Every business runs on trust, and attackers know it. Every software update, vendor integration, and open-source library you rely on comes with an implicit assumption: that it’s safe. And yet, trust has become one of the most exploited attack surfaces in enterprise security. The modern software supply chain connects thousands of parts: code from multiple sources, automation pipelines, build processes, and distribution channels. This web of dependencies means one compromised component can deliver malicious code across entire industries in hours. If that component sits in a trusted path, traditional defenses rarely see it coming.
For CISOs, CIOs, and security architects, this is a pressing operational reality. Securing the supply chain means defending every external dependency, ensuring real-time visibility into execution, and building resilience that lets you withstand breaches without business collapse.
Prevention is essential. Resilience is non-negotiable. This material breaks down where the biggest risks originate, how exploits actually move through the supply chain, and what strategies are proving most effective.
Overview of Software Supply Chain Vulnerabilities
Enterprise applications aren’t single products—they’re mosaics. Proprietary code modules, open-source libraries, APIs, vendor integrations, and external SaaS tools all become part of that. Supply chain vulnerabilities are quickly becoming the top cybersecurity risk across ecosystems. More than half of large organizations—54%—say supply chain challenges are the biggest barrier to achieving cyber resilience, according to the 2025 WEF Global Cybersecurity Outlook survey.
In highly regulated industries, the fallout isn’t limited to operations. You’ll face compliance violations, breach notification obligations, regulatory audits, and potentially long-term reputational damage that’s hard to repair.
Software Supply Chain Risk: Importance for Enterprises in 2025
The trend line points one way—up. The same WEF GCO survey found that most concerns center on vulnerabilities introduced by third-party vendors and on cyberattacks, including malware distribution, that target weaknesses in the supply chain. Attackers deliberately target the weakest link in the chain: that unpatched open-source library, that overprivileged vendor integration, or that outdated build process no one’s reviewed in years.
If your environment contains legacy systems, custom applications, or critical tooling from multiple third parties, consider your supply chain risk level high by default.
Core Risks in Software Supply Chain Security
Attackers thrive on blind spots. They embed malicious logic inside approved updates, piggyback on vendor signing processes, and exploit automation pipelines you take for granted.
Not all enterprises re-scan or re-verify third-party modules post-integration. That leaves detection to the vendor. The SolarWinds attack proved how dangerous this really is. The malicious code behaved exactly like legitimate software because it was part of the legitimate build.
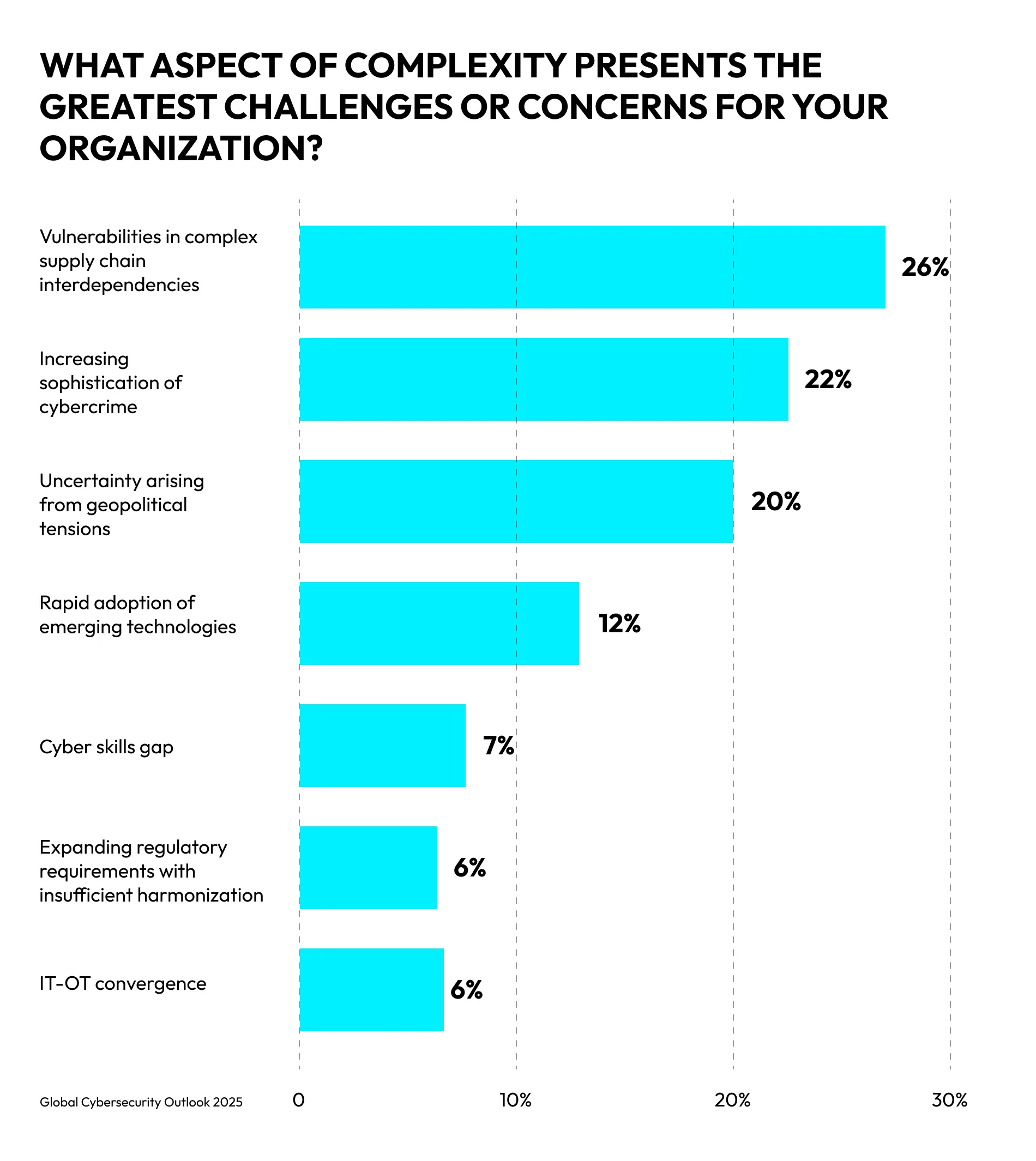
Source: Global Cybersecurity Outlook 2025
Mapping and Assessment: Uncovering Supply Chain Risk
For teams responsible for executive reporting, mapping and assessment deliver the clarity needed to drive down uncertainty. They turn blind spots into known, managed risks and build the foundation for resilient supply chain security across the business.
Dependency Analysis and Risk Visualization
Modern apps contain hundreds of dependencies, often several layers deep. Advanced supply chain risk assessment software maps these dependencies, generates SBOMs automatically, and keeps them updated through CI/CD workflows. Live scoring and alerting let you zero in on the risks that matter now, not last quarter.
Most Vulnerable Life Cycle Stages
Key vulnerabilities can surface at every stage of the software lifecycle, giving attackers narrow but dangerous windows to exploit.
- Procurement: Pulling in unvetted open-source components or libraries can import hidden flaws or even embedded malicious code.
- Build and integration: Compromised build and automation processes allow attackers to inject malicious code directly into the application before it ever reaches production.
- Deployment: Once an application is live, newly discovered zero-day vulnerabilities can be exploited long before patches are ready.
The most effective way to counter these threats is with real-time enforcement and least‑privilege execution. Applying these controls at every phase reduces the attack surface and shuts down exploitation opportunities before they can be used.
How Attackers Exploit Supply Chain Dependencies
Attackers don’t necessarily break in; they turn the software, updates, and automation you trust into their way in. When supply chain dependencies are exploited upstream, routine processes become high-impact threats.
How the exploiters work:
- Repository hijacks: Attackers seize control of popular open-source packages, publishing malicious updates that look legitimate. The name stays familiar, but the code turns dangerous. It only takes one compromised version to silently infect thousands of downstream users before anyone sees the problem.
- Build tool poisoning: Instead of targeting finished software, threat actors go upstream and tamper with build automation tools (CI/CD). Every application compiled or deployed from these poisoned pipelines now contains their stealthy payloads. By contaminating the source, attackers guarantee broad and persistent reach.
- Update server compromise: Trusted update servers—responsible for patching and maintaining environments—become attack vectors. Malicious actors infiltrate these servers, so regular patches and updates deliver exploits directly to production systems. Routine maintenance turns high risk overnight.
The MOVEit breach proves just how fast escalation can happen. Ransomware groups combined a fresh zero-day exploit with widespread, trusted file transfer software. Within hours, attackers moved laterally across major organizations, weaponizing trust to gain entry, exfiltrate data, and disrupt operations on a global scale.
Impactful Software Supply Chain Breaches
Real-world breaches to study and learn from:
- Kaseya VSA (2021): Ransomware hit over 1,500 downstream orgs via MSP software, pushing regulatory focus to SBOMs and vendor attestations.
- Codecov (2021): CI/CD tool compromise exfiltrated credentials from hundreds of companies, showing even developer tooling is an attack vector.
- 3CX DesktopApp (2023): Trojanized installer infiltrated critical sectors; response showed the value of runtime behavior blocking.
- XZ Utils backdoor (2024): CVE-2024-3094 is a vulnerability discovered in the open-source library XZ Utils that stems from malicious code that was pushed into the library by one of its maintainers.
Each case reinforces the same truth: trusted channels can be dangerous, and exploit windows are too fast for reactive measures alone.
Open Source: Agility vs. Risk
Open source accelerates development but expands your dependency web. Attackers routinely compromise maintainers, slip malware into popular packages, and let downstream integration spread it everywhere.
A mature SBOM program, paired with runtime monitoring, makes invisible risk visible—and enforceable.
Early Warning Signs of Compromise
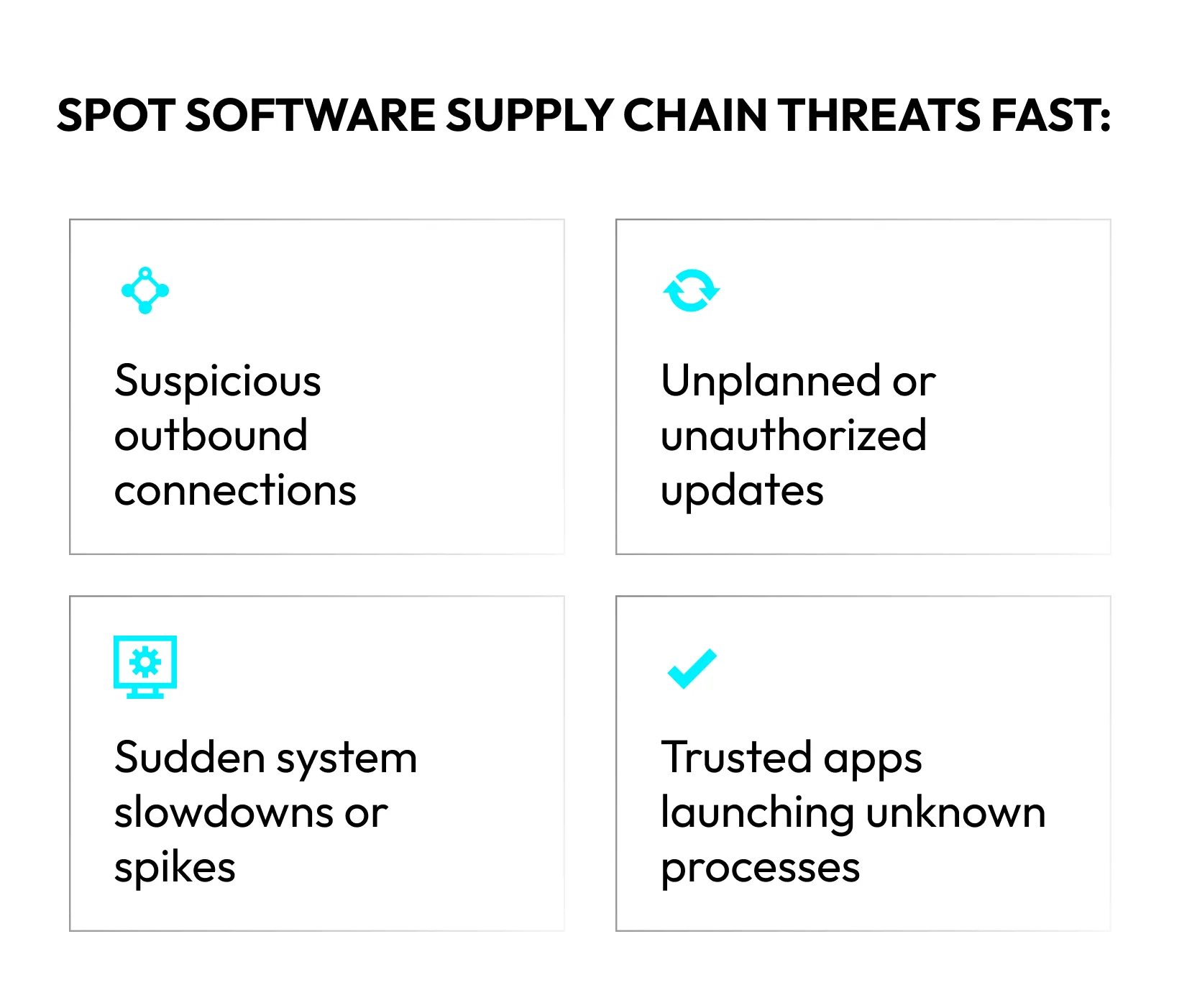
Detecting a software supply chain compromise early can mean the difference between containing a threat and allowing it to escalate across your environment or even industry. Attackers often employ subtle tactics to avoid triggering traditional defenses, which means security teams need to remain vigilant for nuanced, behavior-based signals.
Indicators typically include
- Unexpected outbound connections from trusted applications
When a business-critical application or a previously trusted binary initiates new outbound network communications—especially to unfamiliar domains or foreign IPs—it may signal data exfiltration, command-and-control activity, or an attempt to piggyback information outside the organization. - Unscheduled or unauthorized update attempts
Software updating outside planned windows, or update mechanisms that trigger without appropriate change controls, are classic red flags. Attackers exploit supply chain weaknesses by inserting malicious code into expected update processes or hijacking auto-update features to install backdoors. - Unexplained performance or resource changes
Sudden spikes or drops in CPU, memory, or network usage, especially after new components are deployed, point to active exploitation. Malware (including cryptominers, botnets, or data stealers) inserted by supply chain attackers works to blend in, yet still causes performance degradation, system slowdowns, or random failures as it operates undetected within trusted processes. - Trusted binaries launching unfamiliar or suspicious processes
If vendor-signed applications or well-known binaries start spawning processes outside their expected behavior, it could indicate malware injection or attempted privilege escalation. Adversaries commonly use legitimate processes to run malicious payloads to avoid endpoint detection and maintain persistence. - Changes in application configuration or permissions without authorization
Supply chain attackers may manipulate configuration files, alter permissions, or adjust registry keys to entrench malware further or open the door for future payloads. Automated monitoring tools should flag any system or application changes that don’t align with official update policies. - Credential access or privilege escalation events linked to third-party components
Attackers often move quickly to harvest credentials or escalate privileges using compromised vendor modules, scripting engines, or open-source libraries. Security alerts involving authentication anomalies tied to these elements should trigger immediate investigation and containment procedures. - Anomalous system event logs
Beyond performance data, well-designed SIEM and runtime protection platforms log every major event, configuration change, and unusual network flow. Unexpected spikes or patterns in these logs can point to a supply chain compromise in progress.
H1: Spot Software Supply Chain Threats Fast:
- Suspicious outbound connections
- Unplanned or unauthorized updates
- Sudden system slowdowns or spikes
- Trusted apps launching unknown processes
Best Practices: Mitigation and Protection Strategies
Faced with sophisticated supply chain exploits, security leaders must go beyond reactive patching and late-stage fixes. True resilience calls for a proactive, multilayered approach that integrates continuous visibility, real-time enforcement, and disciplined vendor oversight.
Effective defense means establishing end-to-end control and trust across every phase of the software life cycle. This includes knowing not just which components and vendors enter your environment, but precisely how each behaves at runtime.
Mitigation & Remediation
Mitigation and remediation are essential to managing software supply chain risk, but they serve different purposes. Mitigation focuses on immediate action to shield vulnerable systems from exploitation, buying critical time when a permanent fix isn’t yet available. In practice, this means stopping an attack in progress, blocking malicious code execution, or applying virtual patches without waiting for vendor updates or code changes.
Remediation, on the other hand, is the permanent removal of the vulnerability through patching, upgrading dependencies, refactoring code, or replacing compromised components. While mitigation keeps you protected in real time, remediation closes the loop, ensuring the risk cannot return.
When Log4j broke, smart teams mitigated immediately and then remediated once stable fixes were ready.
Comprehensive Asset and Dependency Visibility (Automated SBOMs)
You can go with automated SBOM generation for every application and service. Supply chains demand live, accurate mapping of all software components and third-party dependencies. Integrate SBOM management into your CI/CD pipelines and routine build processes, so every update, integration, and vendor-supplied element is tracked live as changes happen.
SBOMs provide critical transparency to expose risky components, accelerate response, and anchor regulatory reporting. But visibility is only the foundation, as SBOMs must inform every subsequent security control.
Deterministic Runtime Protection
Visibility doesn’t stop attacks—enforcement does. Virsec OTTOGUARD.AI delivers deterministic runtime protection by mapping the intended execution of every application and instantly blocking any deviation, exploit, or unauthorized code execution.
Unlike probabilistic or signature-based tools, deterministic enforcement works regardless of patch status, threat intelligence, or vendor speed. Whether your system faces a known vulnerability or a zero-day surprise, runtime protection neutralizes exploits before they execute, keeping mission-critical workloads safe and compliance intact.
Continuous Vulnerability Scanning and Risk Assessment
Apply continuous scanning with industry-leading platforms such as Snyk, Sonatype, Black Duck, and Wiz. Automated static and dynamic analysis tools flag new vulnerabilities, misconfigurations, and hygiene issues across custom code, open-source libraries, and vendor components.
Real-time risk scoring, coupled with SBOM-maintained inventories, allows your security team to prioritize exposures by business impact and respond immediately as threat intelligence emerges.
Vendor Attestations, Secure Development Compliance, and Ongoing Monitoring
Supply chain security is only as strong as your weakest supplier. Enforce vendor security attestations, require SBOM submission for every provided asset, and demand evidence of compliance with frameworks like NIST SSDF, SLSA, and ISO27001.
Tie vendor contracts and onboarding to these requirements, and monitor each supplier’s patching speed, transparency, and SDLC best practices. Use continuous monitoring solutions to spot unexpected changes or behavioral anomalies in third-party dependencies as they arise.
Breach Simulation and Incident Response Readiness
Don’t wait for a real-world attack to test your posture. Conduct routine tabletop exercises and breach simulations—focusing on software supply chain scenarios—to validate and improve your team’s readiness.
These drills help you identify gaps in workflows, escalate response speed, and ensure your runtime protection and visibility controls operate seamlessly when the pressure rises.
Building and Managing SBOMs
SBOM generation in the CI/CD cycle ensures that inventory is always current.
Software Supply Chain Risk Management
Proactive software supply chain risk management should become an ongoing discipline built on visibility, accountability, and enforcement. With an expanding scope of third-party code, open-source dependencies, and vendor integrations, organizations must continuously validate the integrity of every component and the security posture of every supplier.
Ongoing Review and Auditing
Mission-critical dependencies get monthly reviews, others quarterly, with continuous AI-driven monitoring in between. This produces a real-time proof of consistent oversight.
CI/CD Pipeline Security
Secure builds with:
- Signed code and artifacts.
- Mandatory SBOM validation before deployment.
- Role-based access to build systems.
Vendor Evaluation
Score vendors on speed to patch, adherence to SBOM practices, and compliance with secure coding frameworks. Tie contract terms to these metrics.
Compliance, Regulations, and Frameworks
ISO/IEC 27001 and SLSA frameworks help structure mature governance and reporting. You can track the following KPIs:
- Percentage of SBOM-mapped dependencies.
- Mean time-to-mitigate and remediate vulnerabilities.
- Incidents blocked by runtime protection.
- Vendor patch speed.
Building a Secure Software Supply Chain Culture
Mature security cultures integrate:
- End-to-end SBOM visibility.
- Deterministic runtime controls.
- Frequent dependency audits.
- Vendor oversight as a standing practice.
Mitigating Supply Chain Vulnerabilities with Virsec’s OTTOGUARD.AI
Virsec’s OTTOGUARD.AI delivers deterministic runtime protection: a patented zero-trust, “lock down by default” technology that maps the legitimate execution flow of each application and enforces it with precision. This creates a binary security state:
- If execution strictly matches the known-good baseline → it runs.
- If it deviates in any way → it is instantly blocked.
Because this enforcement happens at runtime, it stops the exploit before it executes, independent of whether a patch exists, a signature is known, or a threat is brand new. There’s no dwell time, no “patient zero,” and no opportunity for lateral movement. Book a demo to learn more.
FAQs
Software supply chain vulnerabilities emerge from flaws, weaknesses, or malicious insertions in any third-party code, open-source libraries, vendor components, or tooling integrated into your environment. In a world where so many enterprise workloads run code sourced outside organizational boundaries, these exposures are both unavoidable and high-risk.
A single exploited supply chain vulnerability can trigger costly data breaches, regulatory fines, reputation loss, and operational downtime, sometimes spreading from one supplier to thousands of downstream organizations.
Supply chain attacks slip past perimeter tools by weaponizing trust. Malicious code arrives masquerading as legitimate updates, certified builds, or standard libraries. Most security solutions focus on known threats, signature detection, or anomaly tracking. But supply chain attacks blend in, often using legitimate developer workflows, signed binaries, and approved toolchains to hide in plain sight.
Without runtime enforcement and deep visibility, organizations operate blind. Only solutions that continuously monitor execution, deterministically blocking deviations from known-good application behavior in real time, can catch and halt these sophisticated tactics before damage spreads.
Most codebases mix in hundreds of externally sourced components, many of which go years out of date or lack robust security oversight.
Visibility into components—achieved through automated SBOMs and live inventory—is the first step. However, simply knowing what’s running does not stop attackers from exploiting weaknesses. You must also deploy active mitigation solutions like Virsec’s OTTOGUARD.AI, enclosing every component in a runtime shield, instantly blocking exploit attempts before malicious code can execute, regardless of patch status or threat intelligence. This patchless mitigation ensures that even when outdated, unpatched, or vulnerable dependencies remain in your stack, attackers cannot weaponize those weak links.
In practice, mitigation transforms unmanaged dependencies from open attack surfaces into monitored, protected assets. By combining visibility and runtime enforcement, you retain control over risk, even as your supply chain grows more complex and dynamic.
Top risks include:
- Compromised vendor updates and malicious code injections.
- Trojanized open-source packages (often the result of hijacked maintainers).
- Legacy dependencies with unpatched, known vulnerabilities.
- Opaque inventories—lack of up-to-date SBOMs and component tracing.
- Weak build pipeline security (CI/CD compromises).
Unverified third-party automation scripts and external integrations.
Attackers exploit any gap in the trust chain, often using techniques that evade classic malware detection and monitoring.
Mitigating risk requires security controls at each life cycle stage, not just after deployment:
- Procurement: Integrating new libraries or services without full security vetting.
- Build and integration: Automated CI/CD pipelines, if unprotected, spread compromised code instantly.
- Deployment: Attacks can propagate during rollouts or updates, especially when zero-days hit before patches appear.
Update and maintenance: Legitimate-looking updates become vehicles for stealthy malware.
Yes. No organization, sector, or government is immune. The SolarWinds, Log4j, and MOVEit breaches proved that attackers exploit systemic software supply chain trust across the board, affecting global enterprises and public agencies alike.Any organization relying on external code, managed services, or automated software supply chains faces the same core risks. Prevention means shifting from reactive patching and signature-based detection to real-time mitigation: runtime protection, in-depth visibility, and prompt blocking of abnormal execution.
To truly secure your software supply chain in 2025, you need to implement controls and solutions that grant visibility and deliver immediate, uncompromising protection.
Key steps are to:
- Automate SBOM generation and verification: Use tools that integrate directly with your CI/CD pipelines for real-time component inventories.
- Enforce deterministic runtime protection: Virsec’s OTTOGUARD.AI sets the gold standard, mapping the approved execution of every application and instantly blocking deviations, malicious behavior, or zero-day exploits on critical and legacy workloads. This solution stops attacks pre-execution, minimizing risk exposure and rendering patching delays irrelevant.
- Apply patchless mitigation: Unlike traditional solutions that depend on immediate vendor response, workload patchless mitigation ensures you can neutralize vulnerabilities (known or unknown) before attackers can exploit them, delivering virtually zero mean time to remediate (MTTR).
- Integrate automated scanning and agentic AI-powered risk assessments to reduce the burden on your security teams and support frictionless operations.
- Demand vendor security attestations and SBOM submissions: Require every supplier to provide verified SBOMs and evidence of their secure software development lifecycle (SDLC) practices.
- Simulate supply chain breach response and recovery: Tabletop exercises are more meaningful when you know you have autonomous, always-on runtime mitigation in place.
Adopt and enforce frameworks (NIST SSDF, ISO, SLSA) with runtime monitoring as the operational core: Use industry frameworks for governance and reporting, but anchor your program in solutions, with OTTOGUARD.AI, that deliver continuous enforcement, audit trails, and real-world resilience.




