The software supply chain is complex, to say the least, with complexity being the enemy of security. Encompassing all the processes and components involved in developing, distributing, and deploying software, supply chains—with an increased range of vulnerabilities—are facing escalating security concerns.
Modern software development heavily relies on third-party components, open-source libraries, and diverse tools, and each of these pieces represents a target for hackers. Additionally, because everything is so tightly connected, a weakness in one part can spread from a single organization to countless others. Not even US federal government agencies are immune, as we saw in the SolarWinds attack.
You don’t want this to happen to you, which is why you need to do everything you can to prevent a software supply chain attack. But in some cases, if things go south for reasons out of your control, you also want to build the resilience necessary to withstand an attack.
Prevention and resilience in the face of imminent software supply chain threats—that’s what we’ll explore in the following sections.
What Is the Software Supply Chain?
The software supply chain is the intricate network of all elements involved in creating and deploying software. That includes all the third-party components, external services, and pre-built software libraries integrated into your systems. Each of these external dependencies introduces potential security risks that you must manage with great care.
The Key Components of the Software Supply Chain
The software supply chain is an ecosystem on its own and a prime example of what diversity means. There’s a stack of elements—necessary for building and deploying any piece of software today—comprising this ecosystem.
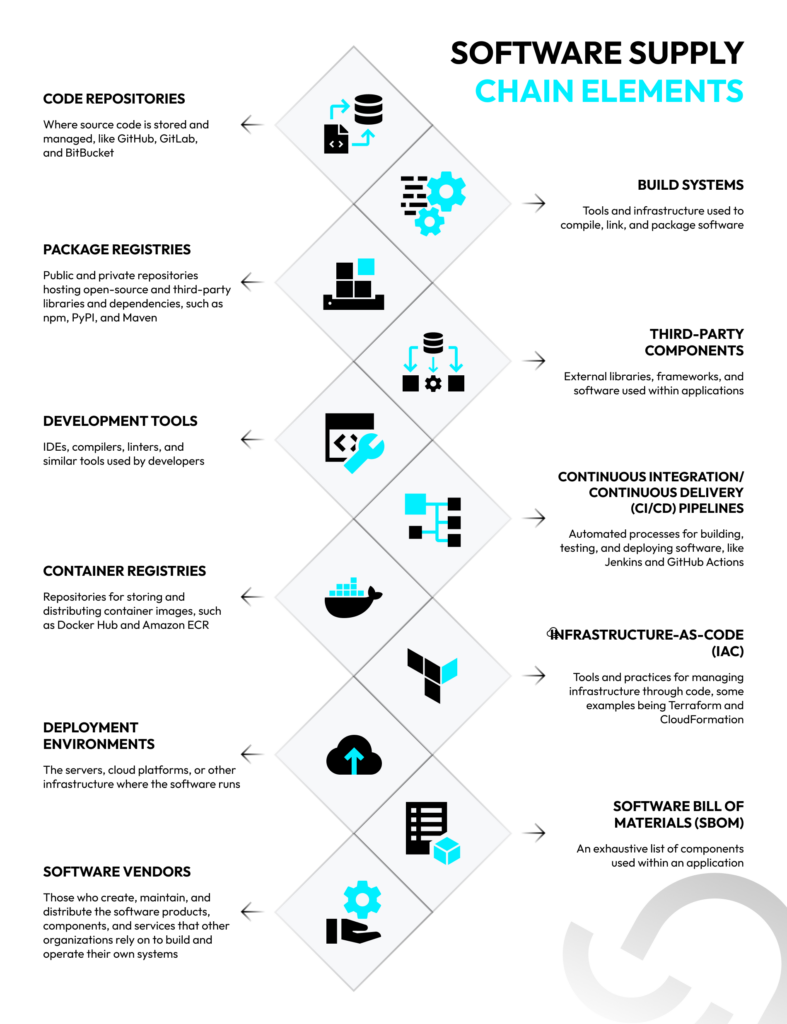
Why Understanding Your Software Supply Chain Is Crucial
Asset visibility brings a full understanding of your software supply chain, which provides the context necessary to manage security risks proactively and prevent cyberattacks. It also supports your compliance efforts and helps you maintain the integrity and trust of your software.
Without software supply chain visibility, you operate in the dark, unaware of the many unavoidable security weaknesses within your environment. Hence, this visibility is critical for actively tracking known vulnerabilities, detecting misconfigurations, assessing the security practices of your vendors, and recognizing signs of tampering or malicious insertions.
Ultimately, software supply chain visibility transforms possible blind spots into a manageable landscape. That’s the only way to reduce the attack surface and hinder threat actors’ ability to exploit hidden vulnerabilities and exposures.
Why Securing the Software Supply Chain is Important in 2025
In June 2024, Blackberry published the results of its cybersecurity research, showing that approximately 75% of the cyberattacks that had happened in the previous 12 months were related to unmanaged software supply chain elements.
Verizon’s “2024 Data Breach Investigations Report” revealed that software supply chain issues were among the top four factors leading to breaches. Furthermore, the World Economic Forum’s “Global Cybersecurity Outlook for 2025” showed that supply chain disruption was the second most concerning cyber risk in the eyes of CISOs and CEOs, right behind ransomware.

So, yes, in 2025, securing the software supply chain should be one of your imperatives. The intricate web of third-party components and open-source software introduces myriad potential entry points for hackers, and a single compromise can cause a terrible fallout.
Increasing Threats in the Software Supply Chain
We don’t have to look further than SolarWinds to fully comprehend the implications of not securing the software supply chain.
SolarWinds was a masterful display of strategy, tactics, and sophistication. The attackers didn’t want to hack into their ultimate targets directly. Instead, they compromised SolarWinds, a widely trusted IT management software provider.
The threat actors inserted a backdoor named “SUNBURST” into the Orion software updates. It lay dormant for about two weeks, after which it began beaconing to command-and-control servers using legitimate-looking SolarWinds infrastructure.
So, when the company’s 18,000 affected customers downloaded what they believed to be legitimate software updates, they were unknowingly installing malware into their systems.
Sunburst was highly elusive malware. It mimicked normal network traffic to blend in and evade detection for months. The malicious code was even digitally signed with SolarWinds’ legitimate certificate to increase its trustworthiness and make detection extremely hard. Besides, it relied on sophisticated techniques to avoid analysis, such as checking for the presence of security tools and virtualized environments.
However, injecting code into an existing application was not the most concerning aspect of the attack. The bigger problem was that the attackers compromised SolarWinds’ software build and release process. This was deeply disturbing because it meant attackers could subvert the very process intended to create secure and trustworthy software.
But how did we even get to the point where a prominent software company like SolarWinds could suffer such a devastating software supply chain attack?
The following information might help you understand our current situation.
About 75% of commercial software relies on open-source components that suffer from known high-risk vulnerabilities. “High-risk vulnerabilities” here refer to actively exploited and remote code execution vulnerabilities, as well as those with documented proof-of-concept exploits.
What’s more, 91% of the commercial codebases include open-source software that’s at least 10 versions behind the latest version. The mean age of the open-source vulnerabilities is more than 2.5 years, and approximately 25% of them are over 10 years old.
Making a bad situation worse, more than half of commercial software has open-source license conflicts, and about one-third lacks a discernible license or includes a customized license.
And this is just open-source software. Imagine the visibility and threat exposure problem you have when you add commercial third-party software to the picture. Consequently, security incidents like SolarWinds are not that difficult to explain.
Regulatory Pressures
The fact that compliance requirements and regulations focus increasingly on software supply chain (in)security confirms the gravity of the problem. Several regulations mandate that organizations manage risks associated with their supply chains:
- GDPR requires organizations to ensure the security of processing, which extends to third-party processors and suppliers handling EU citizens’ data.
- NIST Cybersecurity Framework and NIST 800-161 outline processes for identifying, assessing, responding to, and monitoring risks throughout the supply chain, including software vendors and components.
- ISO 27001 requires organizations to establish, implement, maintain, and continually improve their management of risks associated with third parties and the supply chain.
- NIS2 mandates a coordinated security risk assessment of the software supply chains across the EU.
- DFARS in the US includes specific cybersecurity requirements for defense contractors, which often flow down to subcontractors in their supply chain.
- PCI DSS includes requirements for managing third-party service providers who can impact the security of cardholders’ data.
If organizations fail to meet compliance requirements, they can face regulatory fines (as mandated by GDPR, NIST frameworks, and ISO 27001), costs from legal fees, and potential compensation to affected parties.
Not even tech giants and big companies are exempt from facing the music for non-compliance:
- Meta (Facebook) has paid multiple massive fines for GDPR violations, including an insufficient legal basis for data processing and mishandling of user data. One of the fines exceeded €1 billion.
- In October 2024, LinkedIn was fined €310 million by the Irish Data Protection Commission (DPC) for infringement of GDPR.
- Amazon was penalized with €746 million in 2021 by Luxembourg’s data protection authority for non-compliance with general data processing principles related to its advertising practices.
- Montefiore Medical Center agreed to pay $4.75 million to the U.S. Department of Health and Human Services (HHS) in February 2024 for a lack of safeguards to protect electronic protected health information (ePHI).
The Risks of Not Securing Your Software Supply Chain
Failing to secure the software supply chain carries legal, financial, and reputational risks. We’ve already touched on legal and, partially, financial. Let’s explore the subject further.
Data Breaches and Financial Losses
A supply chain breach can lead to the exposure of sensitive customer data if a compromised third-party component or vendor has access to it. Data exposure directly erodes customer trust, as people lose confidence in the organization’s ability to protect their information.

The loss of trust, then, can easily translate into customer churn, difficulty in acquiring new customers, and ultimately, a loss of business and damage to the organization’s reputation, potentially for the long term. If accompanied by negative news coverage and public scrutiny, a breach can permanently damage an organization’s image.
In addition to the financial consequences mentioned in the previous section, incident response and recovery efforts can also incur major direct costs, especially if you lack strong ransomware protection. As far as indirect costs go, lost revenue and lower stock value due to operational disruptions are common problems in the aftermath of major breaches.
Service Interruptions and Operational Delays
A breach or failure within the software supply chain can introduce malicious code, as we saw in the SolarWinds example, or compromise critical components. That can lead to system instability, crashes, shutdowns, and unavailable services.
Downtime suffered during breaches directly affects daily operations. For starters, it prevents employees from performing their tasks, slashing productivity. But that’s not the biggest problem. Frustrated and dissatisfied customers losing trust and migrating to competitors due to unreliable service is a much bigger problem that can ruin businesses.
How to Secure the Software Supply Chain
There’s no other way to secure the software supply chain but through continuous visibility, rigorous vetting of components, secure development practices, and robust monitoring throughout the software lifecycle.
Comprehensive Risk Assessment
Visibility into the complex web of third-party components, open-source libraries, vendors, and services is the sine qua non of a strong security posture. And to gain visibility, you must clearly map the dependencies. The map you get acts as a blueprint, revealing critical junctures where vulnerabilities could be introduced or exploited.
Now, when the software supply chain is in question, visibility assumes clear software provenance—the ability to trace the origin of each element. Software provenance allows you to identify innate security weaknesses within the software supply chain ecosystem, such as common open-source software vulnerabilities, and mitigate them to preclude attackers from reaching those system entry points. In other words, it ultimately enables targeted security measures and informed risk management decisions.
Once you map your software supply chain, the next step is risk assessment. Its objective is to allocate efforts, resources, and time effectively. That means analyzing components and vendors based on factors like the criticality of their function, the sensitivity of the data they handle, their known vulnerability history, their security practices, and the impact a compromise could have on your organization.
When you know the most vulnerable and impactful parts of your supply chain—those that would cause the most severe business disruption, data loss, or reputational damage if breached—you can give them the urgent attention they require. For instance, instead of increasing the risk by relying on long patching cycles, you can apply vulnerability mitigation off the bat.
Vendor Management and Monitoring
Long gone are the days of reactive security being the way to do things. Today, organizations must adopt a proactive approach to third-party risk. How? By continuously evaluating their vendors’ security posture throughout their collaboration, because risk assessment is not a one-and-done deal.
Clear security requirements, straightforward contractual obligations, and regular assessments (questionnaires, audits, or penetration tests) should all be part of the collaboration. Diligent monitoring of vendor security guarantees the timely identification and remediation of weaknesses that are introducing risk in your environment.
To achieve the best results, use real-time monitoring solutions. These tools give you ongoing visibility, allowing you to quickly spot unexpected changes in how third-party components behave. With this information, you can stop suspicious or harmful activities immediately. Even if an attack occurs, you can reduce its impact and prevent a full-scale security breach.

Implementing Secure Development Practices
To address the problem at its root, vendors must adopt secure coding practices. One way to enforce these best practices is to train developers to write code that inherently prevents common vulnerabilities, such as SQL injection, cross-site scripting, and buffer overflows.
This proactive approach—focusing on security from the initial stages of development to the end of the SDLC (software development life cycle)—guarantees a minimized likelihood of exploitable weaknesses in the software supply chain.
In addition to secure coding, organizations must implement regular code audits and vulnerability scanning for all the software components and services integrated into their systems. That includes static (SAST) and dynamic (DAST) analysis tools to identify security flaws and misconfigurations.
Continuous monitoring of external dependencies for known vulnerabilities and promptly addressing any findings allows you to maintain a secure software supply chain that can withstand vulnerability exploitation by malicious actors.
Virsec’s Approach to Securing the Software Supply Chain
Virsec offers an integrated solution that unifies exposure and vulnerability management in one security platform—OTTOGUARD.AI. And the software supply chain is one of the aspects the platform was purpose-built to protect.
How Virsec Combines Exposure Management and Vulnerability Management
OTTOGUARD.AI heightens security by looking across the entire code in your environment at runtime and providing full workload visibility. It establishes software provenance and precisely maps the intended execution of all the code in your environment. Based on these insights, the platform creates a baseline of trusted behavior.
This baseline further enables OTTOGUARD.AI to identify a broad spectrum of exposures—from known vulnerabilities to misconfigurations—since they all force, in one way or another, your systems and software to deviate from the established baseline at runtime. This same quality allows OTTOGUARD.AI to stop threats in real time, preventing them from gaining a foothold and moving laterally.
What this means is that the platform effectively mitigates security issues without relying on anything external, whether “external” means patching or human intervention. This means that OTTOGUARD.AI is equally effective against both CVEs and zero days (unknown vulnerabilities) because its protection is independent of and, hence, indifferent toward available threat knowledge and patches.
Benefits of Virsec’s Software Supply Chain Security
OTTOGUARD.AI’s approach yields tremendous practical results:
- Fast, real-time threat detection
- Zero-dwell time
- Patchless mitigation, leading virtually to zero MTTR (time to remediate), i.e., immediate remediation independent of patching
- Protection from zero-day, malware, and ransomware attacks
- Reduced risk exposure
- Minimized attack surface
Securing the Software Supply Chain with Virsec
The countless threats targeting the software supply chain necessitate a fundamental shift in the approach to security. As reliance on complex third-party and open-source dependencies grows, so does the likelihood of a compromise coming from the software supply chain.
What is to do?
Prioritize continuous visibility, proactive risk assessment, vendor management, and secure development practices. These can help you build the necessary resilience to prevent attacks and minimize the devastating consequences of a breach coming from the software supply chain.
A security solution that offers real-time threat detection and patchless mitigation, like Virsec’s OTTOGUARD.AI, represents a giant step forward in securing this vital yet often vulnerable link in the modern digital ecosystem.
Ready to fortify your software supply chain? Book a demo to see OTTOGUARD.AI in action.
FAQs
The software supply chain encompasses all third-party components, services, and software integrated into your environment.
Virtually all of the OWASP Top 10 can be traced back to software supply chain issues, because modern applications are assembled from third-party components, rather than built from scratch.
Here is the latest Top 10 list:
- A01: Broken Access Control: Users can access data or perform actions they shouldn’t be allowed to.
- A02: Cryptographic Failures: Sensitive data is exposed due to weak or missing encryption.
- A03: Injection: Untrusted data is sent to a code interpreter as part of a command.
- A04: Insecure Design: Security was not a core part of the application’s original architecture.
- A05: Security Misconfiguration: Insecure default settings or improperly configured permissions are left open.
- A06: Vulnerable and Outdated Components: The application uses components with known security flaws.
- A07: Identification and Authentication Failures: Weaknesses in login processes allow attackers to impersonate legitimate users.
- A08: Software and Data Integrity Failures: Trusting software or data without verifying whether someone has tampered with them.
- A09: Security Logging & Monitoring Failures: Insufficient logging and visibility to detect and respond to attacks.
- A10: Server-Side Request Forgery (SSRF): Forcing the server to make a malicious request to a destination the attacker chooses.
Here are the most common software supply chain attacks:
- Dependency confusion: An attacker tricks a build tool into downloading a malicious public package that shares the same name as an internal, private one.
- Typosquatting (brandjacking): A malicious package is published with a name that is a common misspelling of a popular library to trick developers into installing it by mistake.
- CI/CD pipeline poisoning: Attackers compromise the automated build and deployment process itself to inject malicious code or steal credentials.
- Known Vulnerability Exploitation: An attacker targets an application by exploiting a publicly known vulnerability (CVE) in one of its unpatched third-party dependencies.
Repository compromise: An attacker gains direct access to a code repository to inject malicious code or replace legitimate software artifacts with compromised versions.
Software supply chain security is the cybersecurity discipline that’s concerned exclusively with making sure that every piece of outside code and every tool you use to build and deliver your software is safe and has not been tampered with.
Securing the software supply chain in 2025 is crucial due to more and more sophisticated attacks, like SolarWinds, targeting numerous vulnerabilities.
Secure your software supply chain through continuous visibility, rigorous vetting, secure development, robust monitoring, and patchless exposure mitigation.
Securing the open-source software supply chain requires:
- A continuous process of identifying all dependencies
- Analyzing them for vulnerabilities
- Enforcing policies to block risky components
- Actively monitoring for emerging threats throughout the software life cycle.




