While Equifax is finally pledging to shore up its security, many feel they got off far too easy
<<Download a free business and consumer guide for protecting your data after a breach>>
On September 7, 2017, Equifax announced it had been hacked and the personal data of 143 million Americans was stolen and was out out in the wild (on the dark web). Unauthorized access to people's private data occurred from mid May through July 2017. Equifax discovered the breach on July 29, 2017 but withheld the information from the public for 40 days – drastically increasing every victim’s exposure and potential damage.
On March 1 of this year, Equifax revealed that yet another 2.4 million more US customers had data stolen in the breach, bringing the total to roughly 145.5 million people -- about half the households in the US.
The hackers gained access through the Apache Struts VCE-2017-5638 vulnerability that opened the door for the massive hack. By the numbers, it was the 4th largest cyber attack to date. But because of the severity of the breach and the extent of the damaging nature of the data stolen, the breach is widely viewed as the worst we’ve seen so far.
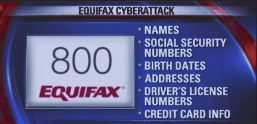
The items below are what they got of your data. This will be the breach that keeps on giving for a long time.
- Names
- Social security numbers
- Birth dates
- Addresses
- Driver’s license numbers
- Credit card info (in some cases)
But, where are the Consequences?
Since the breach, former Equifax executives and an employee have been charged with insider trading for unloading stock during the 40 days before announcing the breach. And 8 US states made an agreement with Equifax in an effort to make sure it beefs up its security. These states did so because, so far, no charges or penalties have been forthcoming. (Read article about this agreement.) Consumers are paying a big price – why isn’t Equifax?
That’s remains a good question.
This year, two significant laws took center stage and had either been in effect in September 2017, Equifax would have faced staggering penalties. The first law is the oft-discussed (and dreaded) GDPR, which went into effect in May. Most US organizations are affected and struggling to comply (read our GDPR article). And the other, the California Consumer Privacy Act of 2018, was passed this year and will take effect in 2020 (see more info here).
The GDPR laws impose significant fines, both of which would have hit Equifax head on. The first would have been for failing to protect its data and the penalty for that would have been 4% of its global revenue. The second fine would have been for failing to notify its affected customers and the penalty for that would have been another 2% of its global revenue. Equifax’s revenue in 2017 was $3.36 billion, so its fine would have been $201 million.
The California privacy law fines are assessed based on number of individuals impacted, ranging from $100-$750 per California resident. Roughly 56% of Americans were affected by the breach so if we apply that percentage to California’s population for a rough estimate, Equifax could have faced a fine somewhere between $1.7 billion and $12.75 billion.
No fines have yet been assessed. But it may not be over yet. According to the NY Times, Equifax is still being investigated by several agencies, including the Federal Trade Commission, the Security and Exchange Commission and the Consumer Finance Protection Bureau.

In the meantime, what is Equifax doing about security?
Under the terms of the agreement with the 8 US states mentioned above, Equifax is obligated to develop a detailed security assessment with increased board oversight of cyberthreats. It must also improve its process for patching known vulnerabilities. If this sounds like nothing more than the basics that any responsible company should do when it comes to security, that’s because it is. Equifax still holds the information of over 800 million people and 88 million businesses around the world. Moving in the right direction, yes, but with stakes like these, maybe these steps are not enough.
Perhaps another step they’ve taken will ultimately bring greater results. Six months after the breach, the company hired Jamil Farshchi as their new chief information security officer (CISO). He has a history of rebuilding the reputation of companies whose trustworthy reputation has crumbled. He was also CISO for Time Warner and was brought onboard as Home Depot’s CISO to rebuild their reputation after a hack exposed 50 million Home Depot’s customer credit card accounts. Now, he’s outlined a 3-year plan for Equifax to rebuild its reputation and regain customer trust – your trust.
Equifax has a 3-year security plan to regain your trust
First, Equifax says responsibility for security now doesn’t just belong to the top executives. It’s part of every person’s job.
Jamil reports directly to the new Equifax CEO, which is the case for only a few Fortune 100, 1000 and 2000 companies. Equifax is building in incentives for employees to make security a priority, where achieving goals is now a part of their annual bonus structure to be added or subtracted as accomplished. They’ve committed $200 million this year in resources to the cause (ironically, about what a GDPR penalty would have been). They’ve also brought on a new CTO from IBM who promotes the philosophy that “technology, if done right, should eliminate the vast majority of security risks.” Their new CEO has also made strong commitments to securing their customer information, professionally and personally pledging to protect all the data entrusted to them.
What Home Depot experienced is not the same as what Equifax is going through. Home Depot is a consumer-based company (business to consumer), while Equifax functions as business-to-business (B2B). As such, Equifax must follow more regulations but, publicly at least, they are vowing to restructure security as a top priority and rebuild trust, structured in a 3-year plan with year one to build, year two to mature and year three to become leaders in their space.
Jamil stresses that it was Equifax themselves who discovered their own breach. He believes this demonstrates even a prior commitment to technology and security that they will build on now. But he also acknowledges that rebuilding trust is a whole lot different from having it prior to a significant breach. But now post breach, they have a lot more to prove. Jamil says they’ll do it by delivering and executing. And, he believes if a company follows the principles they’re following now from the start, they probably could avoid finding themselves in a post-breach position to begin with.
Only Time Will Tell
For everyone’s sake, no one ever wants to see another breach at Equifax or any other credit bureau or business of any kind. But that’s not the same thing as allowing the world’s 1st or 4th (depending on how you look at it) breach of all time go unpunished. Time will tell us whether they get their security act together and whether there is a price for them to pay financially, beyond the massive hit they've taken to their reputation. Either way, it’s likely no one will think of the name Equifax in quite the same way ever again.
<<Download a free business and consumer guide for protecting your data after a breach>>
Sources
https://www.cnet.com/news/equifax-has-a-plan-to-win-your-trust-back-itll-take-three-years/
https://www.darkreading.com/equifax-avoided-fines-but-what-if-/a/d-id/1332487



