Data Center Knowledge, May 15, 2019, with comments by Satya Gupta;
Experts say exploits would be sophisticated and take a long time to build, but operators should act now.
Yesterday more news of another Intel chip vulnerability was revealed where attackers can grab sensitive data while processes are running. Nearly all Intel chips manufactured in the last ten years are affected by the flaw, so machines with Intel chips are at risk. Most at risk are multi-user environments, such as virtualized servers in data centers.
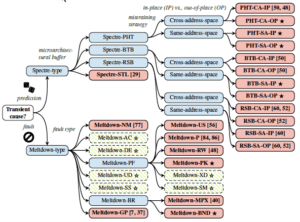
“ZombieLoad” is the common name given to the vulnerability and researchers have already discovered and coined names for variants, Fallout and RIDL.
How can you protect yourself against ZombieLoad?
Choosing a practical moniker, Intel refers to the flaw as ‘Microarchitectural Data Sampling.’ They say they’ve already addressed the issue at the hardware level for many eighth- and ninth-generation Intel Core processors, as well as for the second-generation Intel Xeon scalable processor family. Leigh Rosenwald, their spokesperson, has said they’ve provided mitigation for other products through microcode updates combined with corresponding OS and hypervisor updates. Additional information is available at their Deep Dive page.
Intel has also released a patch, but a patch would need to be applied to operating systems, hypervisors and individual apps. This is especially true for multi-user environments, which again are the most at risk. This is in part because the status of parts of these multi-tenant systems is unknown – and possibly patches can’t be applied across the board. An Intel spokesperson has revealed that if the patch is applied, data centers can expect up to a 9% performance hit. This is reminiscent of the Spectre/Meltdown remediation efforts. Apple, Microsoft and Google have also released patches, likely with similar affect.
How quickly could a ZombieLoad attack strike?
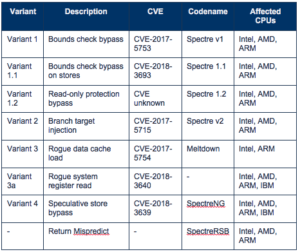
This is the latest in an ongoing run of side-channel types of attacks, starting with Spectre and Meltdown in January of 2018. (See our blog, Similar to Spectre yet Different, Spoiler Is a New Threat Impacting All Intel Chips). With awareness going back at least that far, organizations have had time to begin mounting their defense against such attacks.
With the disclosure of the threat yesterday, researchers included proof-of-concept code. If threat actors weren’t already aware of this vulnerability, they are now. If they’ve started developing attacks targeting Spectre, Meltdown or ForeShadow, vulnerabilities, they have an even longer head start. Whether bonafide attacks will come in days, weeks or months isn’t known, but they always seem to come sooner than expected.
Watch for Exposure in Computing-as-a-Service (CaaS) Environments
Satya Gupta, founder and CTO at Virsec Systems talked with Data Center Knowledge about ZombieLoad, saying, “Data center operators providing computing as a service should make sure information about their vulnerable assets doesn't leak, since anyone using shared infrastructure could be exposed. In some environments, it might be difficult or costly to shut down servers to do the upgrades. It's not as easy in the cloud to go and do a reboot. Lots of critical workloads could be operating on the shared infrastructure."
Gupta added, "If you have two programs, one trusted and one not so trusted, then every time you switch between the programs you should flush the internal states," said Gupta. "There's a microcode update that Intel has provided."
Another recommendation as an additional mitigation is for application developers to clear buffers, but this could slow operations down.
You can check if your system is vulnerable
The researchers behind the exposure of this design flaw operate from multiple locations: the Graz University of Technology, Vrije Universiteit Amsterdam, the University of Michigan, the University of Adelaide, KU Leuven in Belgium, Worcester Polytechnic Institute, Saarland University in Germany, and security firms Cyberus, BitDefender, Qihoo360, and Oracle.
One of these, the Vrije Universiteit Amsterdam has provided a tool for organizations to check their own systems for the vulnerability: Check for Intel vulnerability in your system.
Read full ZombieLoad Affects Data Centers article.
Further resources:
Blogs:
Similar to Spectre yet Different, Spoiler Is a New Threat that Impacts All Intel Chips
Spectre Will Haunt Us for a Long Time
2-minute Video: Virsec Overview: Protecting Against Advanced Cyberattacks