARD.AI, that includes most of the capabilities that you need to do exposure management the right way? Zero trust, AI agents, automation, real-time monitoring, and mitigation first all converge in one platform to protect your server and application workloads, legacy software, and the software supply chain from ransomware and a swarm of adversaries, each seeking a unique way through your defenses.
Book a demo and experience first-hand what it means to do exposure management the right way.
FAQs
Issues including stringent regulatory scrutiny, rapid cloud and GenAI adoption and the flood of vulnerabilities and exposures that US organizations face, make exposure management both a security and business imperative.
Exposure management proactively targets misconfigurations, identity flaws, software supply chain risks, cloud environment weaknesses, and security control gaps, as well as CVE vulnerabilities.
Data analytics, automation fueled by AI, and cross-departmental collaboration, alongside advanced real-time monitoring, zero trust principles, and a mitigation-first approach, can all help US organizations realize effective exposure management.