SearchSecurity, November 15, 2017; comments by Satya Gupta;
A Proof of Concept Exploit Demonstrates Hackable Vulnerability
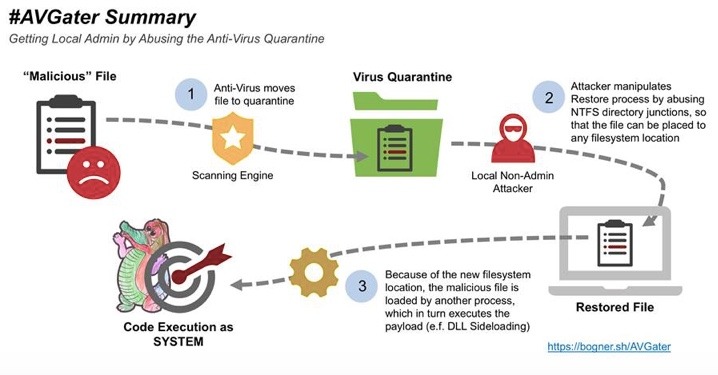
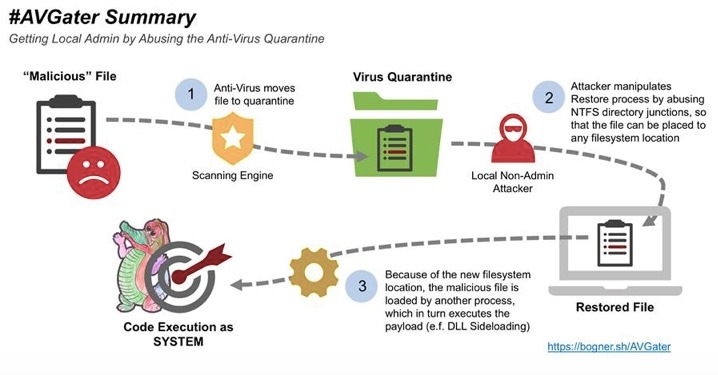
A security researcher in Vienna, Florian Bogner, has recently discovered a “proof of concept” exploit that’s affecting multiple anti-virus products and has the power to completely take over a system. Such proof of concept exploits carry out attacks on computers or networks simply to prove that vulnerabilities can be hacked. And this is now proven.
Named AVGater, the exploit manipulates the virus quarantine restore process. Previously quarantined files can be written to arbitrary system locations and the malicious library is placed in a folder where the current user logged is normally not able to access.
Bogner reports he disclosed the AVGater vulnerability to a number of companies, including Trend Micro, Kaspersky Lab, Check Point and more. Bogner recommends, among other preventative actions, that users should be blocked from restoring identified threats.
Satya Gupta, founder and CTO at Virsec Systems, tells SearchSecurity that “AVGater is yet another way an attacker could manipulate legitimate processes to launch malicious code or scripts."
Gupta continues, "It's also another nail in the coffin for conventional signature-based antivirus solutions. We've known for a while that fileless and memory-based exploits fly under the radar of most AV systems, but now hackers can use AV tools to essentially disable themselves. Hackers are relentless and will inevitably find clever ways to bypass perimeter security. The battle has to move to protecting the integrity of applications for process and memory exploits."
Virsec is an application threat software company based in San Jose, Calif.
Read the full AVGater Abuses AV Software for Local System Takeover article