An application memory firewall detects what other security solutions miss and protects applications and memory from cyber attack
Looking But Not Seeing
It’s the things you can’t see that threaten your network. Your anti-virus solution dutifully scans your disk drives for malicious files and quickly finds any threat it recognizes. But today’s increasingly sophisticated attacks have outsmarted A/V software by not placing malware files on your system the way that’s expected. Instead, fileless malware is inserted into memory where your scanners can’t see it or identify it. Including attacks that occur during runtime, at the process memory level.
Perimeters Filled with Gaps
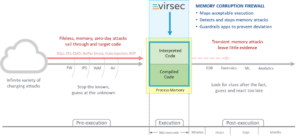
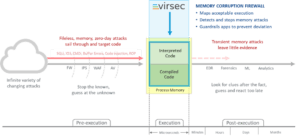
The vast majority of security products focus on the pre-execution stage – identifying and stopping known malware at the network or host perimeter. That approach made sense in the past but today’s perimeter is ill-defined and filled with gaps. Current tools can’t stop malicious activity that hasn’t been seen before. These gaps in knowledge and visibility leave a significant portion of the application stack exposed. Such vulnerabilities have not been lost on attackers.
Lack of Visibility into Memory Usage Makes for Great Opportunity for Hackers
While very few security practitioners understand how process memory works, inventive attackers have found creative ways to exploit the dynamic and transient nature of process memory. Techniques include the use of fileless malware described above, memory corruption, code insertion and other evasive methods. All of these techniques bypass conventional security, can only be identified during runtime, and don’t leave evidence behind after execution.
Advanced memory hacking tools, like EternalBlue and DoublePulsar, that exploit these gaps are now widely available. Attackers frequently modify them to avoid detection and they’ve have become major attack vectors. This has resulted in an endless series of massive attacks like WannaCry, NotPetya, Industroyer, BlackEnergy, Triton and others, causing billions in losses and global disruption.
Manipulating Legitimate Processes to Weaponize at Runtime
When employing traditional malware or fileless techniques, most attacks today have some element that exploits process memory. Assailants can take advantage of host system memory management functions, buffer overflow errors, pointer arithmetic, and uninitialized memory to turn hosted applications into attack weapons. By combining flaws in software and hardware with a series of unvalidated data inputs targeting process memory, attackers corrupt legitimate processes to disable security, leak information, or execute application functions in uncommon ways.
Another common cyber attack strategy is to escalate privileges or control legitimate processes that have high privileges. Privileged processes typically have broad access to memory, can modify system security configuration, add a trusted root certificate, change registry settings, or corrupt memory for specific code sets just as code is being executed. From here, attackers can hijack control over application servers, access databases, or use APIs to connect to other systems.
Critical application processes are at the greatest risk, including those that are running in air-gapped environments. Once skilled malicious hackers have bypassed deficient conventional security, they can setup backdoors, and dwell within networks for extended periods without setting off alarms.
Stopping Memory Exploits with Virsec’s First Application Memory Firewall
As described above, the typical methods of A/V and other security tools are powerless to spot, much less block, these attacks. Virsec takes a completely different approach to filling the void left by these other security solutions.
Virsec brings to the table the industry’s first Application Memory Firewall – a comprehensive set of memory protection capabilities that monitor and secure the critical juncture between applications and runtime process memory. Virsec effectively detects and stops advanced fileless and zero-day techniques including buffer overflow attacks, stack smashing, DLL injections, return-oriented programming (ROP) and ROP gadgets, side channel attacks and corruption of configuration data.
Mapping and Enforcing Proper Execution
Compiled applications may be complex, but they should be predictable. As they are loaded into process memory, fixed assignments are made for memory usage and source-to-target transitions. Virsec’s patented Trusted Execution™ maps all legitimate memory assignments, creating a reference AppMap. If there is any deviation during execution, this is a positive sign of compromise, and Virsec stops the exploit within milliseconds. Because this process is deterministic, Trusted Execution eliminates false positives.
The Application Memory Firewall has a broad range of additional capabilities. Many attacks insert rogue DLLs directly into process memory as applications are executing. Virsec automatically whitelists legitimate DLLs and can instantly detect these changes and restore the correct DLLs. The solution can also detect and stop buffer overflows, stack smashing and a wide range of side-channel attacks.
Take Action Without Guessing Before Damage Is Done
Stopping attacks before they execute relies on prior knowledge, signatures and rules, or guessing. While endpoint protection vendors claim that machine learning, AI or other mysterious tools can predict what’s coming next, this always relies on learning, guesswork and outsmarting equally inventive attackers. As we’ve seen repeatedly, smart attackers can easily fool predictive models and stay several steps ahead.
Stopping attacks after the fact is too late. Endpoint protection and response (EDR) tools claim to learn from attacks so they can be stopped when they reappear. But closing the barn door after the horses have escaped is rarely satisfactory.
Only Virsec stops attacks during execution, in runtime to keep applications on track. The Application Memory Firewall delivers results that are far more effective and nearly instantaneous with unprecedented accuracy. This eliminates the scourge of false positives that undermine many security tools and drown out real attacks.
Virsec does more than detect attacks. Because of its accuracy, Virsec can automatically take surgically precise protection actions within milliseconds to terminate rogue processes, disconnect specific rogue users, restore corrupted libraries, or signal network tools like firewalls or WAFs to disable attackers at the network perimeter.
In short, rather than endlessly chasing an endless stream of unknown and external threats, Virsec focuses on what applications should be doing, how they are actually executing during runtime, down to the memory level, and ensuring they don't do anything else.
Learn more about Virsec's First Application Memory Firewall