The following sections present an “everything you wanted to know but were afraid to ask” guide to vulnerability and exposure management.
What is vulnerability management? What is exposure management? How do they differ? Do they have something in common? Is a strong security posture possible without them? Can they coexist? If yes, is there something still missing from the picture?
These questions are about to be answered, so buckle up for a closer look at the details.
What Is Exposure Management?
Definitions. We’re not fans. At best, they sound like a PA announcement—helpful but rigid as iron statues. At worst, they’re like fourth-graders reciting the lecture they have learned by heart. Nevertheless, an explanation of the key terms we use will help with understanding later on.
Definition and Key Concepts
In cybersecurity, to manage exposure means to know, evaluate, and address the security risks in your environment. A security risk is a weakness that exposes your assets and networks to threat actors’ exploitation. When we say assets, we mean systems, applications, devices, and data.

These weaknesses can take the form of technical or business logic flaws, unnecessary open ports or services, reused passwords, unmanaged devices, misconfigured servers, weak encryption, bugs in code — the list goes on. Clearly, in this case, the term “exposure” can also be used in its plural form, “exposures,” to refer to all those diverse security issues.
A natural evolution of exposure management is Continuous Threat Exposure Management (CTEM), a concept developed by Gartner. CTEM emphasizes the ongoing nature of managing exposures and, crucially, integrates threat intelligence to focus on weaknesses that are actively being targeted or are likely to be exploited by threat actors.
What is the goal of exposure management?
In a nutshell, the goal is a reduced attack surface. You want as few entry points and exploitable weaknesses as possible. But not at any cost — what we’re saying is that the lowest number of, say, security vulnerabilities is not the sole goal. Rather, it’s the lowest number of exploitable vulnerabilities damaging to your vertical, daily operations, and organization.
Take, for example, a CVE vulnerability with a critically high severity score that plagues telcos. If you’re a medical provider, it will present a much lower risk to your organization than a known exploitable vulnerability with a medium severity score plaguing healthcare.
How does exposure management achieve its goal?
Since reducing your attack surface is not a one-time thing, exposure management requires continuous effort and structured processes.
Proactive real-time monitoring, vulnerability scanning, penetration testing, and red team exercises can all be part of exposure management. The same applies to mitigation, security patching, regular updating, configuring firewalls, securing endpoints, and protecting server workloads. And let’s not forget to mention assessing risk and establishing a risk tolerance threshold.

It’s worth noting that the security of the software supply chain and legacy software is also part of threat exposure management, as its goal is to reduce the overall threat exposure, that is, the entire attack surface. That includes the third-party components and nested dependencies, as well as end-of-life systems and outdated software in your environment.
Why Exposure Management Is Crucial for Cybersecurity
The principal reason for this is because exposure management goes farther, broader, and deeper than just identifying and remediating CVE vulnerabilities. This has multiple effects:
- Exposure management addresses security gaps other than CVE (or NVD, CWE, etc.) vulnerabilities. Two examples would be weak authentication/access mechanisms and outdated encryption.
- Exposure management moves away from prioritizing vulnerabilities based on severity scores. Instead, it contextualizes security threats, meaning it helps you address them based on their exploitability and realistic impact on your organization and industry/niche.
- Exposure management doesn’t deal only with publicly known and analyzed security vulnerabilities. Instead, it strives to strengthen your security posture so that it can deal with emerging and unknown threats, such as zero days.
- Exposure management tends to be markedly proactive. Its purpose is to prevent cyberattacks, not just make your organization resilient enough to withstand them. In that spirit, cyber exposure management done right means primarily using everything that’s in your hands to deny threat actors the opportunity to breach your systems in the first place, not just reducing the impact of an attack.
What is Vulnerability Management?
Like exposure management, vulnerability management identifies, assesses, and addresses security risks, too. Unlike exposure management, the security risks it focuses on are strictly known vulnerabilities published in systems like CVE, meaning its scope is narrower.

Besides, contextualization is not typically a characteristic of vulnerability management. That means vulnerability prioritization closely follows the official severity scores, failing to consider contextual factors like real-life operational impact and confirmed exploitability.
Key Elements of Vulnerability Management
The typical vulnerability management cycle consists of multiple steps. However, the important thing to emphasize is that we’re talking about a cycle. That means vulnerability management is a continuous process.
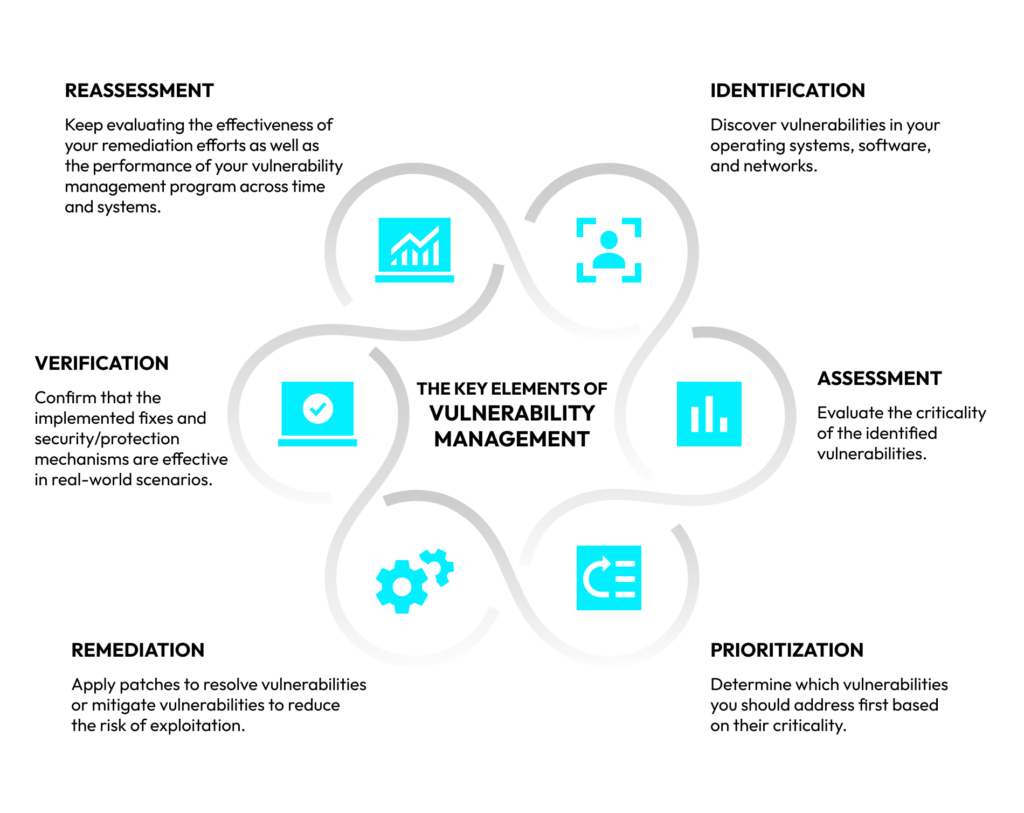
You may encounter fewer elements or different names, but these six make up a sound, generally applicable representation.
Another thing to note is that asset discovery is a prerequisite of successful vulnerability management (and, while we’re on the topic, of exposure management as well). You cannot even begin addressing the vulnerabilities in your environment if you don’t know what is there in the first place. Hence, full or comprehensive visibility in the form of a neat asset inventory is, indeed, the foundation of a good vulnerability management program.
Keep also in mind that constant updates of your vulnerability management program are understood here. New vulnerabilities are published daily, and keeping your program updated is necessary to stay current with threats, meaning you can apply proper intermittent or urgent permanent fixes. As an illustration, in 2024, 40,300 new vulnerabilities were published, and this year, in only the first few months, we’ve seen as many as 14,151 new CVE vulnerabilities.
Why Vulnerability Management Is Critical
Vulnerability management is not without flaws (more on that in the next section), but suffice it to say that it’s been around for a reason.
For starters, even if we put aside all other upsides, a vulnerability management program would still be worthwhile for the sole reason of enabling you to prevent the exploitation of known vulnerabilities. Its narrow focus on public CVEs — many of which have exploits available in frameworks like Metasploit — allows for a focused vulnerability mitigation and remediation approach.
Speaking of remediation, vulnerability management puts a strong emphasis on patching. Systems like NVD even provide references and links to vendor patch pages, download sites, security advisories, and bulletins with available fixes or remediation recommendations. As such, vulnerability management can noticeably facilitate the complex job of security and IT operations teams, along with everyone else involved in reducing an organization’s attack surface.
Reduced attack surface—that’s another benefit of vulnerability management. Although threat exposure management does this in a much more holistic fashion, vulnerability management contributes to the same overarching goal by remediating known severe CVEs.
Finally, vulnerability management allows you to meet compliance requirements, such as GDPR, HIPAA, and PCI-DSS. How? By addressing vulnerabilities that could lead to breaches, endangered user privacy, and other types of compliance violations.
The Key Differences Between Exposure Management and Vulnerability Management
The relationships between vulnerability management and exposure management are complex and manifold, which can sometimes become confusing.
On the one hand, exposure management can be considered the next step in the cybersecurity evolution, attempting to fill the gaps of traditional vulnerability management.
On the other hand, they’re both attack surface management practices, that can be seen as complementary solutions to the same problem of reducing the attack surface. In that sense, a vulnerability management program can coexist with an exposure management program in the same organization. But how is this possible?
Let’s make a side-by-side comparison first to prepare the ground, and then we’ll explain.
A Detailed Comparison
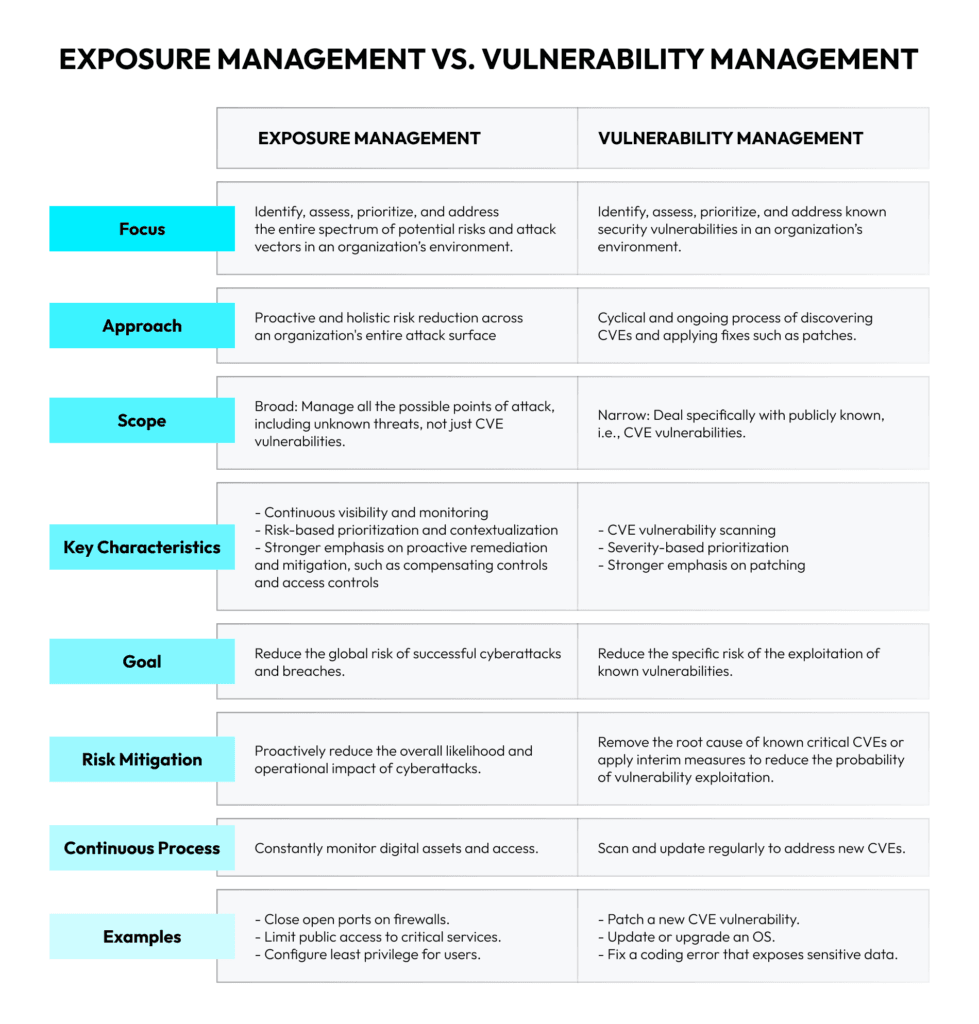
Keep in mind that comparisons like this one rarely do full justice to the realities of these frameworks. They don’t cover subtleties or overlaps that may make the factual situation much more complex. However, this table is sufficient to show the different focuses of vulnerability management and exposure management and explain why you may need both of these methods to reduce your organization’s attack surface.
How They Complement Each Other
Exposure management and vulnerability management, while distinct in their scope and methodology, are not mutually exclusive. They can jointly serve as pillars that support a single cybersecurity strategy. This role of pillars is possible primarily because they emphasize different aspects of an organization’s security posture.
Vulnerability management identifies and addresses known security vulnerabilities. It ensures that readily exploitable CVEs are patched or mitigated and reduces the risk of highly targeted attacks directed at specific vulnerabilities, fixing CVEs before attackers can exploit them. However, vulnerability management alone cannot account for all potential threats.
This is where exposure management picks up the slack. It takes a broader, holistic view, hunting for pathways that are open to compromise other than CVEs. It continuously monitors and evaluates exposures like weak credentials and shadow IT, allowing you to gain a more realistic understanding of your risk posture. The outcome is your ability to (proactively) address even those security gaps overlooked by traditional vulnerability management.
Why Managing Exposure and Vulnerabilities Is Important for Cybersecurity
There’s not much philosophy to it: If you want to prevent terrible and embarrassing cyberattacks, such as ransomware, you should manage exposure and vulnerabilities.

The Risks of Not Managing Exposure and Vulnerabilities
You may think that underlining all the things that can go wrong when neglecting the management of exposures and vulnerabilities is too harsh and unnecessary. Why not simply focus on the bright side? After all, isn’t talking about the advantages of the two practices enough to spur companies to implement them diligently?
Well, it turns out it’s not, since it is common knowledge that many organizations act only when a disaster strikes.
So, here is a short reminder of what can happen when good vulnerability and cyber exposure management programs are missing:
- Data breaches: Loss or compromise of sensitive customer data, financial information, or other confidential records
- Financial losses: Incident response and recovery costs, legal fees, regulatory fines, lost revenue, ransom payments, and decreased stock value
- Reputation damage: Loss of customer trust and loyalty, negative media coverage and public perception, hardships in attracting new customers or keeping existing ones, and lost investor confidence
- Business disruption: Inability to conduct daily business operations, system outages, and data corruption
- Intellectual property theft: Loss of trade secrets and proprietary information, and lost competitive advantage
- OT (operational technology) risks: Physical safety incidents and environmental damage
Enhancing Organizational Security Posture
Vulnerability management alone cannot be the whole story. Exposure management on its own can miss the specifics of a new vulnerability, being too consumed with the overall picture.
That is why together, these two practices provide a layered and comprehensive defense against diverse security threats — both known and unknown. And if that doesn’t improve your security posture, what would?
Virsec’s Approach to Exposure and Vulnerability Management
Virsec takes the best of both worlds — traditional vulnerability management and exposure management. But what good would that be if that were all it did? To correct the first statement, Virsec blends the best of traditional vulnerability management and exposure management but moves forward to flip the script of both. So how is this achieved?
How Virsec Combines Both Strategies
Virsec’s unique approach is embodied in OTTOGUARD.AI—the first zero-trust platform for workload patchless mitigation.
OTTOGUARD.AI is different from a regular cyber threat exposure management platform, as it provides full workload visibility. This allows organizations to monitor and control the execution of every process, executable, library, and script running on their servers. It then precisely maps the intended execution of all code, establishing a baseline of trusted runtime behavior.
By verifying known good code and behavior, OTTOGUARD.AI autonomously detects and blocks any malicious deviation or exploit attempt in milliseconds—before damage occurs. This runtime enforcement neutralizes threats stemming from both known CVE vulnerabilities (as exploits inherently deviate from the baseline) and broader exposures like misconfigurations.
Recognizing the critical role of access and identity in cyberattacks, OTTOGUARD.AI also provides just-in-time access, granting access only when necessary and for a limited time, dramatically lowering the risk of unauthorized access.
OTTOGUARD.AI fundamentally shifts the security paradigm by mitigating security gaps immediately upon deployment—applying remediation (in the form of mitigation) as the initial step of vulnerability and exposure management. This proactive approach protects assets and neutralizes threats without the need for immediate patching, reducing the Mean Time to Remediate (MTTR) to virtually zero, and eliminating the risks associated with lengthy patching cycles.

This “default-deny, allow-on-trust” model guarantees continuous workload protection and enforced application security without human intervention. Its focus on runtime integrity, deviation blocking, and patchless mitigation delivers a comprehensive security solution that transcends traditional vulnerability management and mitigation methodologies, offering a new standard in proactive cyber defense.
The Benefits of Virsec’s Mitigation-First Approach
Virsec’s comprehensive cybersecurity strategy, incorporated in OTTOGUARD.AI, delivers several key benefits:
- Faster threat detection: Detects malicious activity in milliseconds
- Quicker remediation: Addresses threats instantly through patchless mitigation
- Proactive defense: Blocks unauthorized code and process execution, including zero days and ransomware, before they gain a foothold
- Software supply chain security: Validates code integrity to prevent attacks from compromised components
- Legacy software protection: Shields legacy software and server workloads, regardless of patch availability and outdated technologies
Workload Patchless Mitigation as a Key Proactive Measure
In conclusion, vulnerability management addresses known security vulnerabilities and exposure management tackles broader weaknesses, which is why a truly robust cybersecurity strategy needs both. However, the time lag inherent in traditional remediation often leaves a critical window of opportunity for attackers.
Workload patchless mitigation builds upon the best aspects of vulnerability management and exposure management while moving forward to the immediate resolution of critical vulnerabilities and exposures. It allows you to proactively manage the entire attack surface without the headaches of the typically prolonged remediation and patching cycles. Organizations can now conduct risk management and build a stronger, more resilient security posture in a much faster and more efficient way.

FAQs
Exposure management is the continuous process of identifying, assessing, and mitigating all potential weaknesses across an organization’s entire attack surface.
Vulnerability management works through a cyclical process of identifying, assessing, prioritizing, remediating, and continuously monitoring security weaknesses in IT systems to reduce cyber risks.
Exposure management takes a broad view of all potential attack vectors across the entire digital attack surface, while vulnerability management focuses specifically on identifying and remediating known CVE vulnerabilities.
These practices are crucial because they allow you to proactively reduce the attack surface and mitigate weaknesses, minimizing the likelihood and potential impact of cyberattack




