Vulnerability Disclosure: On December 3, Meta (React Team) and Vercel (Node.js) publicly announced the React2Shell vulnerability (CVE-2025-55182) following a private disclosure on November 29, 2025, by security researcher Lachlan Davidson. A massive wave of scans and attacks followed the public disclosure. Because the vulnerability enables unauthenticated remote code execution (RCE) and attackers actively exploited it, CISA added React2Shell to its Known Exploited Vulnerabilities (KEV) catalog.
Why React2Shell is such a big deal
The React JavaScript library is one of the most widely adopted frontend technologies. When application teams need charts, maps, forms, or other UI elements, they can almost always find a mature, high‑quality React package for that use case. React components also allow teams to change the look and feel of the frontend quickly, which has helped drive adoption. React components now appear in over 50% of websites worldwide, including those of major ISVs such as Meta, Netflix, Airbnb, Uber, and Instagram. Weekly downloads of the React NPM package exceed 22 million, underscoring its market leadership.
React Server Components further improved the experience by allowing the server to render dynamic content in parallel while the client renders static HTML. This parallelization solved a long‑standing issue where browsers showed blank pages while the backend JavaScript waited for data.
What makes the React Server Component vulnerable
The React ecosystem breaks down into server and client components as shown below.
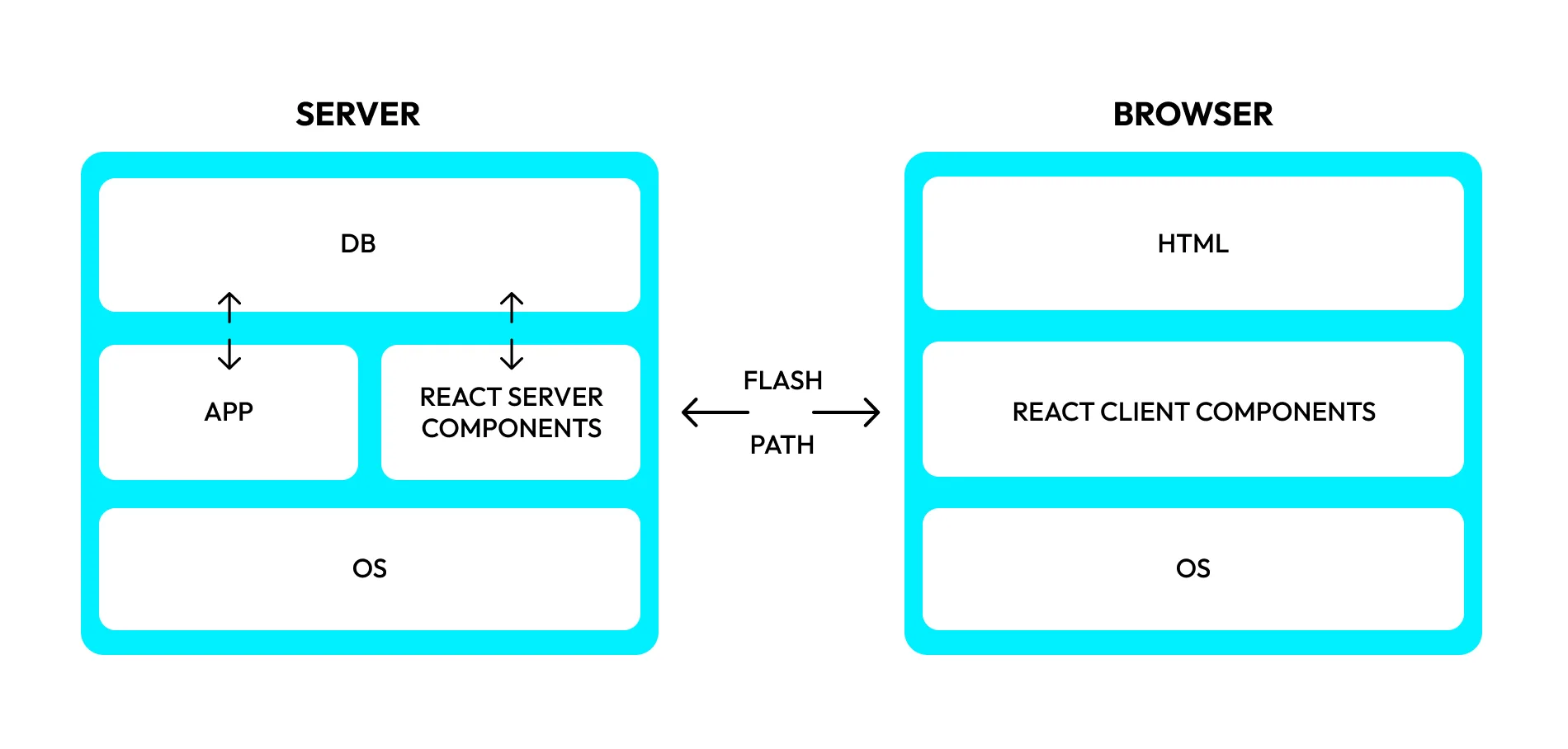
The React Server Component renders active content on the server, while the Client Component renders static parts of the HTML page in the browser. This parallel processing delivers content faster and improves user experience.
The server and client communicate using a protocol called Flight Path. Flight Path allows the browser to send data and the names of pre‑programmed actions that the server should execute. Based on user actions, the client sends a serialized data stream over Flight Path, requesting processed data from the backend. The server deserializes this stream to understand which actions to run and which data the user expects.
In the vulnerable implementation of the React Server Component, if a malicious object arrives in an unfamiliar serialized format, the server does not fail safely. Instead of rejecting the input and generating an error, it executes the server action immediately with no further validation. Threat actors exploiting React2Shell use this weakness to package actions the React Server Component implicitly trusts and then runs on the vulnerable server.
The attack kill chain works as follows:
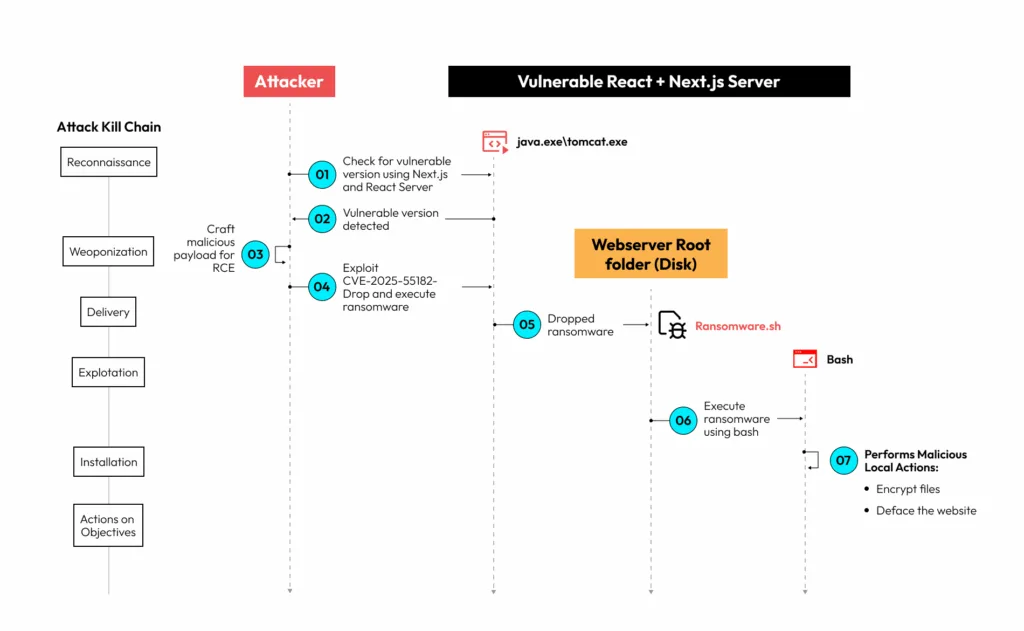
The objective of steps 1 and 2 is to determine whether the target server is vulnerable. In steps 3 and 4, the threat actor builds and delivers a malicious serialized object using the Flight Path protocol. Due to the RCE vulnerability (CVE-2025-55182), the threat actor can drop a web shell and any required encryption code, and then execute a reverse shell in step 5. Once the attacker establishes a two‑way connection between the target server and the command‑and‑control server, they can run arbitrary commands on the shell of the victim server. At that point, in step 6, the Threat Actor can execute the RCE payload of their choice; in this demo, the RCE chosen was to encrypt several backend files.
What happens on a Virsec VSP-protected Server
On a server protected by Virsec VSP, the attack stops early in the kill chain—at step 4. In the accompanying demonstration, multiple Virsec Protection Engines in the kill chain block the attack well before the threat actor gains control of the server or executes arbitrary code. The platform does not rely on transient indicators of compromise or any prior knowledge of the attack.
Instead, Virsec’s Protection Engines use patent‑protected Default‑Deny Allow‑On‑Trust technology to block untrusted code supplied by the threat actor. As a result, Virsec offers true patchless vulnerability mitigation to vulnerabilities such as the troublesome React2Shell vulnerability.
What defines a true Patchless Vulnerability Mitigation (PVM) solution
A true patchless vulnerability mitigation solution should deliver the following characteristics:
- Theoretically, a patch stops the exploitation of the underlying vulnerability, thereby delivering zero-dwell-time protection from threat actors. It stands to reason that a true patchless vulnerability mitigation solution must be as effective as a patch in that it must deliver zero dwell time. This, in turn, means the threat actor has zero opportunity to execute even one instruction of the arbitrary code they’ve chosen.
- A true patchless vulnerability mitigation solution cannot hide behind a reachability argument. A determined threat actor can phish legitimate personnel and reach any part of an enterprise’s infrastructure with ease.
- A true patchless vulnerability mitigation solution cannot hide behind an exploitability argument. Believing that threat actors cannot exploit vulnerabilities underestimates their abilities and is therefore akin to sticking one’s head in the sand. Many threat actors are highly skilled and driven by profit, perceived national interests, or opportunistic gain.
- A true PVM solution should not rely on Indicators of Compromise (IOCs) such as IP addresses, file names and hashes, byte patterns in network traffic, or any ephemeral threat intelligence that a threat actor can modify at will. Overreliance on IOCs turns defense into a whack‑a‑mole exercise.
- A true PVM solution should not force enterprises to make poor decisions in the name of prioritization. The solution must scale to handle large vulnerability backlogs without requiring organizations to accept unnecessary exposure. Prioritization remains important for workflow, but the technology itself should not demand compromises. Threat actors look for opportunity; when a weakness remains, they exploit it.
Why Virsec
Unlike other solutions that promise patchless vulnerability mitigation or prioritization, Virsec delivers patchless vulnerability mitigation that meets these requirements:
- Protection even when the vulnerability is a zero‑day and known only to a small group, often excluding the application vendor and the enterprise that deployed the software.
- Protection even when the vendor has not yet released a patch. Patch creation requires root‑cause analysis, coding, testing, and setting up distribution.
- Protection even when a patch exists but teams have not deployed it. Reasons range from lack of awareness or limited testing resources to the potential impact of downtime.
- Protection even when a patch prescribed by the app’s ISV is broken and cannot protect the vulnerable app. Recall that the Log4J vulnerability took four iterations of patching before the library was finally patched adequately.
- Protection even when the app has reached the end-of-life stage and no further patches are forthcoming. Most software will reach end-of-life in 5 to 7 years. Changing apps that deliver is not easy. We often see apps that are 20 to 30 years old and still deployed.
- Protection even when no IOCs exist or the IOC set remains incomplete.
- Protection even if threat actors rewrite exploit code. Different authors and small code changes produce different file hashes, so any defense that depends on specific hashes or signatures can be easily bypassed.
Conclusion
Virsec VSP is designed to meet the requirements of a true patchless vulnerability mitigation solution. In practice, VSP often reduces effective risk by 90% or more, with even higher coverage for vulnerabilities with critical and high CVSS scores. Enterprises unlock these benefits without:
- Taking production servers offline
- Testing and rolling out emergency patches
- Risking application functionality by applying unproven fixes
- Relying on patches that may still leave gaps
Virsec VSP significantly reduces cyber risk even as the volume and complexity of vulnerabilities continue to grow. The platform focuses on real mitigation instead of arguments about exploitability or reachability.Request further information or book a demo at virsec.com.
Frequently Asked Questions
React server components enable part of an application’s UI to render on the server, rather than only in the browser, which can improve performance and user experience. Because React server components run on the server and accept user-driven input, any flaw in how they handle serialization, deserialization, or server actions can expose powerful attack paths that lead to remote code execution if not properly controlled.
React2Shell targets the way some React server components deserialize and execute server actions sent from the client. When a vulnerable implementation accepts crafted serialized objects without strict validation, an attacker can inject malicious actions and trigger them on the server. This makes React server components a critical focus area for runtime security controls and patchless vulnerability mitigation.
Patchless Vulnerability Mitigation protects React server components by blocking untrusted behavior at runtime instead of waiting for a vendor patch or maintenance window. Virsec’s runtime controls inspect execution in memory, validate allowed code paths, and stop malicious actions before they complete, so even if a React Server Component contains a vulnerability like React2Shell, attackers cannot successfully exploit it.
Patching remains essential, but it often lags behind disclosure and active exploitation. React server components sit on critical servers that support production traffic, making aggressive patching and frequent restarts risky. Patchless vulnerability mitigation gives security and infrastructure teams a way to protect these components immediately, maintain uptime, and then patch on a controlled schedule, without leaving a window that attackers can exploit.




