“Your computer’s network has been breached and infected with MegaCortex Malware.
All of your user credentials have been changed and your files have been encrypted.
We assure that the only way to retrieve your data swiftly and securely is with our software.
Restoration of your data requires a private key which only we possses.“
Imagine your workday coming to a screeching halt with that message on your computer screen. The rest of the message is even more chilling, re-printed below.
The MegaCortex ransomware note also tells users that they, the hackers, can and will change their login credentials if they don’t give in to demands. Researchers have verified that this threat is real. The hackers also inform users that they have made a copy of their data and issue the second threat that if they do not pay the ransom, they will make that data public.
We’ve reported in recent articles that while some companies do pay the ransom, the majority opt not to, not wanting to encourage the heinous behavior. Clearly, the data-nappers are using greater extortion methods to not let that be an option. Failure to comply will be still more painful.
On the flip side, the thieves promise that if payment is made successfully, they will erase the copies they’ve made of the users' data. "Once the transaction is finalized all of copies of data we have downloaded will be erased." As if that could be trusted. Adding further irony, they pledge to be available to assist with any technicalities. The whole scenario ventures into the surreal.
MegaCortex Ransomware Nightmare, Escalating Round After Round
Security researchers who track malware and attacks, readers of cybersecurity news and previous victims are already well acquainted with MegaCortex. The malware got attention last summer when it struck many business. Then, it was known that the malware functioned with Emotet Trojans and carried a disk wiping function. (See our article MegaCortex Malware Strikes Business Networks, Does Damage Both as Ransomware and Disk Wiper.) Now, the malware can change user passwords, (which incidentally, LockerGoga malware reportedly does as well).
MegaCortex continues to add to its injurious traits. Once their passwords are changed, users will be permanently blocked from accessing their data and systems unless they ransom their way out of that predicament. But on top of that, they now face the added threat of having their stolen data made public if they don’t comply with the demands.
If You Become a MegaCortex Victim, You Will See These Ransom Notes
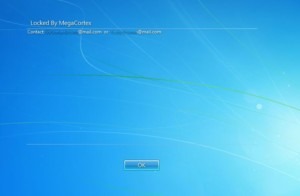
The attacks strike Windows PCs and users learn they are victims when the message below appears on their screen.
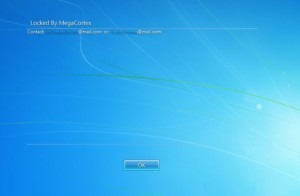
MegaCortex Legal Notice, image from Bleeping Computer
The legalese language appears on a designer-ish background. Users are given two email addresses and a place to click an “OK” button.
Once launched, MegaCortex posts its ransom note, entitled “"!-!_README_!-!.rtf” which appears on the victim’s screen. The text of the ransom note is below.
Entire Ransom Note (spelling and grammar errors included):
“Your computer’s network has been breached and infected with MegaCortex Malware.
All of your user credentials have been changed and your files have been encrypted.
We assure that the only way to retrieve your data swiftly and securely is with our software.
Restoration of your data requires a private key which only we possses.
To confirm that our decryption software works email to us 2 files from random computers.
You will receive further instructions after you send us the test files.
After receiving payment we will provide you with the decryptor including its full source code and credentials to your computers.
We have also downloaded your data to a secure location. In the unfortunate event of us not coming to an agreement, we will have no choice but to make this data public.
Once the transaction is finalized all of copies of data we have downloaded will be erased.
We will provide any assistance if needed.
Contact emails:
[xxx@mail.com
xxx@mail.com]
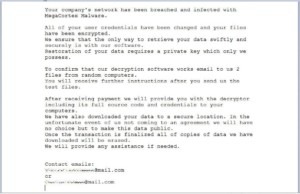
MegaCortex Ransom Note, image from Bleeping Computer
Whether or not the attackers can actually make good on the second part of their threat isn’t yet confirmed. Perhaps it’s intended to motivate users to pay. But it stands to reason that given the attackers have already demonstrated they have breached the user's system and can change passwords, it’s quite possible they can carry out the rest of the dirty deeds as they’ve claimed.
Some Details of the MegaCortex Attack – Uses DLL Files and CMD Scripts
Malware expert Vitali Kremez at Malware Hunter Team obtained a sample of the MegaCortex malware and along with Bleeping Computer, they have performed detailed analysis and testing of the malware*. They were able to confirm that after encryption and reboot, they could not log in to the test computer. The Windows password was indeed changed, accomplished by executing the net user command when the ransomware is launched.
Further testing shows the attackers use DLL files and CMD scripts to carry out the attack.
Two DLL files are used to encrypt the PC files. One DLL file looks for files to encrypt and the other is involved in the encrypting. The DLL files are not injected but are run via Rundll32.exe. After this, the ransom note is displayed on the screen to victims. Victims can see the ransomware has altered files with the .m3g4c0rtx extension to each file.
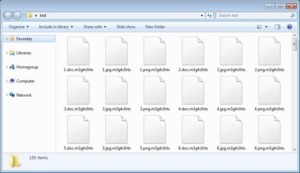
MegaCortex encrypted files, image from Bleeping Computer
Testing by Kremez and Bleeping Computer on a target machine also found that the malware launcher extracts three CMD scripts to the C:\Windows\Temp directory. A signed certificate from an Australian company, “MURSA PTY LTD” is used.
The scripts execute multiple commands, including wiping free space on the C:\ drive, delivering the MegaCortex Malware seizure notice, and cleaning the files used to encrypt the PC. An example of the first script shown below.
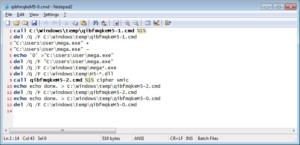
MegaCortex Command script, image from Bleeping Computer
Even with the majority of victims not paying the ransom so far, successful ransomware attacks are lucrative enough to keep the attackers as motivated than ever. By raising the ante like this, these attacks stand to become increasingly successful against greater numbers of victims.
*For a much deeper description and analysis of this malware attack, see Bleeping Computer’s detailed article. https://www.bleepingcomputer.com/news/security/new-megacortex-ransomware-changes-windows-passwords-threatens-to-publish-data/
Further resources:
MegaCortex Malware Strikes Business Networks, Does Damage Both as Ransomware and Disk Wiper
LockerGoga Ransomware Slams Industrial Firms in Europe, Could Hit Anyone
In the Face of a Ransomware Attack, Can Your Defenses Prevail?
Ransomware Demo: Multi-Level Protection Against Ransomware
Sources:
https://www.tomshardware.com/news/megacortex-ransomware-changes-windows-login-password