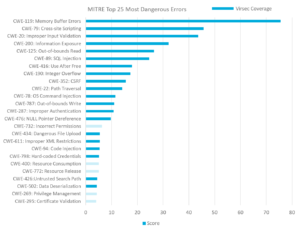
With data threats rising, memory buffer errors present the biggest threat to organizations
MITRE has released a new list of the Top 25 Most Dangerous Software Errors, and a type of memory buffer error tops the list, with by far the highest risk score. While many organizations have been complacent about the risks of memory-based cyberattacks, this new report provides a stark wake-up call.
The non-profit’s report is based on the Common Weakness Enumeration (CWE) catalog which compiles and categorizes software bugs, errors and potential attacks that developers and security professionals should be monitoring. This year’s report – the first update since 2011 – is unique in that MITRE has ranked and weighted these risks. While the previous version used more subjective survey data, the new report uses a scoring algorithm based on the NIST National Vulnerability Database (NVD) and the Common Vulnerability Scoring System (CVSS), with analysis of over 25,000 CVEs.
The Most Dangerous, Exploitable Threat Is a Memory Buffer Error, Followed by Cross-Site Scripting (XSS)
By far the most dangerous error, according to MITRE, is CWE-119, labeled "Improper Restriction of Operations within the Bounds of a Memory Buffer." This bug allows code to read or write data outside of the buffer’s boundaries. This single risk accounted for almost 20% of the total risk score for all the top 25. Coming in second is CWE-79, the "Improper Neutralization of Input During Web Page Generation" -- also known as cross-site scripting (XSS).
The new MITRE list highlights the most widespread and critical weaknesses that can lead to serious vulnerabilities in software. According to MITRE, “These weaknesses are often easy to find and exploit. They are dangerous because they will frequently allow adversaries to completely take over execution of software, steal data, or prevent the software from working.”
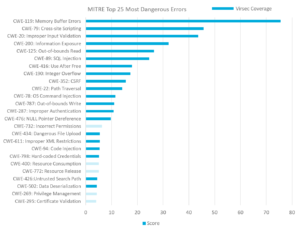
Memory and Web Threats Make Up Nearly 80% of Critical Risks
The top 10 errors, which account for almost 80% of the total weighted risk are all related to advanced memory or web threats. Roughly 40% of the entire weighted score is related to memory-based risks, while 51% is related to web threats, with the remainder a mix of host and access control issues.
Virsec is the only vendor that provides complete protection across the full application stack including the web, memory and host layers. Mapping coverage to the new MITRE list, Virsec provides:
- Complete coverage for MITRE’s top 10 errors
- Coverage for errors that account for 94% of the total risk scores
- Full coverage for all the Memory and Web errors listed, accounting for 92% of the total risk
- Coverage for 20 out of top 25 most dangerous errors listed
These risks are not new, but we welcome MITRE’s efforts to focus attention on the most dangerous flaws, as many organizations struggle to prioritize their security efforts against a constant onslaught of attacks. Unfortunately, few organizations and even fewer security vendors, have knowledge or visibility into advanced memory-based attacks – a fact that is being exploited by attackers every day. We encourage everyone to pay attention to the MITRE list, learn everything you can about memory protection and advanced web application security, and to make sure your security solutions deliver complete protection against today’s most dangerous threats.
Further Resources:
Why Companies Need an Application Memory Firewall
Gartner Market Guide Calls Memory Protection a “Mandatory Capability”
Prediction Series #1: Security systems are blind to memory-based threats
You Must Remember This: Memory-Based Attacks Are the New Battleground
The Memory Attack Battleground
Detecting and Stopping Fileless Attacks
MY TAKE: Memory hacking arises as a go-to tactic to carry out deep, persistent incursions