Virsec Security Research Lab Vulnerability Analysis
The Virsec Security Research Lab provides timely, relevant analysis about recent and notable security vulnerabilities.
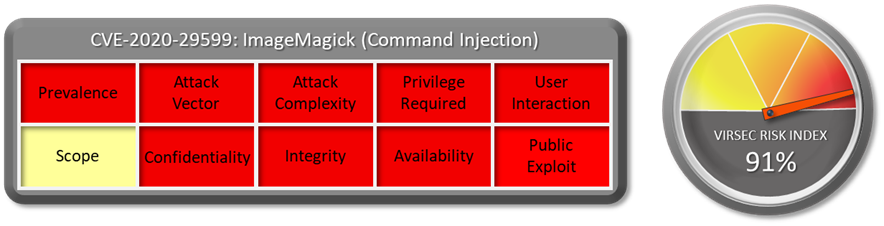
1.1 Vulnerability Summary
Magmatic before 6.9.11-40 and 7.x before 7.0.10-40 mishandles the -authenticate option, which allows setting a password for password-protected PDF files. The user-controlled password was not properly escaped and sanitized, and it was therefore possible to inject additional shell commands via coders/pdf.c.
Watch the video to learn more about this and other important vulnerabilities.
1.2 CVSS Score
The CVSS Base score of this vulnerability is 9.8 Critical. CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
1.3 Affected Version
ImageMagick before 6.9.11-40 and 7.x before 7.0.10-40.
1.4 Vulnerability Attribution
This vulnerability was disclosed by Alex Inführ.
1.5 Risk Impact
ImageMagick® is a popular open-source tool that is used to create, edit, compose, or convert bitmap images. It can read and write images in a variety of formats (over 200) including PNG, JPEG, GIF, HEIC, TIFF, DPX, EXR, WebP, Postscript, PDF, and SVG. ImageMagick can resize, flip, mirror, rotate, distort, shear and transform images, adjust image colors, apply various special effects, or draw text, lines, polygons, ellipses and Bézier curves.
Exploiting this vulnerability can lead to planting backdoor and affecting the entire organization. A publicly available exploit is available here.
1.6 Virsec Security Platform (VSP) Support:
The Virsec Security Platform (VSP)- Host monitors processes that are spawned which are not part of a set of whitelisted process. Any attempt to execute new command or unknown binary would be denied by VSP-Host’s Process Monitoring capability.
1.7 Reference Links:
- https://github.com/ImageMagick/ImageMagick/discussions/2851
- https://nvd.nist.gov/vuln/detail/CVE-2020-29599
- https://insert-script.blogspot.com/2020/11/imagemagick-shell-injection-via-pdf.html
Download the full vulnerability report to learn more about this and other important vulnerabilities.
Jump to: List of CVE Vulnerabilities


