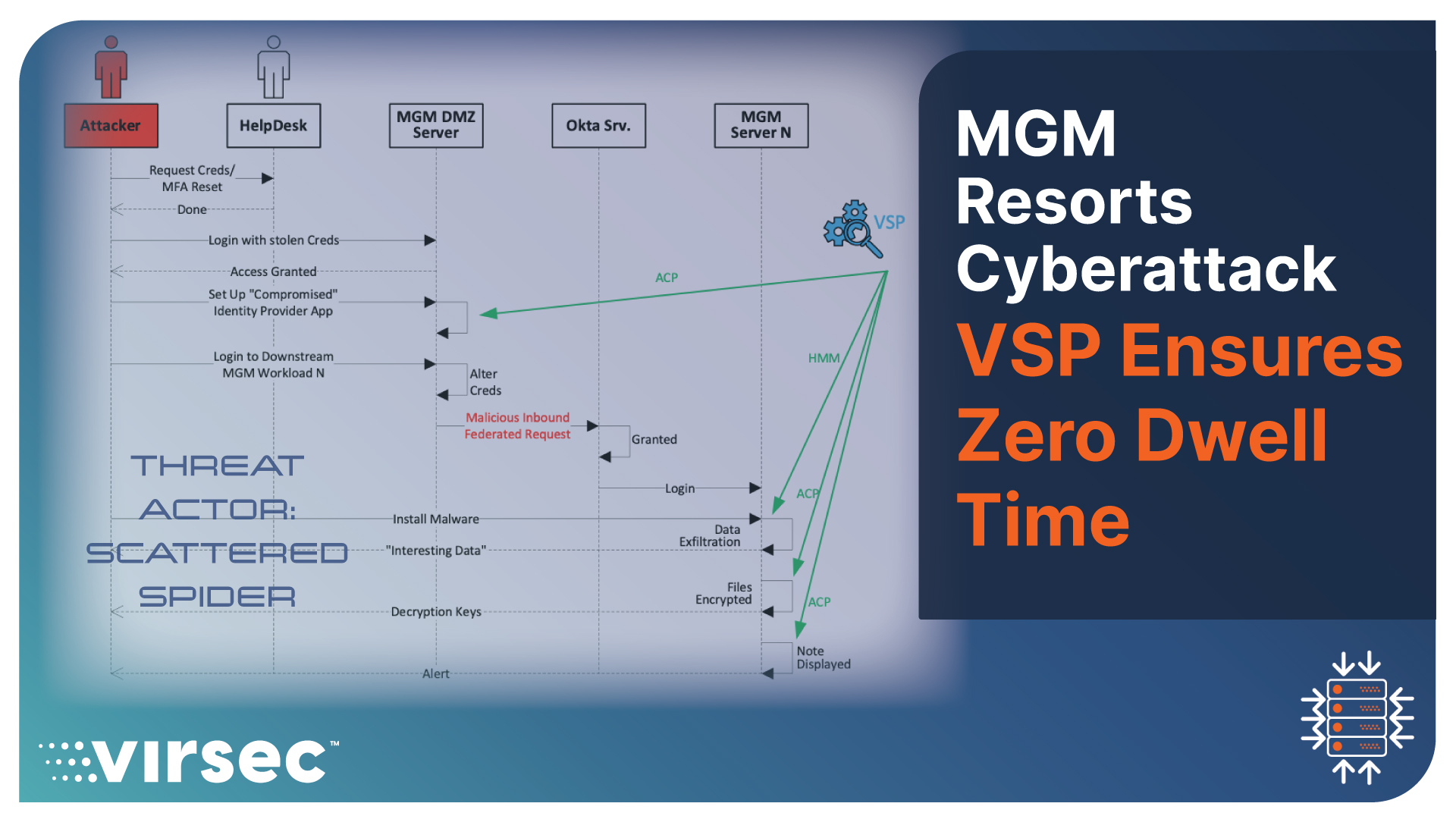
The cyberattack on MGM Resorts in September 2023 affected the company's operations and services. The Threat Actor, Scattered Spider demonstrated a high level of sophistication in their tactics, using voice phishing attacks and deploying their own Identity Provider (IDP). This blog shows the kill chain for the attack and demonstrates how VSP ensures that Threat Actors have zero dwell time on the targeted workload, even if they gain initial access with compromised credentials.
Incident Overview: On September 11, 2023, MGM Resorts, a renowned hospitality and entertainment company, reported a cyberattack that significantly disrupted its operations. Services such as dining, entertainment, and entertainment-related services were affected, and hotel guests faced difficulties accessing their rooms.
Attribution: The attack is believed to have been orchestrated by a group known as "Scattered Spider" (also identified as UNC3944), consisting of individuals in their twenties who are native English speakers. This group has connections with another cyber gang called "ALPHV" (also known as Black Cat), which operates a ransomware-as-a-service operation from Russia. Scattered Spider specialized in voice phishing (vishing) attacks and demonstrated a high level of sophistication in their tactics. They researched senior MGM Resorts staff via LinkedIn. They used this information to contact MGM's Helpdesk, where they verbally requested a phone number reset for a highly privileged MGM Resorts employee.
Attack Details: Scattered Spider gained unauthorized access to a DMZ Server using compromised credentials. However, Scattered Spider realized that the Helpdesk would soon realize their folly, and then they would be locked out. To overcome this issue, Scattered Spider established a secondary Identity Provider (IDP) app under their control to maintain continued access. This secondary IDP submitted authenticated requests to Okta, MGM's authorized Identity Provider. Okta's Chief Security Officer David Bradbury confirmed that the attack succeeded because the threat actors deployed their own IDP, demonstrating their advanced capabilities. He also pointed out that there was evidence since mid-August that Threat Actors were targeting many Okta customers with a similar tactic.
The Kill Chain: Information from MGM, Okta, Dark Reading, and Bloomberg reveals the following kill chain for the MGM attack:
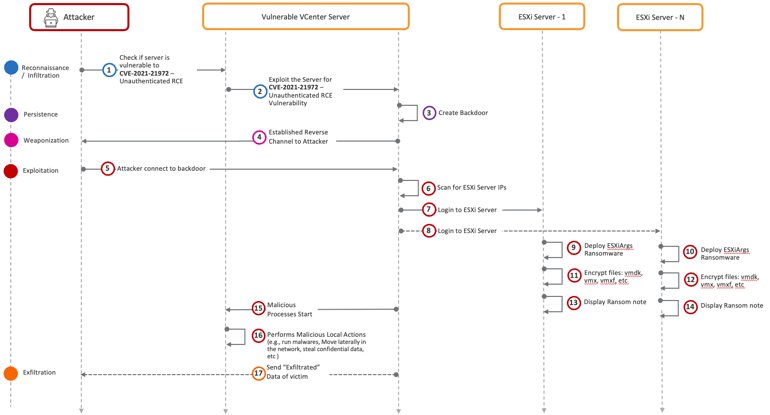
Virsec's Protection: The Virsec Security Platform (VSP) protection at various stages of the kill chain is indicated by green arrows in the kill chain diagram below:

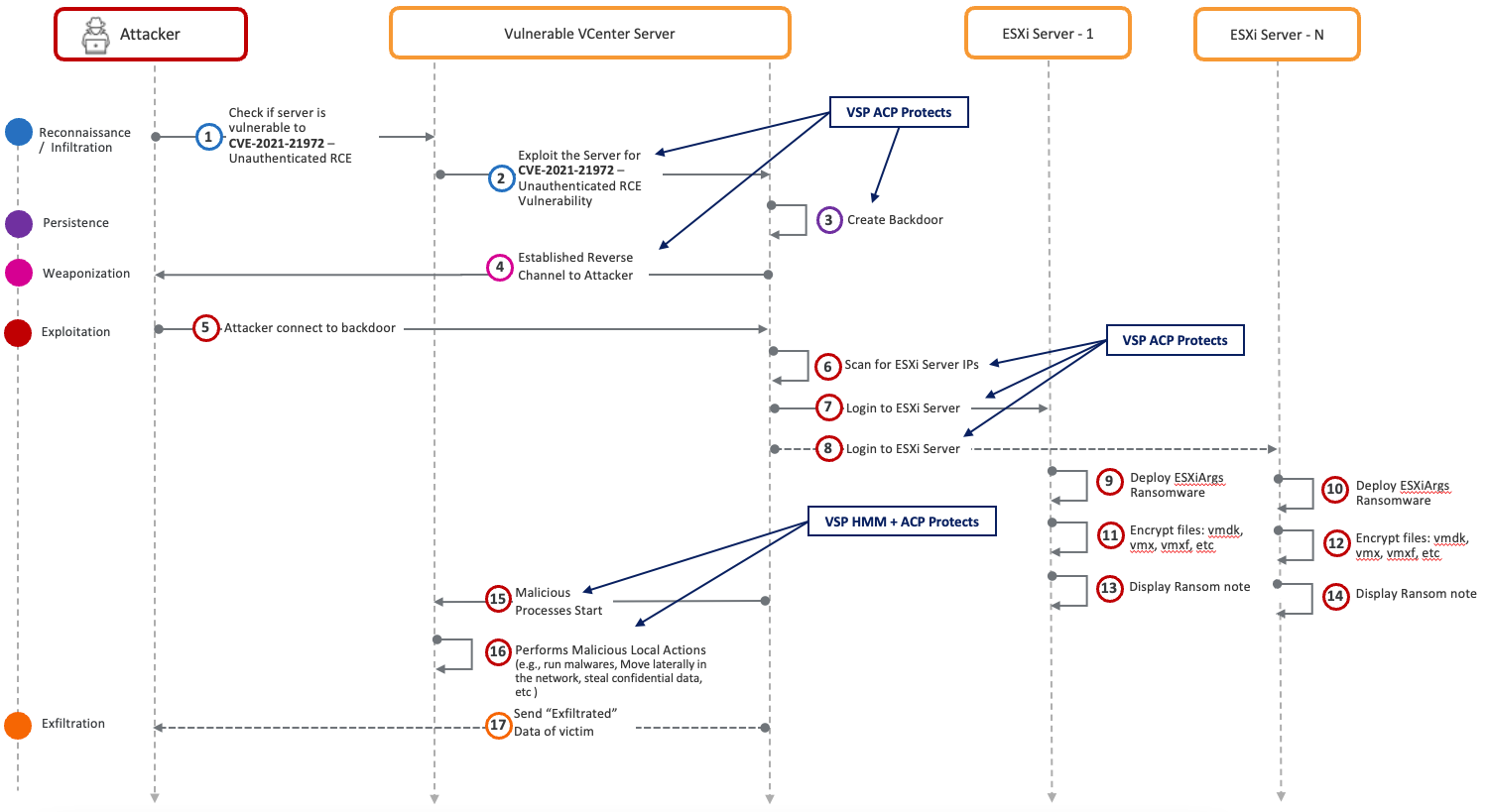
Summary: In contrast to traditional EDR solutions that rely on a "Default Allow Block on Threat" approach, the Virsec Security Platform (VSP) employs a "Positive Security (Default Deny Allow on Trust)" strategy to safeguard executables and processes running on workloads. This approach comprises two critical stages of protection. First, unauthorized code, such as malware, is prevented from initiating execution. Second, in cases where a Threat Actor manipulates a vulnerable authorized application into running attacker-influenced code, VSP detects the deviation from the app's secure execution path and immediately halts execution. This approach ensures Threat Actors have zero dwell time on the targeted workload, even if they gained initial access with compromised credentials.
For more information about the Virsec Security Platform (VSP) and how we protect vulnerable legacy workloads, visit www.virsec.com.
Don't miss our security insights, and subscribe to our blog now.