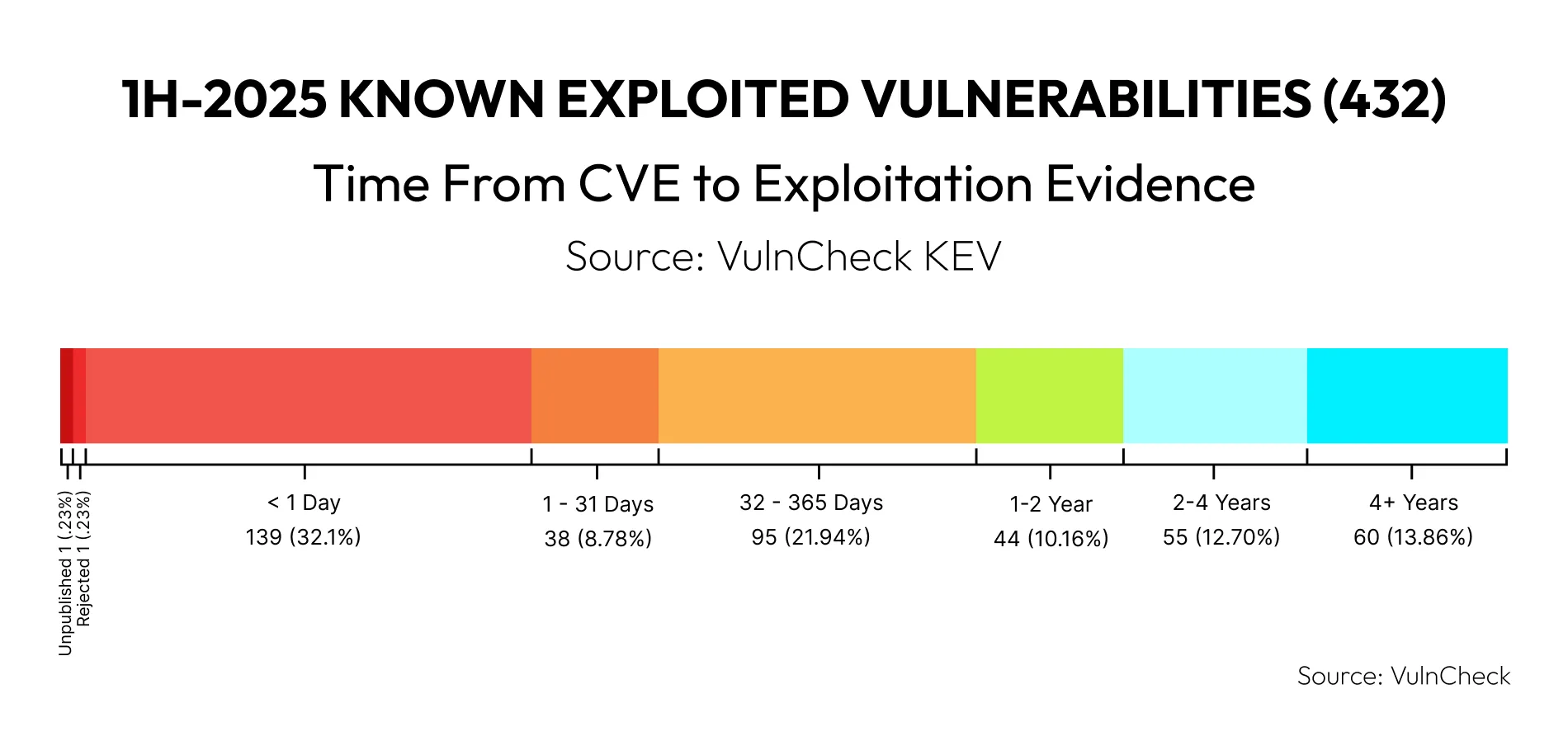
An unpatched vulnerability today is likely to become a breach within weeks. Attackers routinely weaponize new vulnerabilities in less than 48 hours, while most companies take weeks or months to patch. During this delay, mission-critical workloads remain exposed. The 2025 DBIR report found that vulnerability exploitation is the initial access method in 20% of breaches.
This is the harsh reality for enterprise security teams:
- Vulnerability overload: Thousands of CVEs are published yearly, far more than any security team can address.
- Patch delays: Installation cycles get bogged down with testing requirements, operational constraints, or vendor delays.
- Exploitation speed: Exploits for critical CVEs appear within hours of public disclosure.
Such a dangerous mismatch is why a vulnerability mitigation process is a must. Instead of relying solely on delayed patches, enterprises need a way to:
- Shrink the attack surface immediately.
- Neutralize vulnerabilities at runtime, before exploitation.
- Buy time for remediation without business disruption.
What Is Vulnerability Mitigation?
Vulnerability mitigation refers to reducing the risk of exploitation of a vulnerability by implementing controls or safeguards, even if the underlying flaw is not fully fixed.
Unlike remediation, which involves patching or rewriting code to remove the bug permanently, mitigation can take different forms, with one key focus being the ability to block attacker exploits in real time. In other words:
- Mitigation = make the vulnerability unexploitable now.
- Remediation = fix the vulnerability’s root cause later.
This distinction matters because
- Patching lags: It may take weeks or months to deploy patches across a global infrastructure.
- Zero-days exist: Exploits often hit before any vendor patch is available.
- Legacy systems endure: Vendors stop releasing patches, but those systems still run mission-critical workloads.
4 Main Reasons Why We Need the Vulnerability Mitigation Process
Every security team struggles with more than just closing vulnerabilities. They face a torrent of alerts, lagging patch cycles, and adversaries who are ready to take advantage of any delay. The following challenges show why standard approaches fall short.
Alert Fatigue and Dashboard Noise
Common tools produce vast lists of open CVEs, many of which turn out to be irrelevant or non-exploitable. Unfortunately, meaningful, risk-based prioritization typically gets lost. This cycle breeds alert fatigue, distracts focus from actionable threats, and ultimately allows serious risks to evade scrutiny.
The SolarWinds breach in 2020 made this problem visible at scale: attackers slipped a Trojanized update past monitoring systems, leveraging trusted infrastructure to stay invisible. Teams received no warnings because the threat hid within legitimate activity, demonstrating the limitations of detection-centric dashboards.
Delayed Patching Creates High-Risk Windows
The patching process is rarely immediate or frictionless. Even after vendors release security fixes, organizations must vet each patch for compatibility, schedule deployment windows to minimize downtime, and secure approvals across operations. This results in prolonged exposure management—often 30 to 90 days—during which attackers actively target known vulnerabilities.
The Hafnium attacks on Microsoft Exchange servers in 2021 serve as a reminder of this: despite rapid patch availability, tens of thousands of systems suffered breaches as adversaries exploited the delays inherent in manual remediation pipelines. The core issue wasn’t the lack of patches, but the time it took to close the window between disclosure and effective remediation.
Vulnerability Chaining: Multiplying the Damage
Attackers chain together multiple weaknesses to maximize impact. Threats like PrintNightmare, NotPetya, and Log4Shell exemplify this, combining exploits to maintain persistence, escalate privileges, and traverse network boundaries.
Legacy Systems: The Unpatchable Problem
Business-critical applications still depend on legacy technologies that are either unsupported or too fragile to update. In healthcare, for example, many providers still operate essential infrastructure—MRI machines, diagnostic analyzers, emergency systems—on outdated Windows servers. Such systems routinely remain exposed to wormable exploits like EternalBlue, since necessary patches risk catastrophic downtime or operational failure.
Attackers recognize legacy environment vulnerabilities and continuously scan for opportunities, knowing that operational constraints prohibit modern defensive measures.
Each of the breaches mentioned above had a common denominator: a vulnerability window between discovery and full patch deployment. Mitigation-first security closes that window—instantly.
Why Mitigation Must Come First in a Modern Security Strategy
You can’t patch faster than adversaries can weaponize vulnerabilities. Even when patches exist, operational constraints delay deployment. Attackers exploit that delay, with the gap ending only when you introduce runtime mitigation as the first line of defense.
A mitigation-first approach, that neutralizes threats at runtime, makes them unexploitable. It doesn’t replace remediation but enables it by:
- Neutralizing threats immediately, no matter whether a patch exists.
- Preventing exploits from executing.
- Giving your team breathing room to remediate at its own pace.
The Step-by-Step Vulnerability Mitigation Process
Let’s look at the guided vulnerability mitigation process offered by OTTOGUARD.AI. This is designed for autonomous workload protection without patching.
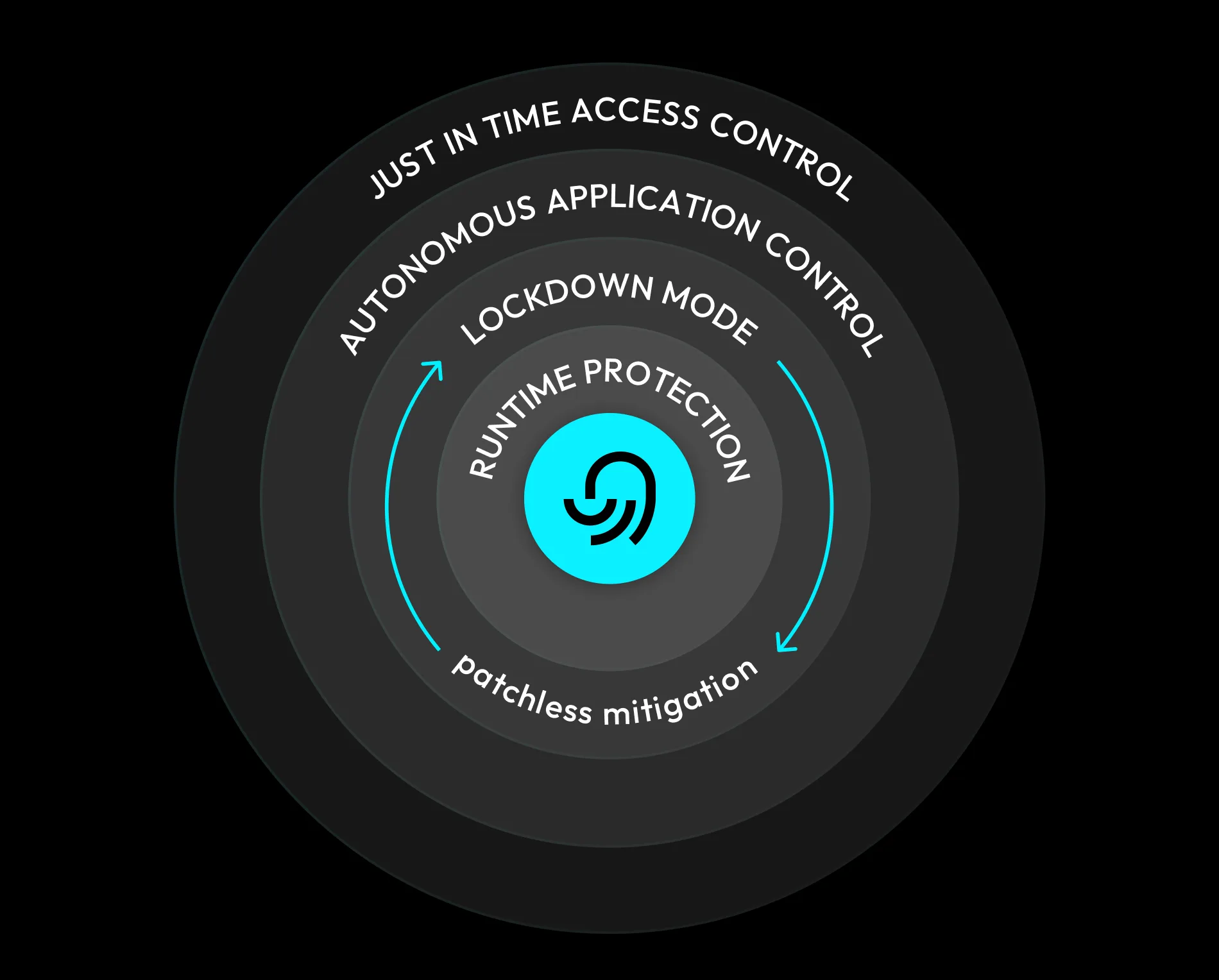
Step 1: Enforce Runtime Protection at the Core of the Mitigation Process
Visibility matters, but enforcement is where risk reduction happens. Traditional vulnerability management waits for detection; runtime protection prevents the exploit.
OTTOGUARD.AI deterministic enforcement means:
- It maps your application’s legitimate execution flow.
- Anything that deviates—buffer overflow, injected DLL, malicious payload—is stopped in milliseconds.
- There is no “maybe” or probability score. Execution is either trusted or blocked.
This binary decision-making eliminates the gray areas that attackers target. Exploits like ransomware loaders or supply chain trojans cannot “live off the land” when runtime behavior is locked down.
Step 2: Apply Autonomous, Patchless Mitigation to Stop Exploits Instantly
Every vulnerability has two parts: the flaw in code and the exploit that attempts to trigger it. OTTOGUARD.AI blocks the exploit, even if the vulnerability remains.
This means vulnerabilities, both known CVEs and zero-days, become non-exploitable at runtime.
The benefits:
- No emergency patch fire drills.
- No downtime waiting for vendor patches.
- Protection even when patches are months away—or don’t come at all.
This is workload patchless mitigation in action. Threat actors find the door closed, even if the lock itself is broken in the original code.
Step 3: Apply Just-in-Time Access and Restrict Privileges
Vulnerability exploitation is often just the start. Attackers pivot through systems using stolen or overprivileged credentials. Privilege controls are part of the mitigation process.
OTTOGUARD.AI enables Just-in-Time access, granting credentials only when needed and revoking them immediately afterward. This shrinks the privilege window, reducing opportunities for lateral movement or privilege escalation attacks.
Step 4: Automate Defense, Reduce Alert Fatigue
Manual vulnerability workflows cannot scale. Teams are overburdened with patch notifications, vendor advisories, and CVE scoring.
OTTOGUARD.AI’s agentic AI is purpose-built and trained on specialized cybersecurity data, enabling it to deliver rapid, consistent, and highly accurate results—far exceeding human capabilities for these tasks. Achieving such reliability requires continuous model training, data refinement, and strong feedback loops. The system also uses prompts and clarifying questions to refine ambiguous queries, ensuring precise and relevant outcomes.
AI agents maintain strict control over data quality, earning user trust and acting as competent security experts without alert fatigue. These agents process petabytes of data 24/7 with unwavering vigilance, reducing the risk of missed threats compared to human-only teams.
- Deploy protection autonomously.
- Integrate with scanners and ITSM ticketing.
- Streamline incident reporting for auditors.
This reduces alert fatigue and ensures mitigation scales alongside vulnerability growth.
Step 5: Audit, Report, and Prove Security Maturity
Boards and regulators demand proof of risk reduction. A step-by-step vulnerability mitigation process must deliver auditable evidence.
Key success metrics include:
- % of vulnerabilities mitigated in runtime.
- Zero dwell time: no window between exploit attempt and block.
- Zero MTTR: vulnerabilities made unexploitable instantly, no patch delay.
- Fewer successful attacks and reduced patch backlog.
OTTOGUARD.AI enables this reporting automatically, providing compliance-ready evidence to auditors and giving CISOs board-level visibility into enterprise exposure posture.
The Business Benefits of an Optimized Vulnerability Mitigation Process
Executives care about outcomes: operational resilience, reduced risk, and cost savings. Thanks to optimizing the mitigation process, they ensure:
- Safety from zero-day attacks even before patches exist.
- Critical vulnerability reduction off the bat.
- Shielding for legacy/end-of-life systems that cannot be modernized.
- Reduced risk of downtime or business disruption.
- Lower operational overhead with fewer fire drills and fewer “all-hands patch weekends.”
- Transparent proof of compliance via measurable KPIs.
To dive deeper, explore the comparison of the best vulnerability mitigation tools.
Why OTTOGUARD.AI Improves the Vulnerability Mitigation Process
OTTOGUARD.AI doesn’t chase threats and scores or operate with probabilities. It stops attacks at the source, delivering:
- Patchless Mitigation: Vulnerabilities cannot be exploited.
- Deterministic Runtime Protection: Binary enforcement of application behavior.
- Zero MTTR: Immediate remediation through making vulnerabilities inert.
- Zero Dwell Time: Attacks blocked before lateral movement or encryption.
- Autonomy and Automation at Scale: Limits human dependency and alert fatigue.
- Proof of Security: Boards, regulators, and CISOs can measure exposure reductions directly.
The vulnerability backlog is unmanageable. Once you embrace the modern vulnerability mitigation process, you close the exploit window promptly, neutralizing vulnerabilities before they become a problem. Remediation then follows on your terms.
Book a demo and see how OTTOGUARD.AI’s autonomous, workload-level patchless mitigation reduces your critical vulnerabilities.
Frequently Asked Questions
Mitigation and remediation complement each other, but they operate differently:
- Mitigation: Protects workloads immediately by making exploits inert. Vulnerabilities may still exist in the code, but exploit attempts cannot succeed.
- Remediation: Permanently addresses the root cause through a patch, code refactor, or replacement of the vulnerable component.
OTTOGUARD.AI espouses the philosophy of “mitigate first, manage later.” By neutralizing vulnerabilities at runtime with patchless mitigation, OTTOGUARD.AI closes the exploit window immediately. Security teams then patch and remediate systems on their timeline, without risking downtime, rushed deployments, or exposure during prolonged patch cycles.
Runtime protection sits at the core of patchless vulnerability mitigation. It enforces exactly how an application is supposed to behave. Any deviation is immediately blocked.
Runtime protection delivers deterministic precision in real time. OTTOGUARD.AI exemplifies this model by using patented zero-trust enforcement to protect workloads continuously. It defines what “good” looks like and eliminates everything else, creating binary enforcement: valid code runs, exploits do not.
This approach closes the gap that attackers exploit between disclosure and patching, protecting workloads from zero-days, ransomware droppers, and supply chain attacks.
Yes. Legacy and end-of-life systems often cannot be patched, either because vendors ended support years ago or because downtime would cripple critical operations. These workloads remain deeply embedded in healthcare, financial services, and industrial environments, making them prime targets.
Patchless mitigation provides the optimal protection in these environments. It shields legacy applications while blocking exploit execution altogether. Even if vulnerabilities exist in unmaintained or outdated code, attackers cannot weaponize them. This effectively extends the secure life cycle of outdated software, ensuring resilience without business disruption.
Emergency patch rollouts can cause more disruption than the vulnerabilities themselves. Application owners worry about broken functionality, failed integrations, or service outages. As a result, patching gets delayed, leaving vulnerabilities exposed.
When mitigating vulnerabilities at runtime, you remove the need for crisis-driven patching. OTTOGUARD.AI’s deterministic runtime protection neutralizes exploitation attempts in milliseconds, meaning applications remain secure and online. This delivers zero MTTR and allows organizations to patch methodically during planned maintenance instead of doing so in breach-induced panic.
Yes. Zero-day vulnerabilities represent the most dangerous exploits because vendors haven’t yet issued patches and threat actors can often exploit them quickly. Traditional defenses that depend on known signatures or Indicators of Compromise (IOCs) can’t help, because there are no known patterns to match.
It eliminates the attacker’s opportunity window by stopping exploits before they execute. Unlike solutions that depend on patch availability or post-execution detection, OTTOGUARD.AI enforces deterministic runtime protection at the workload level.
Key reasons enterprises choose OTTOGUARD.AI include:
- Patchless Mitigation: Neutralizes vulnerabilities immediately, without waiting for vendor patches.
- Zero-Day Protection: Blocks unknown threats that lack signatures or threat intel.
- Legacy System Defense: Secures unsupported and critical systems beyond vendor life cycles.
- Exposure Reduction: Shrinks the attack surface by 90% and cuts alert fatigue.
- Zero MTTR: Turns remediation into prompt mitigation.




