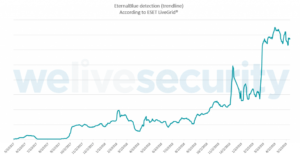
Attack attempts involving EternalBlue now number in the hundreds of thousands daily
WannaCry (aka WannaCryptor) struck two years ago. EternalBlue was the destructive exploit at the heart of this ransomware that shocked organizations and wreaked extensive havoc. It’s believed EternalBlue was released into the wild by a mysterious group known as The Shadow Brokers in the Spring of 2017, which they reportedly stole from National Security Agency (NSA) in 2016. (It’s possible EternalBlue and other exploits were used even before the Shadow Broker’s release – See our blog, Chinese Hacking Group, Buckeye, Used Stolen NSA Hacking Tools Ahead of Shadow Brokers’ Leaks).
Regardless of how early EternalBlue was used, it continues to rise and even mushroom. This exploit is now so popular that the number of times bad actors use it is now numbering in the hundreds of thousands of attacks per day.
EternalBlue hits Microsoft’s Server Message Block (SMB)
EternalBlue strikes at a vulnerability in the Microsoft Server Message Block (SMB) 1.0, the network file sharing protocol that allows the computer applications to read and write to files and request services on the same network. EternalBlue targets this protocol via port 445 which is exposed to the Internet. Through this port, EternalBlue can spread from computer to computer and device to device on a network.
Millions of businesses remain vulnerable
Microsoft patched the vulnerability in 2017 before the WannaCry outbreak. But even now, like then, many still haven’t implemented the patch. The estimate is that nearly a million machines that remain exposed, still using the obsolete 1.0 protocol and giving WannaCry an easy pathway to spread. Most of these at-risk devices are in the US, Japan and the Russian Federation. The Top Ten countries where businesses are still most at risk with an unpatched Microsoft vulnerability are:
- US
- Japan
- Russian Federation
- Germany
- Taiwan
- China
- United Kingdom
- Netherlands
- Hong Kong
- Singapore
Businesses that don’t keep up with patching contributes to EternalBlue’s growth since appearing on the world stage in 2017 (or before). The figure below shows the rise of instances being blocked daily.
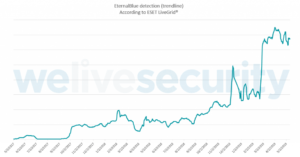
Figure Source: www.welivesecurity.com
EternalBlue is responsible for multiple bad acts
WannaCry is the most infamous attack EternalBlue has powered, but the exploit has been behind others that have made headlines too, such as, Diskcoder.C (Petya, NotPetya, ExPetya), and the BadRabbit attack in late 2017. It’s been behind cyber-spying efforts and spreading Trojans and cryptomining malware in China. The exploit has also been advertised as a black-hat tool for propagating Yatron, a Ransomware-as-a-Service.
In light of these threats, timely patching is always recommended. But for many, such as critical infrastructure systems, it’s not simple and often not even possible (See our blog, Patching the Iron Tail Is Easier Said Than Done, In such cases, it’s even more critical to address the vulnerabilities that unpatched systems present, and to build a layered approach to security capable of proactively protecting against these kinds of advanced attacks.
Further resources:
Blogs:
Chinese Hacking Group, Buckeye, Used Stolen NSA Hacking Tools Ahead of Shadow Brokers’ Leaks
White paper: How The Shadow Brokers Have Permanently Changed The Cybersecurity Landscape
Newsletter: Latest issue
2-minute Video: Virsec Overview: Protecting Against Advanced Cyberattacks