Cloud Workload Protection Platform Report Highlights Changing Security Needs
Research firm Gartner recently released an update to its Market Guide for Cloud Workload Protection Platforms authored by influential security analyst Neil MacDonald. While the CWPP acronym might not roll off the tongue, it is rapidly emerging as an important category as businesses of all types aggressively move critical applications to the cloud. What used to be largely on-premises servers running business applications is quickly changing to a hybrid mix of virtual machines, containers, and eventually serverless workloads.
It’s a cliché to say that the cloud changes everything, but with security strategies it’s quite true. As businesses move applications to the cloud, the bulk of existing network security investments – firewalls, AV, IPS, WAFs and other network protection tools, become much less relevant. Because you’re outsourcing network infrastructure, you should expect legitimate cloud providers to manage most network security functions, and let you focus on protecting your business-specific applications.
Using Endpoint Protection Tools in the Cloud Is Risky
A central thesis of the Gartner report is that cloud deployments require very different security mindset. Assuming that your legacy security tools can make the jump to the cloud is both naïve and dangerous. Gartner also takes strong exception to the notion that conventional endpoint protection platforms (EPP) designed to protect end-user devices can be used for cloud workloads. While numerous EPP vendors claim they are cloud-ready, Gartner shuts this idea down very definitively stating: “Enterprises using EPP offerings designed solely for protecting end-user devices (e.g., desktops, laptops) for server workload protection are putting enterprise data and applications at risk.” The report goes on to say that EPP solutions “are ill-suited for the requirements of dynamic hybrid, multi-cloud workload protection. The risk profile and threat exposure of a server workload is markedly different than an end-user-facing system.”
Hierarchy of CWPP Controls
The Gartner market guide includes a framework diagram that categorizes and ranks security controls needed to protect cloud workloads. In this pyramid, the top is the least critical, while the lower areas are both more critical and foundational. In fact, the top three tiers (anti-malware, HIPS, and EDR) are listed as “Important – but may be performed outside the workload.”
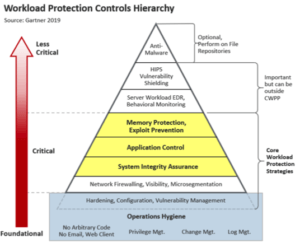
And remember, in the cloud you don’t control much outside your workload.
The base of the pyramid lists Foundational Security Controls that are critical, but should be table-stakes for most enterprises, including operations hygiene, change/log management, hardening and configuration management.
In the middle are Core Workload Protection Strategies including memory protection, application control, and system integrity assurance. These represent the biggest blind spots for most organizations. While addressing these controls is not unique to the cloud, the shift to virtualization and workloads makes these more important for your business than ever.
Don’t Forget about Memory Protection
Gartner takes a strong position on the importance of memory protection/exploit prevention stating definitively that “We consider this a mandatory capability.” By exploiting application vulnerabilities, attackers can inject malicious code that runs entirely from memory – a fileless attack technique that easily bypasses conventional security controls. As we’ve seen repeatedly with memory attacks like WannaCry, NotPetya, and Apache Struts, memory exploits made these attacks nearly indefensible.
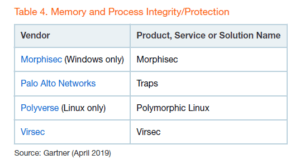
While the report categorizes over 40 vendors by their capabilities, only four were recognized for Memory and Process Integrity/Protection including Virsec. We are pleased to be included in this select list and welcome more entrants into this important space. However, as you assess memory protection solutions, it’s important to keep this in mind:
- Multiple endpoint protection vendors make claims that they also protect memory, yet Gartner does not recognize any of them.
- You can’t protect memory from the outside. Perimeter security is easily bypassed with fileless techniques, and post-execution detection/response tools are too late and miss the transient nature of well-crafted memory attacks that don’t leave clues behind.
- To detect and stop memory attacks, products like Virsec uniquely extracts the intent of an application, then monitors actual code execution in memory and deterministically spots deviations from correct application execution within milliseconds
Memory Protection Provides a Compensating Control When Patches Are Lacking
Gartner importantly points out that memory protection solutions “can be used as mitigating controls when patches are not available.” In 2018, NIST’s National Vulnerability Database (NVD) broke a dubious milestone of 20,000 CVEs reported – growing more than threefold in two years. This creates an impossible task for many enterprises, where each significant vulnerability patch can take weeks to implement and introduces new risks and uncertainties. According to a major financial services firm, each patch successfully deployed costs about $50,000.
BBy protecting any applications, patched or unpatched, Virsec delivers confidence to enterprises that application vulnerabilities, known or unknown can’t be exploited.
Application Control Should Not Depend on Whitelisting
Making sure that only the right applications execute, and they only use the right resources intended by the developer is an important concept, and Gartner endorses application control. Unfortunately, many people equate this with whitelisting, which is viewed as being unmanageable. Manually creating static lists of allowed apps and processes is impractical and doomed to failure as applications and supporting resources frequently change.
At Virsec, we wholeheartedly support the idea of making sure that applications only “do the right thing” during code execution, and solutions include critical automation to make this practical and manageable without manual IT intervention. As valid applications are loaded into memory, Virsec can automatically ensure that executables, libraries, files, and other supporting processes are valid and never change during code execution.
Security Must Travel with Your Applications
Change is the only constant in the cloud. Applications that may have run for months in on-premises servers may run for just minutes at a time in virtual and cloud environments, elastically scaling to meet peak loads, and stopped when not needed. The dynamic nature of the cloud requires security models that are equally dynamic and that can automatically deploy and follow your applications wherever they go, wherever and whenever they run. Virsec’s application security model delivers this level of flexibility and constancy.
Shifting to Application-Centric Security
Most security experts recognize that the legacy perimeter security model is outdated and increasingly irrelevant. As Gartner and others highlight, the move to the cloud is the nail in the coffin for conventional on-premises security. Firewalls, IPS, WAFs and other tools that have previously served us well, are increasingly disappearing as line items from enterprise security budgets. This trend doesn’t absolve businesses from risk and the need to protect their crown jewels. If you strip away perimeter security, what’s left are your mission-critical applications and data – often the cornerstone to your business’s reputation. Shifting our focus to protecting workloads in the cloud is an important first step.
More information about Memory Protection


