IT security researchers are always hunting to find vulnerabilities and exposures before hackers do. They’ve found one recently where a certain technique leveraging a vulnerability allows someone to disable most any antivirus solution out there, across all operating systems – Windows, Mac and Linux.
Virtually all organizations include antivirus (A/V) tools in their toolbox for thwarting malware. This remains true even though most are aware that A/V protections are no match for the malware threats plaguing systems today. Hackers have a plethora of methods for getting around A/V barriers. But even as A/V solutions still provide a defensive role, this new vulnerability takes advantages of the tool itself to create an opening attackers can seize to take control of a system.
This A/V Vulnerability Is Sneaky and Dangerous
The security specialists describe this method as a sneaky, yet easy, way a bad actor can invade a computer, regardless of OS or A/V product.
The method leverages the process all A/V scanners normally follow. When A/V software encounters a new and unknown file being saved to disk, it scans the file for malware and any content that may be suspect. Such a scan happens in real time, from seconds to minutes after the file is downloaded, depending on the A/V product and the file(s). Cleared files are good to go and files that are suspicious or deemed to contain a possible threat are deleted or put in quarantine.
Because this task is high priority, the computer OS allocates A/V products privileged access with the highest authority. And this is the aspect of A/V that threat actors can exploit. The privileged state when these A/V processes are running with highest authority presents a fundamental vulnerability. A door of access is essentially thrown open for threat actors to exploit a race condition vulnerability, which occurs when a computing system programmed to handle one task is thwarted into performing another simultaneously. The process takes advantage of a time gap.
Before file scanning begins, the specialists observed a short opening of time between the scan and when the file cleanup process would begin. This window provides opportunity for threat actors to intercept and hijack the A/V tool’s process. The race condition - a directory function in Windows, and a symbolic link on macOS and Linux systems - allows the attacker to then exploit file operation privileges to disable to A/V security tool altogether. From there, they are able to delete files the A/V product needs to function, disabling it, and OS files as well.
Attackers Can Gain Control of Windows, macOS and Linux Systems
A/V software doesn’t factor in that the small window of time between when the A/V file scan discovers a malicious file and subsequent cleanup process. That window gives opportunity turns a series of events dependent on the sequential timing into a flaw that can be taken advantage of by criminals.
For Windows, it’s a directory junction and for Linux and macOS, it’s a symlink process that uses the privileged file phenomenon to take out the A/V software or disable the OS. Once that happens, the threat actor is in control of the system.
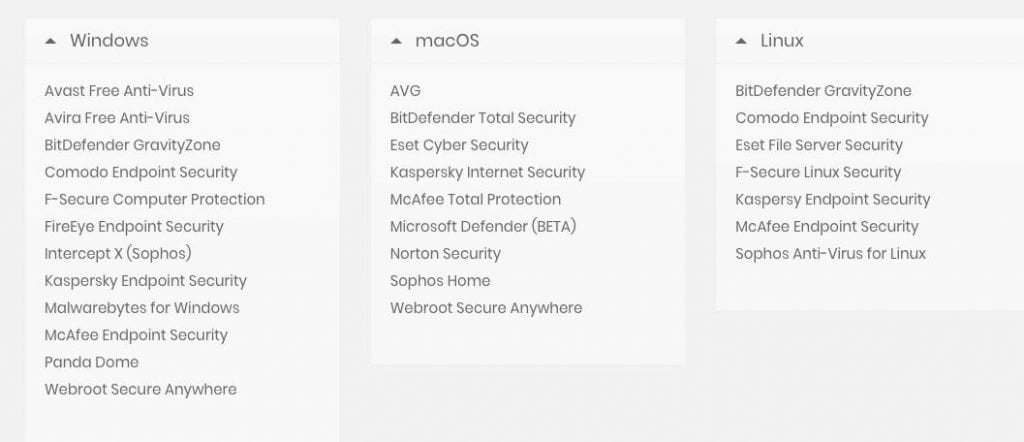
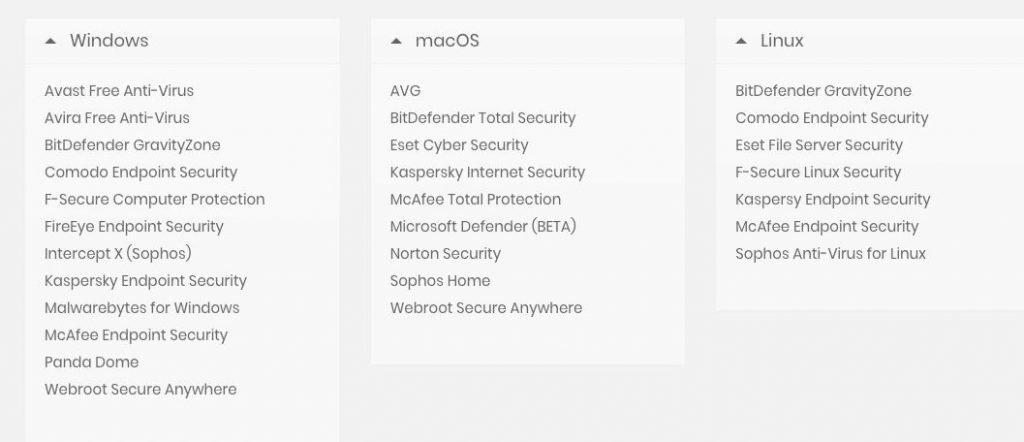
The list below contains files that can be used by this vulnerability for such an attack. The security analysts have alerted the security product developers, but status of any fixes isn’t yet known.
The hijack process described here isn’t difficult for experienced malware operators. The steps are simple enough for them, with the main challenge being striking the timing accurately as it must be precise. A second too soon or too late will fail the mission. But attackers who apply themselves won’t find it difficult to utilize the privileges skillfully enough to gain control. In some of the scenarios A/V software researchers evaluated, a loop statement was all it took to derail the A/V software – timing didn’t even factor in.
While Needed, A/V Software Not a Solution Against Today’s APT Environment
Most companies realize the benefits as well as the limitations of antivirus software. Antivirus (A/V) solutions still provide a first layer of defense that companies are wise to keep, such as blocking attacks consisting of known threats that signatures can successfully identify.
A/V Always Looks Backwards
Apart from the threats to organizations given the vulnerability outlined here, antivirus protections are limited in that they are only able to identify and stop malware that is already seen and found familiar. In that sense, A/V always functions in hindsight. The process of keeping signatures up to date can take days, weeks or months after a threat is identified, leaving a gap in protection. And because it can only recognize known threats, A/V software is not capable of blocking new and sophisticated attacks, including advanced persistent threats (APTs) such as fileless attacks. By design, these attacks are intended to bypass these signatures.
New threats get past traditional antivirus with predictable reliability, which these days includes zero-day exploits and ransomware.
Windows especially and Linux (less so macOS) are susceptible to other vulnerabilities as well (see Further resources for a few). This will always be the case given that no matter how diligent the development cycle. Attackers will always be just as diligent at finding ways to exploit software weaknesses.
Virsec Provides Integrated Protection
Virsec eases the burden of having to worry about every possible vulnerability that exists currently and will exist in the future. Rather than focusing on hindsight, or on trying to envision every future risk, Virsec’s solution premise is to focus on what your system and applications should be doing and prohibits everything else.
Unlike signature-based solutions, Virsec requires no prior insight into attack patterns or methods. Attacks on existing vulnerabilities, whether common, uncommon or unknown exploits, are detected automatically. Because application security is absolutely defined, at the code and memory level, no matter what method or entry point an attacker uses, the application can run only its intended functions.
Virsec helps organizations protect high-valued applications by ensuring an effective defense against increasingly advanced application attacks.
Further resources
Solution Brief: Protection Against Advanced Web Attacks
Why the best antivirus software isn’t enough (and why you still need it)
ACBackdoor malware targets Windows/Linux users
Revisiting the glibc Vulnerability
Avgater abuses antivirus software for local system takeover
White Paper: Deterministic Protection Against Fileless and Memory-Based Attacks
White Paper: Making Applications Truly Self-Defending
Sources
https://www.rack911labs.com/research/exploiting-almost-every-antivirus-software/