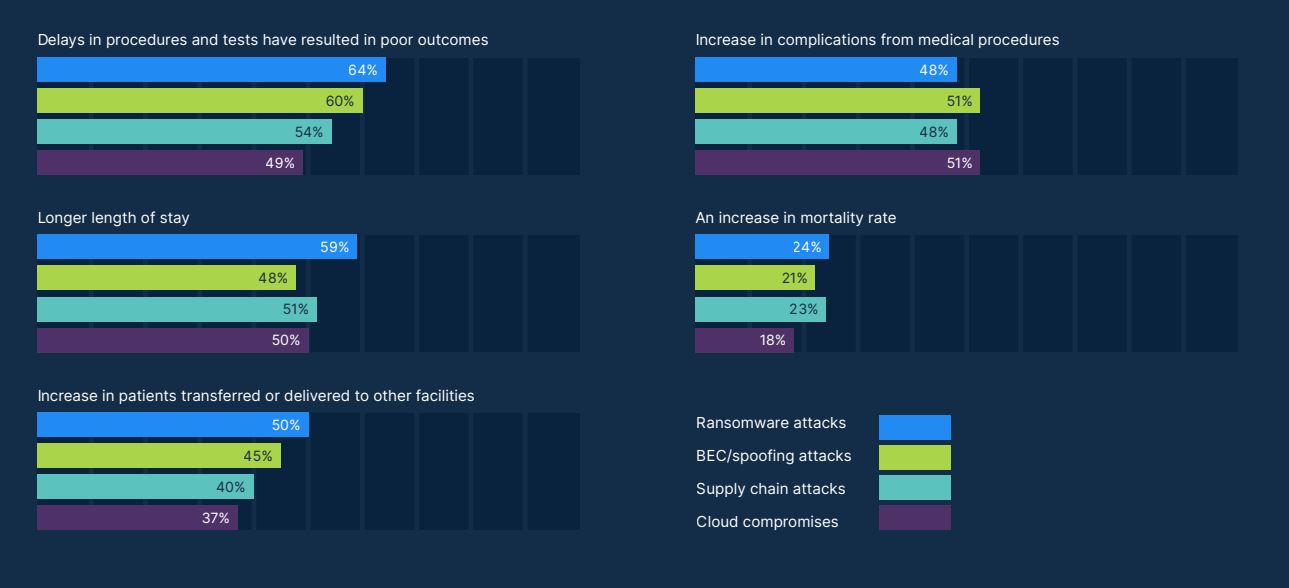
It is no secret that Healthcare Providers are being targeted at an alarming rate by ransomware attacks. Due to the critical nature of health systems, attackers know they are more likely to have their ransom demands met.
Zero-day attacks have become a cause for great concern as unpatched systems are increasingly targeted due to their
high level of vulnerability.
Remote Code Execution (RCE) is another common attack vector used as traditional cybersecurity tools have not been
able to adequately guard against it.
A Verizon Data Breach Investigations Report shows that attacks on servers dominate compared to those on user accounts and client devices. Furthermore, the report also shows that attacks on web application servers outpaces any other asset type.
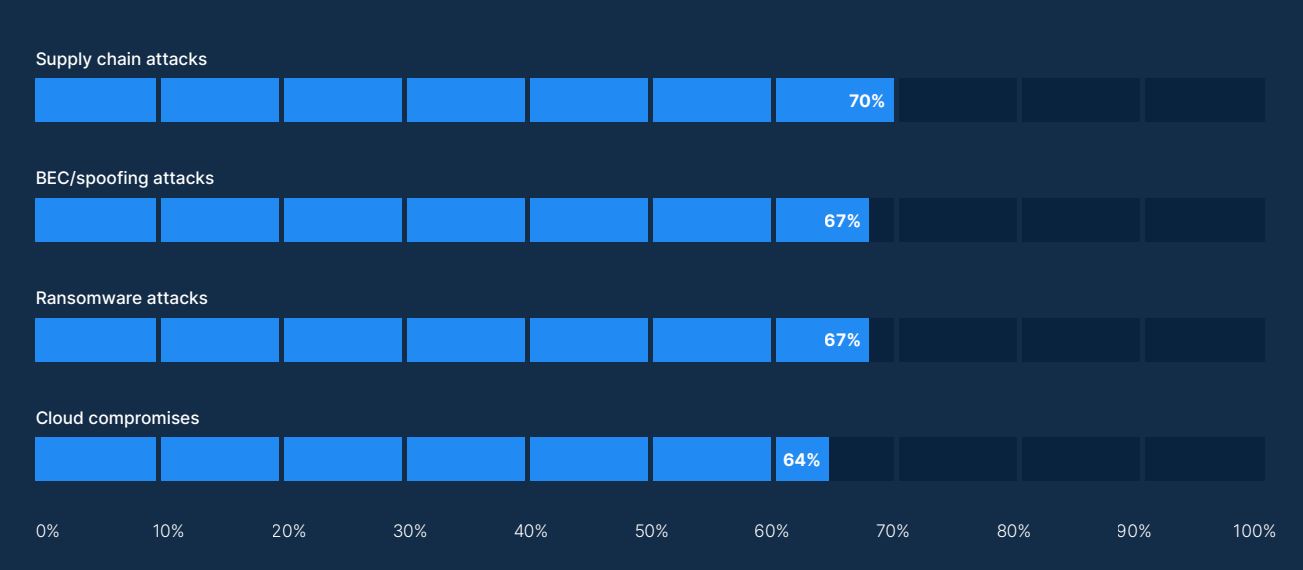
“Ransomware attacks targeting healthcare delivery orgs. doubled from 2016 to 2021.”
2022 Healthcare Cybersecurity Year In Review, Health Sector Cybersecurity Coordination Center (HC3)
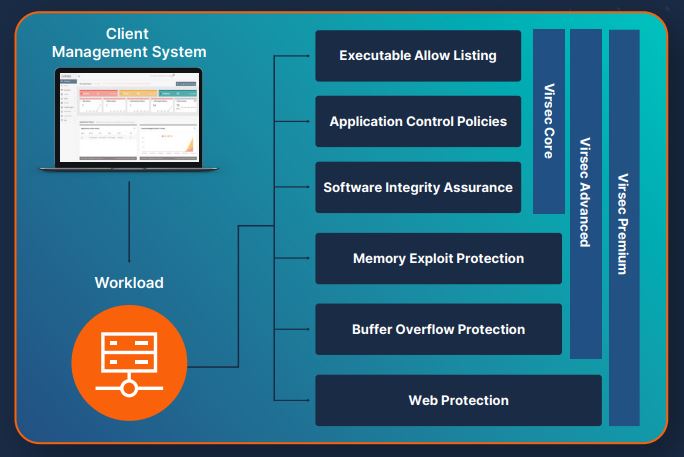
Zero Trust Workload Protection helps to:

Virsec’s groundbreaking approach delivers the highest levels of protection, with zero dwell time and low false positives. Virsec leverages security controls that embrace a modern automated “allow listing” approach — permitting only known good code (executables, libraries, and scripts) to run. All other code is explicitly denied execution — eliminating dwell time and stopping Zero-day attacks before exploitation can occur.
Behavior-based solutions rely on stopping the known bad but struggle with the large set of unknown executables. This “default allow” approach assumes implicit trust (the
opposite of Zero Trust).
Virsec’s approach adopts a “default deny” policy that only allows known good code to execute and stops everything else. That’s true Zero Trust.
100% 0Prevention
42% 8Prevention
Virsec Security Platform
Leading EDR
The speed with which attackers can discover and encrypt systems is putting organizations at even greater risk. According to IBM, ransomware attacks need less than four days to encrypt
systems on average. Furthermore, we have already seen attacks that can compromise data within 30 minutes, e.g. the QBot malware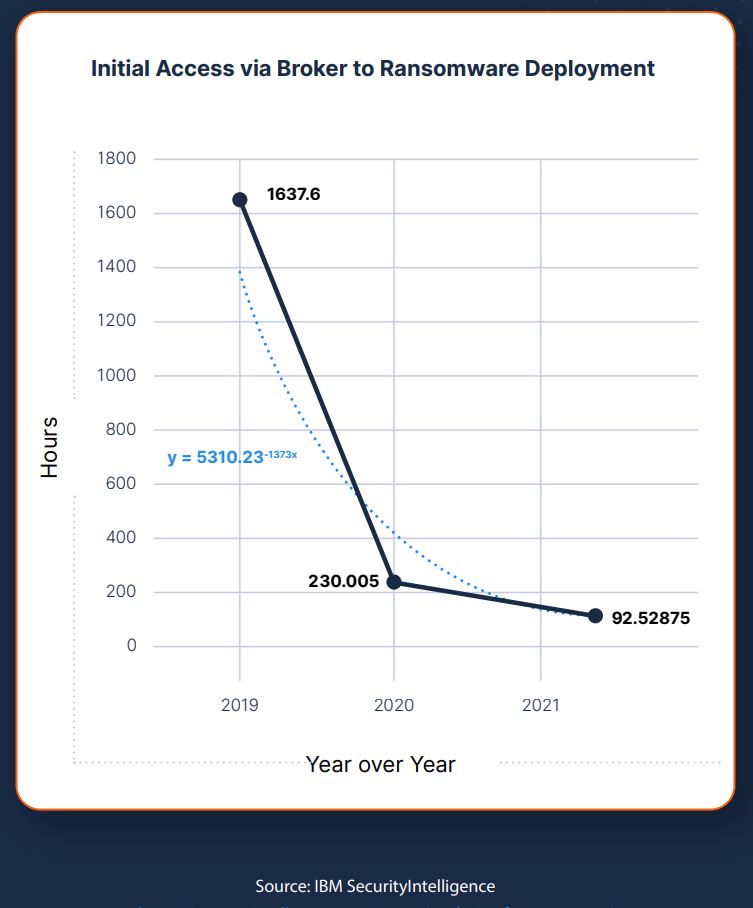
Other solutions that rely on analysis generate so many false positive alerts that it overwhelms teams. With a positive security model and automated allow listing, you can protect legacy systems AND avoid all the alert fatigue.
