The Gartner EDR Market Guide for Cloud Workload Protection Platforms addresses what industry professionals should look for in a cloud workload protection platform. After reviewing the guide and evaluating, two things remain clear—protection must span development and runtime and should include aspects of cloud security posture management.
Virsec Security Platform (VSP) was recognized as a Gartner Representative Vendor as a part of this Market Guide, furthering Virsec’s market validation in the Cloud Workload Protection Platform (CWPP) space.
Gartner Market Guide Best Practices
Legacy Support: When using operating systems that are no longer supported by their providers (like Windows Server 2008), Gartner affirms that when exploring CWPP solutions, security professionals: “require support for those OSs, …and compensating controls if the system is unpatched.”
Single offering: Gartner recommends looking for offerings that protect physical machines, VMs, containers, and serverless workloads — all managed from a single console, regardless of the location of the workloads and their granularity.
Solid Container Support: Vendors should have mature container image support and looking to implement serverless function scanning and protection in the near future if not already.
Flexible deployment: CWPP vendors should support alternative deployment options, including privileged containers, Kubernetes DaemonSets, sidecars, and emerging options for disk image analysis (typically via snapshotting.
Urgency: Security and risk management leaders are now advised to implement CWPP for all workloads or application architectures, not just tier-1 apps.
DevSecOps: Pre-deployment workload scanning and compliance efforts in DevSecOps, especially for container-based and serverless functions
In the future: If using Kubernetes and considering a managed Kubernetes service, make explicit support of this environment a requirement as well.
While the CWPP acronym might not roll off the tongue, Cloud Workload Protection Platforms are rapidly emerging as an important category as businesses of all types aggressively move critical applications to the cloud. What used to be largely on-premises servers running business applications is quickly changing to a hybrid mix of virtual machines, containers, and eventually serverless workloads.
It’s a cliché to say that the cloud changes everything, but with security strategies it’s quite true. As businesses move applications to the cloud, the bulk of existing network security investments – firewalls, AV, IPS, WAFs and other network protection tools, become much less relevant. Because you’re outsourcing network infrastructure, you should expect legitimate cloud providers to manage most network security functions, and let you focus on protecting your business-specific applications.
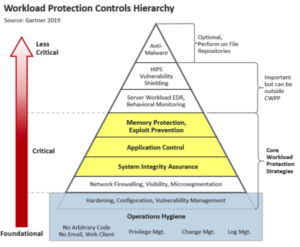
The Gartner market guide includes a framework diagram that categorizes and ranks security controls needed to protect cloud workloads. In this pyramid, the top is the least critical, while the lower areas are both more critical and foundational. In fact, the top three tiers (anti-malware, HIPS, and EDR) are listed as “Important – but may be performed outside the workload.”
100% 0Prevention
42% 8Prevention
Virsec Security Platform
Leading EDR
Gartner takes a strong position on the importance of memory protection/exploit prevention stating definitively that “We consider this a mandatory capability.” By exploiting application vulnerabilities, attackers can inject malicious code that runs entirely from memory – a fileless attack technique that easily bypasses conventional security controls. As we’ve seen repeatedly with memory attacks like WannaCry, NotPetya, and Apache Struts, memory exploits made these attacks nearly indefensible.
While the report categorizes over 40 vendors by their capabilities, only four were recognized for Memory and Process Integrity/Protection including Virsec. We are pleased to be included in this select list and welcome more entrants into this important space. However, as you assess memory protection solutions, it’s important to keep this in mind:
- Multiple endpoint protection vendors make claims that they also protect memory, yet Gartner does not recognize any of them.
- You can’t protect memory from the outside. Perimeter security is easily bypassed with fileless techniques, and post-execution detection/response tools are too late and miss the transient nature of well-crafted memory attacks that don’t leave clues behind.
- To detect and stop memory attacks, products like Virsec uniquely extracts the intent of an application, then monitors actual code execution in memory and deterministically spots deviations from correct application execution within milliseconds
Virsec Capabilities
Other solutions that rely on analysis generate so many false positive alerts that it overwhelms teams. With a positive security model and automated allow listing, you can protect legacy systems AND avoid all the alert fatigue.
