Just what we wouldn’t want to hear – that the A/V software we might have in our anti-cyberattack arsenal is itself capable of being the enemy. Not that it’s likely, so there’s no call to rush to deactivate your A/V product or start giving you’re A/V vendor the evil eye. But since being forewarned is forearmed, it’s useful to know how and why A/V software could possibly be used as a spying tool in your system.
To be effective, security software requires privileged access to everything it’s there to protect – close proximity to all applications, programs, browsers, email and files. You wouldn’t put a security guard 4 blocks away from your house or business.
Knowing A/V software is present in nearly every organization’s security product lineup, Patrick Wardle, chief research officer at security company Digita Security and also prior hacker for NSA, became intrigued by the Kaspersky headlines and accusations of using their software to spy so he began to look into the risks.
Specifically, he was curious about the claims that Russians had used Kaspersky products to extract classified files off a home computer of an NSA worker. Facts are still pending in this case – with Kaspersky at first denying any involvement but later acknowledging that it had destroyed documents once realizing they were classified, after also finding and removing hacking software from the developer’s computer.
Kaspersky Files Suit Against Trump Administration Over Ban of Their Products
The Department of Homeland Security banned the use of Kaspersky at the NSA and then by all the dozens of government agencies and networks where it was being used.
In December, Kaspersky Lab filed suit against the Trump administration, claiming damage to its reputation and business with evidence. But the US government claims it has evidence, which so far is classified, but at least would include intelligence shared by Israeli’s who hacked Kaspersky Lab in 2014 (as reported by the New York Times).
Eugene Kaspersky, chief executive, has offered to let the US inspect the company’s source code to reassure confidence in the trust of their products.
A “Winnie the Pooh” Experiment on Kaspersky Software
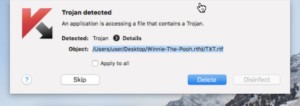
Mr. Wardle set up his own experiment to reverse-engineer Kaspersky’s software to demonstrate that such an inspection would not disprove the spying claims. Because by definition, A/V signatures, Kaspersky’s included, are updated continually and pushed out to clients regularly, they can be tweaked to do things, such as scan for specific content. As a test, among others, Wardle saved the text “Winnie the Pooh” onto his machine along with other markers (“TS/SCI”) and wasn’t surprised when Kaspersky’s A/V software tagged and quarantined the file.
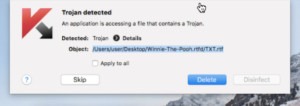
Next steps after something is tagged by A/V is often to send the file back to the A/V vendor for inspection. Imagine if your confidential documents were among the files being sent back! If a security vendor wanted to be nefarious, instead of searching for “TS/SCI,” they could search for “secret” or “confidential” or “R&D” “social security” – the list goes on – and collect all manner of private documents. See the article for more information about Wardle’s experiment.
In this way, as Mr. Wardle noted, “Antivirus could be the ultimate cyberespionage spying tool.”
And no one would ever suspect. Until now.
Read full Antivirus Software Can Be a Spying Tool Article